How the Blockchain secures data using Cryptographic hash function

Judith Ogar
Posted on March 17, 2023

Prerequisite
Basic understanding of how the blockchain works
Basic understanding of how the blockchain works
What is cryptography?
What is the Hash function?
How Blockchain uses the cryptographic hash function.
What is cryptography
Cryptography is formed from the words kryptos meaning “hidden, secret” and graphien meaning “ to study, write”.
Cryptography simply means to securely write a piece of information or data so it cannot be accessed by a third party. This information is written through a process called encryption which means converting a readable/plain text into an unreadable form, and can only be accessed by the intended recipient through another process called decryption which means converting from an unreadable form back to a readable form.
Symmetric and Asymmetric are the types of cryptography. They both uses keys to secure information.
What is the hash function?
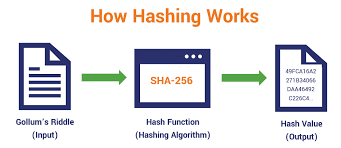
It is a function that takes in a random value as input and gives back a fixed length value as output. The hash function is a type of cryptography.
What's Interesting about the Hash function ?:
- The same input value will always give the same output value no matter how many times the function takes in the input. This feature makes the hash function Deterministic.
“1234” => hashfunctions = 64ec88ca00b268e5ba1a35678a1b5316d212f4f366b2477232534a8aeca37f3c
“1234” => hashfunctions = 64ec88ca00b268e5ba1a35678a1b5316d212f4f366b2477232534a8aeca37f3c
2.It is so sensitive that even a slight change in the input will result in a completely different output. This feature gives the hash function the Avalanche effect.
1234 => hashfunctions = 64ec88ca00b268e5ba1a35678a1b5316d212f4f366b2477232534a8aeca37f3c
1233 => hashfunctions = a8119595d77342cc73c93697a7f70920d3f4ded5d458e31907607e997ff76868
3.It is impossible to guess what was the input value just from looking at the output. The output value cannot be reversed back to give the input.
This is similar to how once you make a milkshake or smoothie by blending oranges, bananas, and pineapple in a blender, it is difficult to change the liquid back to the original ingredients(bananas, oranges, and pineapple).
How blockchain uses the cryptographic hash function
One of the peculiarities of the blockchain is its ability to safely protect data stored on it from being altered or tampered with. The blockchain is able to keep this data securely by encrypting it using cryptography and hashing.
The blockchain uses the Asymmetric cryptography type also known as Public Key cryptography (PCK) for its data encryption and decryption. The PCK uses unique keys to store information. This unique keys the PCK used for securing and storing information are public and private keys which are also available on every blockchain wallet.
when transaction are sent on the blockchain, the details of that transaction forms a hash code that will be sent alongside the public key of the sender, to the receiver of that transaction. Remember what I said about the hash function been deterministic and having Avalanche effect?. Now, the sent transaction must be verified before it is added to a block. During the verification process, if any change has been made to the details of that transaction, the already generated hash code changes to a completely new hash.
once this happens, it proofs that the transaction has been tampered with. Which will make the transaction to be rejected.
In conclusion, the blockchain uses the cryptographic hash function to secure data in encrypted form which also makes the data immutable.

Posted on March 17, 2023
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.