Zachary Wilson
Posted on July 1, 2022

It was recommended by a colleague that i might enjoy delving a bit into Ansible and suggested i check out the Complete DevOps Ansible Automation Training instructed by Imran Afzal. I can already see why this course was recommended, the instructor is very knowledgeable and easy to follow.
In the course, however, he explains how to create a test environment using virtualization software from your local machine, which is easily going to hit the needs of the wider audience. In the interest of the... thinner audience (?), i decided i'd build mine in AWS.
Everything here is using the AWS Management Console and commonly-known IT tools which are easily downloaded and installed.
First thing after logging into the AWS Management Console is to create an EC2 Security Group, which is really just an odd name for server-level firewall (my 2¢). "But we haven't created our EC2 instances yet," you ask? This is true, and you'll see why this is first on my list (i hope) as i continue.
I gave my Security Group a descriptive name and then configured the only inbound rule needed, SSH over port 22 from any IPv4 address. If you're doing this from home, i recommend using My IP instead as this adds a significant layer of security to your environment without too much hassle. I'm accessing this instance from different networks, so i went this route.
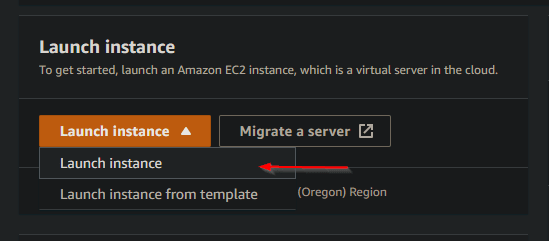
Once the Security Group is created, it's back to the EC2 dashboard to configure the first instance for launch.
Exciting, no?
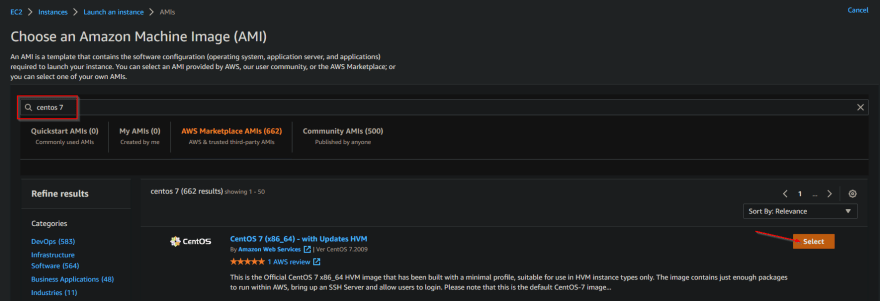
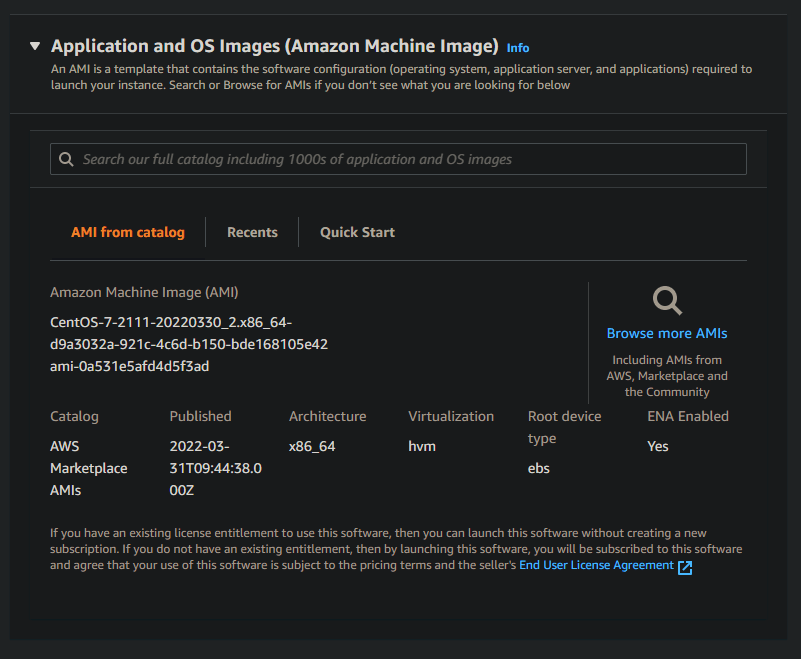
It's time to choose a descriptive name and an OS for my Ansible control node. Instructor Afzal installs CentOS on Oracle VirtualBox VMs in his course, so i chose to install CentOS as well. This wasn't visible in the AWS Quick Start list so i clicked 'Browse more AMIs' (Amazon Machine Image).
