PCI DSS Requirements and Tips on Compliance

Evgeniy Altynpara
Posted on December 4, 2020

Modern entrepreneurs tend to digitize their businesses in the pursuit of new clients and distribution channels. Retail stores and physical chains rapidly fade away, while websites and mobile apps steadily take their positions. According to Statista, 54 percent of overall e-commerce sales will be done via mobile devices. This fact highlights the popularity of mobile digital services among customers. However, the platform should be guarded with up-to-date technologies and protocols to ensure customers’ safety.
PCI DSS is one of the main standards that protect users’ credit card data. In this post, we’ll discuss the PCI DSS standard, its requirements, and how it works.
What is PCI DSS?
PCI DSS stands for Payment Card Industry Data Security Standard. The standard appeared in 2004 after the establishment of PCI SSC (Payment Card Industry Security Standard Council). PCI DSS early versions declared basic requirements to all parties that transmitted, processed, or performed any other manipulations over the sensitive credit card data. Later, with the rising popularity of digital transactions, the standard became more demanding to safeguard all users that make online transactions.
Today, PCI DSS is a default requirement for all software products that manage credit card data. Non-compliance with the standard may lead to severe vulnerabilities and data leaks. If that’s the case, the company may be fined for $5,000 - $100,000 per month. The amount of fines depends on the business size and the type of protocol violation.
Four Levels of PCI Compliance
Even though PCI DSS is a unified protocol for all software products, its requirements may differ. They depend on the number of transactions performed by the app and the number of users. PCI SSC drew up a list of compliance levels that explains the requirements to all responsible parties.
Let’s get a closer look at each of these levels:
Level 1. The first level sets requirements for major software products that process more than 6 million Visa or Mastercard transactions or 2.5 million American Express transactions per year. Besides, companies that had non-compliance issues before have to comply with level 1 requirements too. Requirements include a yearly audit on compliance conducted by a Qualified Security Accessor from PCI SSC or by the Internal Security Assessor (a PCI DSS certified internal employee). The officer draws up a report according to the official PCI DSS template. On top of that, the company should perform network scans each quarter.
Level 2. This level sets requirements for companies that process between 1 and 6 million transactions per year. Businesses are required to perform an annual PCI DSS assessment and fill in the self-assessment questionnaire.
Level 3. Applies to companies that process between 20,000 and 1 million transactions per year. The company should fill in a PCI DSS compliance questionnaire. The ASV scanning is optional.
Level 4. It’s the lowest compliance level for companies that process less than 20,000 transactions per year. Employees should fill in the relevant questionnaire. ASV scanning may also be required.
PCI DSS Requirements
To be PCI DSS compliant, companies should pay a lot of attention to technical and organizational details. The latest version of the standard has 12 main requirements that ensure the cardholder data safety. These requirements include the usage of up-to-date security protocols, control of physical access to data storages, maintaining an information security policy for employees, and more. Let’s single out each of these requirements.
Setting up and maintaining a firewall
PCI DSS defines the firewall as equipment that sits between the payment system and the Internet. To set up a firewall that complies with minimal PCI DSS requirements, you have to follow these steps:
- Change default passwords to strong ones
- Restrict all the traffic to the payment system to only what is necessary
- Avoid “Allow any” rules in firewall settings
- Set “Deny all” rules for unauthorized traffic
- Allow only “established” connections to your network
- Turn on intrusion detection is possible
- Turn on notifications
- Turn on NAT to hide internal addresses
- Keep firewall up-to-date
However, these requirements concern only small businesses. Large companies should hire network professionals for more advanced firewall settings.
Change default passwords
Networks with default credentials are the easiest targets for blackhats. Change default passwords for firewalls, Wi-Fi networks, and other access points. “Admin - admin” is the first combination that the hacker will enter into the login form. Besides, it’s important to change your passwords frequently. According to PCI DSS regulations, passwords should be reset every 90 days.
Take care of cardholder data
The threat often comes from unexpected sources. Consider all possible risks and take action on their elimination. Thus, data should be kept under the password and encrypted with cryptographic keys. If the fraudster accesses the data, it will be unreadable without the means of decryption.
However, the most reasonable idea is to avoid storing sensitive data unless it’s completely necessary. The company that owns a retail app, for example, doesn’t need to store payment details. It can use the services of trustworthy third-party payment gateways like Stripe, PayPal, or Braintree. Even though the liability for data leaks still lies with the app owner, these services have an outstanding security level. Moreover, with third-party gateways, companies can cut expenses on the custom payment system development.
