Andrea Scarpino
Posted on May 26, 2021
A week ago, I blogged about a vulnerability in a platform that would allow anyone to download users’ amortisation schedules. This was a critical issue, but it wasn’t really exploitable in the wild as it included a part where you had to guess the name of the document to download.
I no longer trust that platform so I went to their website to remove my loan data from it, but apparently this isn’t possibile via the UI.
I also opened a ticket on their support platform to request removal and they replied that it isn’t possible.
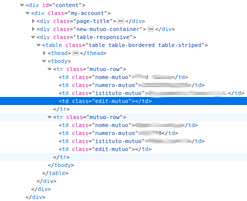
So I went to their website with the intention of replacing the data with a fake one… but there was no longer an edit button!
I’m sure it was there before and in fact the code also confirms that it was there:
However, the platform is based on Magento and so, starting from the current URL, we can easily guess the edit URL, e.g. https://<host>/anagraficamutui/mutuo/edit/id/<n>.
Let’s try 1… bingo!
But wait a minute… this isn’t my loan! Luckily it’s just a demo entry put in by some developer:
Even though it’s a dummy page, we can already see the details of the loan such as the (hopefully) fake IBAN, or the loan total and loan number and even the bank contact person name and email address.
And now take a look at this: if I try to access that page in private mode, then I get the login page. All (almost) well, right?
Nope. Let’s try the same request via curl:
$ curl -s https://<host>/anagraficamutui/edit/id/1 | grep banca
<input type="text" name="istituto_credito" id="istituto_credito" value="banca acme" title="Nome istituto" class="input-text istituto_credito required-entry" />
$ curl -s https://<host>/anagraficamutui/edit/id/1 | grep NL75
<input type="text" name="iban" id="iban" value="NL75xxxxxxxxx" title="Iban" class="input-text iban required-entry validate-iban validate-length maximum-length-27 validate-alphanum" />
Wait a minute, what’s going on?
Well, it turns out that the page sets the location header to redirect you to the login page when there’s no cookie, otherwise it prints the HTML page!
$ curl -s https://<host>/anagraficamutui/edit/id/1 -I | grep location
location: https://<host>/customer/account/login/
Oh-no!
Conclusion
Data from 5723 loans could have been exposed by accessing a specific URL. Details such as IBAN, loan number, loan total and the bank account contact person could have been used to perform spear phishing attacks.
I reported this privacy flaw to the CSIRT Italia and the platform’s DPO. The issue has been solved after 2 days, but I still haven’t heard from them.

Posted on May 26, 2021
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.