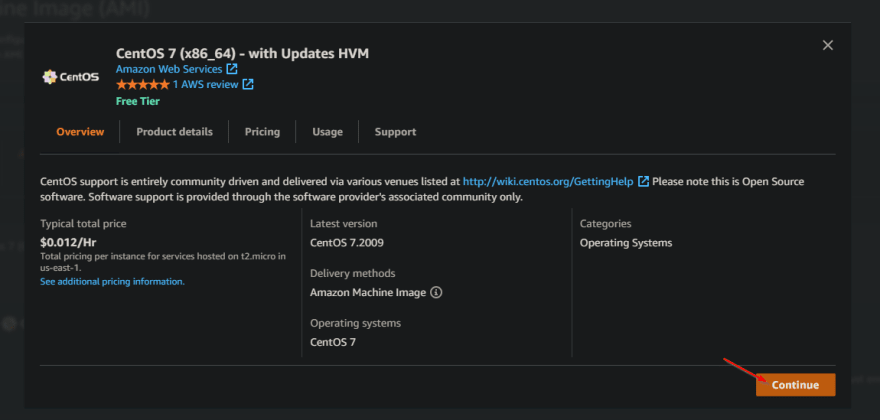
A quick search for 'CentOS 7' and we have results.
After the steps to select the OS it's time to choose the Instance type, basically how much hardware-level performance do you want to pay for? I chose t2.small per the instructor's recommendations for the VirtualBox VMs (1 vCPU, 2GB memory). The math comes out to $8.64 USD per month if this instance runs 24/7 in a 30-day month (if you're curious).
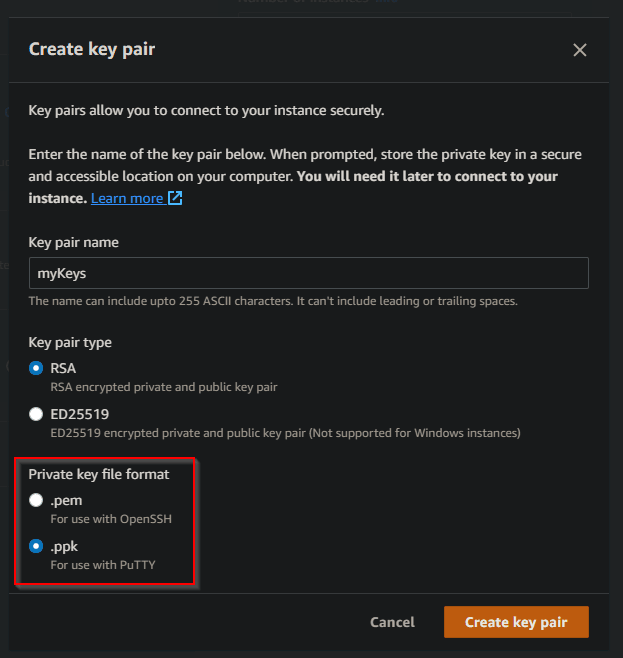
When asked for a key pair i chose to create new.
This is an asymmetric encryption method that i'll use to log into my instance once it's ready. The public key is stored on the instance, the private key i keep, well... private.
I gave my key pair a not-so-descriptive name this time around, left RSA selected as the encryption protocol and then chose .ppk as the key file format. This is because i'm connecting from a Windows client and will be using PuTTY for this purpose.
⚠️ You should be prompted to download your .ppk file! Be sure to do so as this is your only chance.
Onto the Network settings, this is where having already built your Security Group comes in handy - just Select existing security group, choose the group you created and we're done with this section. Otherwise you're building out traffic rules in a poorly-suggested Security Group name (again, my 2¢) in the midst of doing all these other steps.
My next step is to configure storage for the root drive of my instance. I also want to configure some Advanced details.
There's a bit to do in Advanced details, i couldn't grab it all in a concise screenshot and didn't want to edit anything together to avoid possible confusion.
- change Hostname type to Resource name
- change Shutdown behavior to Stop
- change Termination protection to Enable
- and change Tenancy to Shared
The console offers explanations of each setting, so i won't go into those here. Next it's just confirmation your instance is configured correctly and launch.