Data encryption in public networks
Blackhats can intercept sensitive data during transmission over public networks. According to PCI DSS standards, sensitive data should be transmitted over the channels secured with IPsec or TLS protocols, depending on the type of transmitted data. When dealing with wireless networks, the WPA2 security protocol can ensure the appropriate security level.
Malware protection and antivirus updates
PCI DSS declares strict requirements for the usage of antivirus software. All devices that may be a fall victim to malware should have antivirus software. It analyzes downloaded files for possible threats.
It’s important to track the antivirus uptime and log all shutdowns. The antivirus should operate continuously, and there should be a serious purpose to deactivate it. During the annual assessment, PCI DSS officers check the logs of antivirus runtime and may penalize the company for excessive antivirus downtime.
Security of all systems and applications
The applications published by the company should have the same security level as their internal networks have. During and after the development, QA teams should conduct testing of the app to find and remove security breaches. The app should install all security updates automatically.
Secure coding methods are part and parcel of PCI DSS compliant software. Developers should know how to treat the memory that contains sensitive data. It’s also a good option to hire whitehats that can detect the vulnerabilities in your software in return for a reward. It’s a common practice among large companies like Google, Amazon, and others.
Restricted access to sensitive data
One of the PCI DSS requirements is restricted access to sensitive data. It should be accessible only to authorized personnel. At this point, the company should come up with different access levels for each employee that works with credit card data. The system should verify the identity when the employee accesses the information and automatically log off the devices connected to the database after a certain period of time.
Authorized access to system components
As well as it was with antiviruses, the software should also track the access to all individuals that worked with sensitive data. That’s why companies assign an ID to each employee that has access to cardholder data. Whenever the employee gains access to the data, their ID and current time and date will be recorded into the database.
A PCI DSS also requires to delete inactive accounts with critical data access within 90 days. IDs help admins to track the date when users logged in their accounts and delete inactive ones.
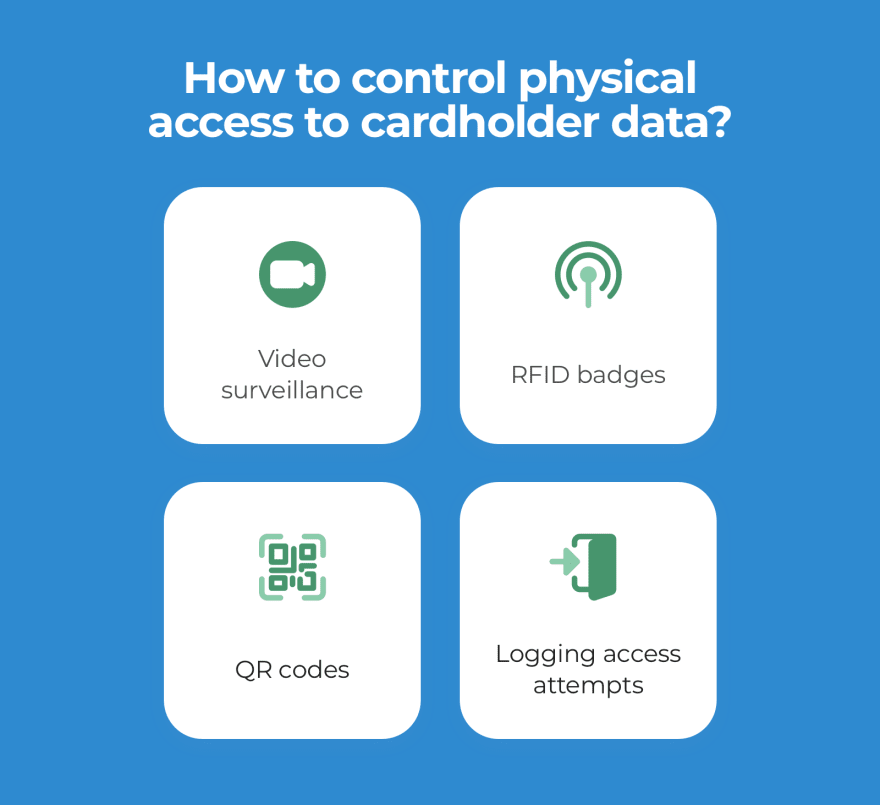
Restricted physical access to cardholder data
With physical access to the storage, fraudsters can copy sensitive data on any removable storage device. PCI DSS regulations require video surveillance and entry control devices in the enterprise data warehouse. Copies of video surveillance files should be stored for three months minimum.
Besides, it’s crucial to identify employees and visitors that enter data centers with sensitive data. As we’ve mentioned before, it’s a good idea to assign an ID badge to every employee. Thus they can scan their badges with the help of an RFID module or QR code and gain access to the storage. If you need third-parties to enter the storage (for hardware maintenance, for example), a responsible employee should escort outsiders all the time inside the storage.
Network access monitoring
User activity monitoring is a big step forward in preventing data leaks. With a properly adjusted logging system, you can easily detect individuals that accessed the network and track their actions inside the system.
PCI DSS officers check the system for the following audit features:
- Tracking access to credit card data
- Logging all actions with admin or root rights
- Attempts to enter wrong credentials
- All actions performed on system-level objects
Security system testing
Every software should be tested before the release. To comply with PCI DSS, the software should be tested for vulnerabilities and bugs after each update. To ensure that the software is safe to use, companies hire the services of Approved Scanning Vendor (ASV) to test their software for vulnerabilities. When choosing an ASV, it’s important to make sure that PCI SCC licensed the vendor.
Maintain security policies
A human factor often becomes a reason for data leaks. Hackers use social engineering techniques to extract information from employees. That’s why companies should deliver security policies to their employees and inform them about any changes. Besides, PCI DSS requirements include an annual risk assessment that is meant to identify possible security threats inside the company and eliminate them in the future.
Wrapping up
PCI DSS policies set strict requirements for software products that process credit card data. Due to these regulations, users can be sure that their data is safe and won’t fall into third-parties’ hands. However, PCI DSS compliance is a complicated process for companies. For small businesses, it makes sense to think of alternative solutions like third-party payment gateways.

Posted on December 4, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.