The 10 most critical API security risks - Part 8: Injection

Matthias Biehl
Posted on March 17, 2020
The recently published “OWASP API security top 10” report analyzes the anti-patterns that lead to vulnerabilities and security risks in APIs. In this 10 part series, we introduce these API anti-patterns. Every API professional should know about these anti-patterns.
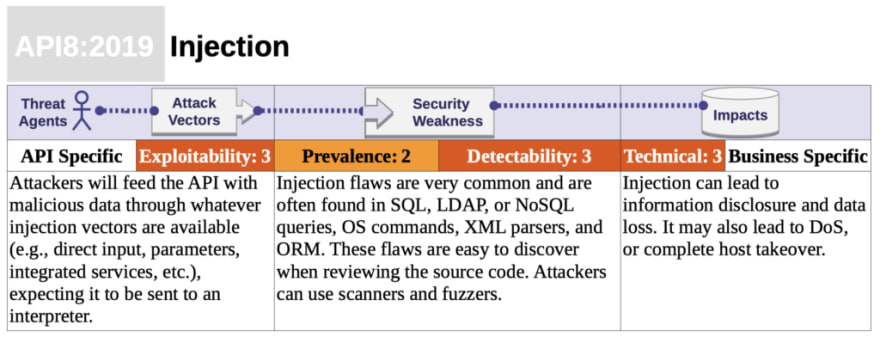
Injection from the OWASP API security paperAPI security anti-pattern for Injection
Injection flaws, such as SQL, NoSQL, Command Injection, etc., occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s malicious data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
Want to learn more?
- Part 1 Broken Object Level Authorization
- Part 2 Broken User Authentication
- Part 3 Excessive Data Exposure
- Part 4 Lack of Resources & Rate Limiting
- Part 5 Broken Function Level Authorization
- Part 6 Mass Assignment
- Part 7 Security Misconfiguration
- Part 8 Injection
Check out the complete OWASP API security paper. To secure access to your APIs, learn more about the OAuth in the OAuth Book, or the OAuth Course. To provide and use identity data in apps and APIs, learn more about OpenID Connect in the OpenID Connect Book, or the OpenID Connect Course.

Posted on March 17, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.