For my client machine, i built a replica of the control node above only changing the hostname to something identifiable, like Client1. Easy enough, now i've got 2 almost identical CentOS 7 AWS instances.
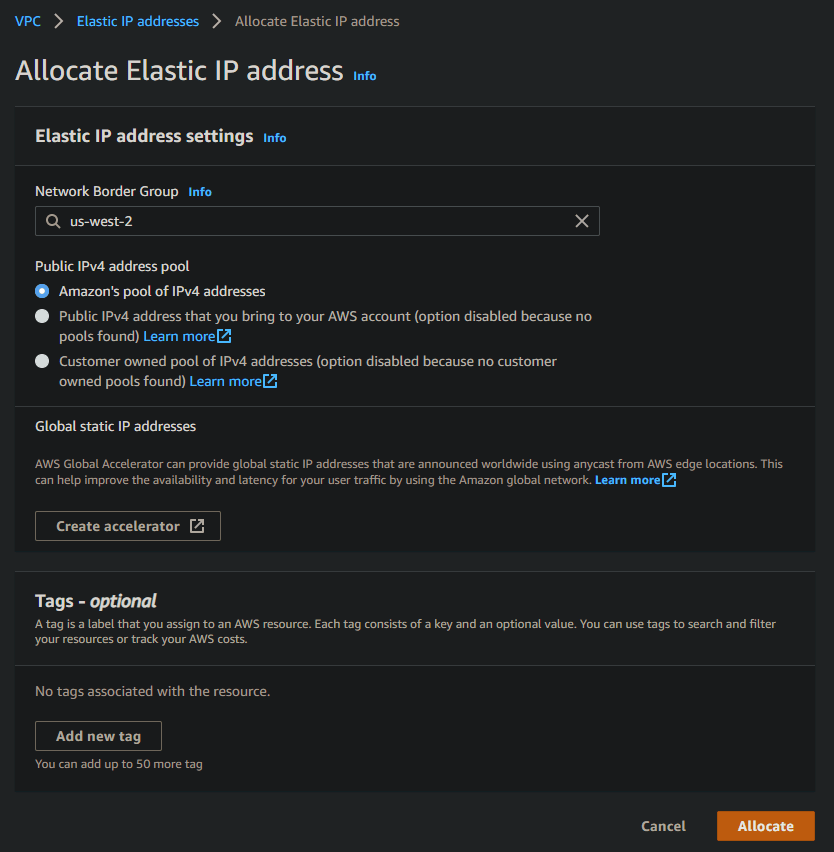
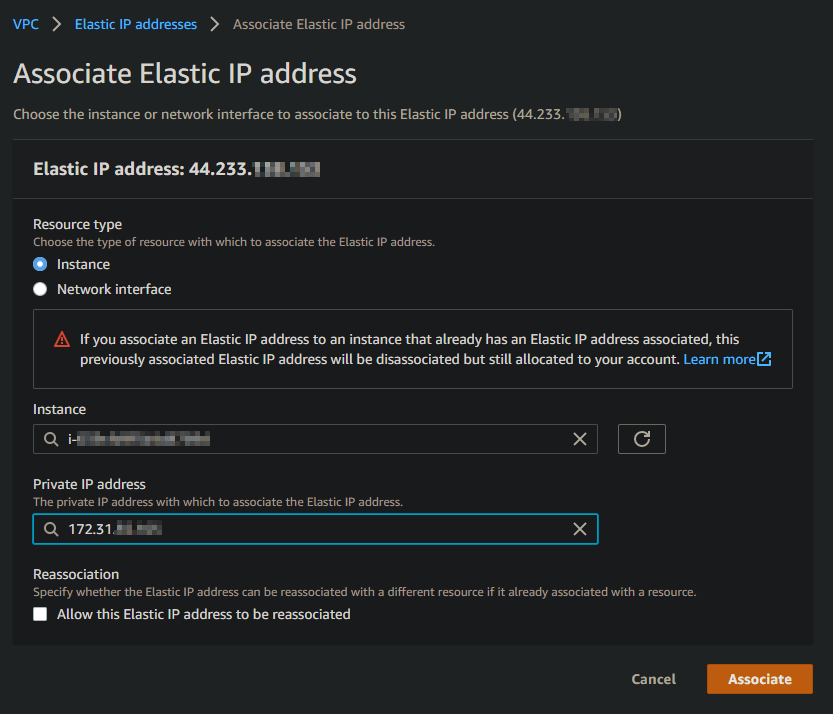
Now to connect to my control node, I allocate an Elastic IP to my VPC from Amazon's pool of IPv4 addresses and associate it with my control node instance.
At this point i was prompted that i might want to associate an Internet gateway with my VPC to connect my private IPs in the VPC to the internet, and this is correct. So i created an Internet gateway and confirmed connectivity to my control node from my local machine.
Now i'm ready to remote into my instance (whew!). As i mentioned, i'll be using PuTTY for this. If you've used PuTTY before (or even if not), this is pretty straightforward for the most part: enter the Elastic IP address, confirm port 22 and SSH connection type. Then scroll down to the Connection category and select Auth.
Here i browsed for my .ppk file that i saved when i created my key pair for my instances.
💡 Tip: Saving this PuTTY configuration will make things easier later on.
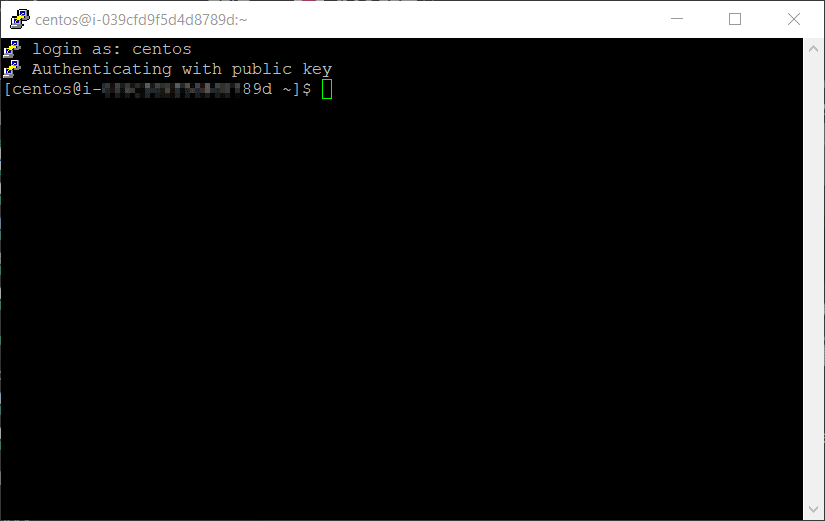
With this i was able to log into my control node for the first time using default OS credentials and authenticating to the public key on the instance.
Next i installed Ansible and confirmed python is installed on my instance (as it should be) using the following commands:
yum install epel-release
yum install ansible ansible-doc
python --version
If python's not installed:
yum install python -y
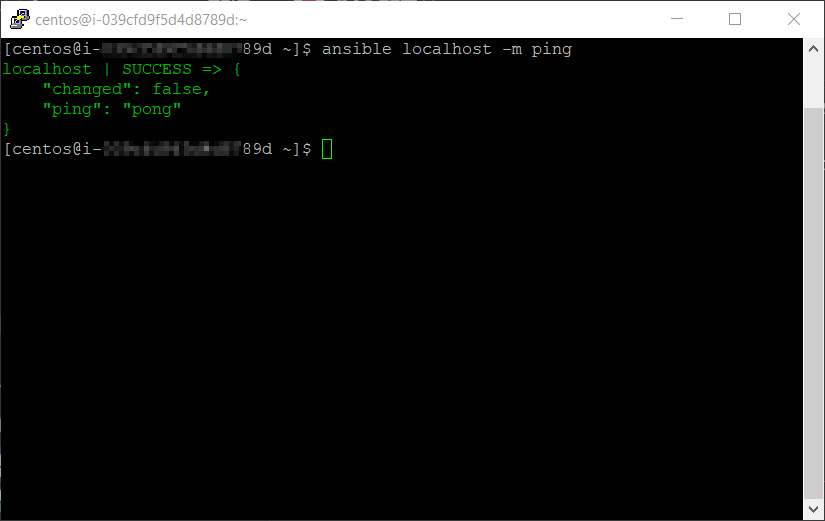
I can confirm the Ansible install a couple ways; here i chose to utilize Ansible's ping module on the localhost. Of course if you prefer you could always run
rpm -qa | grep ansible
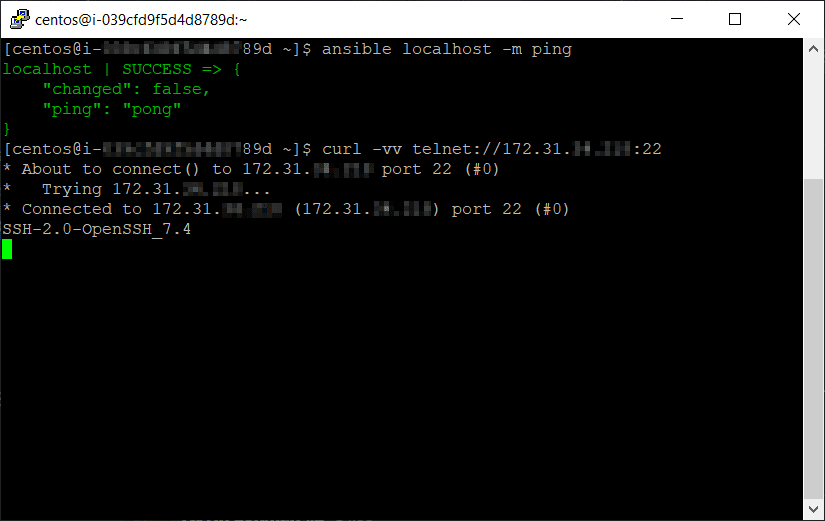
Everything is good so far with the control node, so now i confirm that port 22 is open on the client instance using a nifty trick i didn't know existed until this project.
curl -vv telnet://DestinationServer:22
Fabulous! We're closer to connecting to the Ansible client instance. To remote into the client, i need to use the private key from the instance key pair.
But i downloaded that in .ppk format for PuTTY, not .pem for OpenSSH! And i can't redownload it!!
PuTTYgen to the rescue! The PuTTYgen module is part of the default install of the PuTTY utility and can convert your .ppk to a .pem in no time. I followed the instructions here.
Now that i have my private key in OpenSSH format, i just need to drop it on my control node instance. Since i'm using a Windows client, i'll use WinSCP for this.
💡 Tip: If you saved your PuTTY connection configuration earlier, WinSCP will detect and offer to migrate your configuration and private key file. How easy is that?
Instructions for transferring files to a Linux host with WinSCP
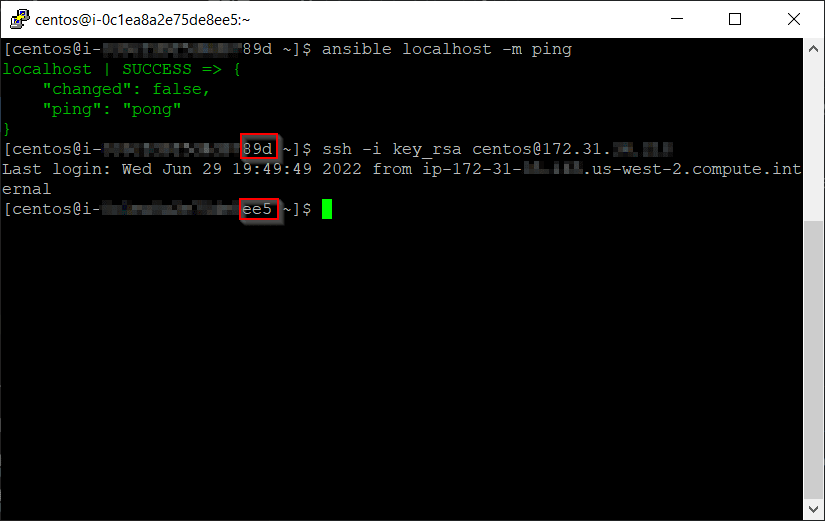
The private key is on the control instance in the correct format, nothin' left to do but SSH:
ssh -i dir/keyName user@hostAddress
Here you can see the instance number changed indicating i'm now working in a remote shell from the control node to the client instance.
Configuring Ansible on the control node to communicate with the client instance requires 2 final steps.
- Add the hostname/IP of the client host to the Ansible hosts file found in etc/ansible/hosts
- Add the private key to ~/.ssh
ssh-agent bash
ssh-add ~/.ssh/keyName
Now for the confirmation...
Ansible is now communicating with the client instance!

Posted on July 1, 2022
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.