
ayy lmao
Posted on January 15, 2021
Task 9: Training
This challenge mostly focused on using basic Linux terminal commands to dig around a machine. Even though I thought I was mostly familiar with these commands already I had a decent amount of trouble with this and had to reach out to the discord for help.
First two question are pretty simple - use ls -a and cat file5 and you get the answers '8' and 'recipes' respectively.
Question 3 is also simple: grep password * (when current dictionary is the one with files1-8) will give you the answer file. The * is just a wildcard that searches through all files.
Question 4 was a bit more of a pain as it required knowledge of regex. Regex, or regular expression, is just a series of characters that define a search expression. There's some pretty neat things you can do with it, but in this I kept it simple and learned just enough to create a pattern to match an IP address. I learned mostly from this site and then used this site to practice. In the end I came up with this:
[0-9]+.[0-9]+.[0-9]+.[0-9]+
Which matches any string with 4 segments of 1 or more digit (the [0-9]+) separated by a period. You can tell how amateurish it is because I didn't even use character classes like \d or account for size limits (1000.0.0.0 is not a valid IP), but honestly whatever works works.

I tried pasting that sequence straight into the ssh session as grep '[0-9]+.[0-9]+.[0-9]+.[0-9]+' *, which gave me nothing.
After doing some digging, I was introduced to the world of different regex engines. Differences between the three most common ones: BRE, ERE and PCRE can be found here. For now, just know that grep uses BRE by default, and using the -E and -P flags switches over to the ERE and PCRE engines respectively. The reason I didn't get any results from my previous command is because the '+' symbol is treated as a symbol in BRE, so when grep sees [0-9]+ it looks for one digit followed by a '+' symbol. We could escape it with a backslash, or we could switch to ERE. In ERE the + gets treated as a 'one or more' modifier, however it also treats the period as any character, so instead of getting an IP we get the following.

Where it matches 4 different segments of digits separated by any character. Escaping the period with a backslash finally gets us what we want.

Question 5 is as simple as printing out the contents of /etc/passwd and counting the users that have a shell location that's not /sbin/nologin. In this case there are 3 users: root, ec2-user, and mcsysadmin.
Question 6 is just the output of sha1sum file8: fa67ee594358d83becdd2cb6c466b25320fd2835. Here's an interesting article I found about how SHA-1 is depricated
Question 7 pretty much asks you to look at the shadow file, but since we don't have any permissions for it we have to see if there's any backups they might've left it in. The following command: find / -name *.bak 2>/dev/null looks for any .bak (backup) files in all directories, and any errors (there's a lot of Permission denied errors) are filtered out. We find that there is a shadow.bak file in /var, which gives us the answer of $6$jbosYsU/$qOYToX/hnKGjT0EscuUIiIqF8GHgokHdy/Rg/DaB.RgkrbeBXPdzpHdMLI6cQJLdFlS4gkBMzilDBYcQvu2ro/:18234:0:99999:7:::
All in all this was one of the more challenging tasks that required me to dig around a lot more and even ask for help (got stuck on the last one). Getting through it gives me a pretty nice sense of pride and accomplishment though!
Learned: Regex, find command, standard linux dictionary structure
Task 10: Ho-Ho-Hosint
This is another one of of the tasks that doesn't require you to deploy and connect to a server, and this one's about OSINT! Very interesting.
The extra material here just gives a quick intro to what OSINT is (honestly just seems like a fancier term for googling). There's a link to the OSINT framework which we don't need for this. The rest is about three tools - Exiftool for image metadata, WayBack Machine, and Reverse Image search. It seemed pretty obvious that the task wants you to use the Exiftool on the downloaded grinch image, so I did:

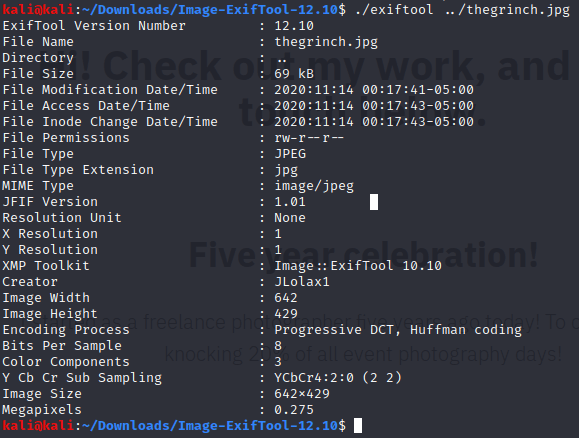 Nothing too interesting here except the creator: JLolax1. The first result after searching that on google leads to a twitter page for the user Elf Lola, from which I got the first three answers DOB (December 29, 1900), occupation (Santa's helpers) and the phone she makes (iPhone).
Nothing too interesting here except the creator: JLolax1. The first result after searching that on google leads to a twitter page for the user Elf Lola, from which I got the first three answers DOB (December 29, 1900), occupation (Santa's helpers) and the phone she makes (iPhone).
If you follow the link to Lola's wordpress site, it just seems to be a pretty empty photographer's website. The woman in the pictures I recognized to be Ada Lovelace, world's first programmer - no reverse image search necessary :)
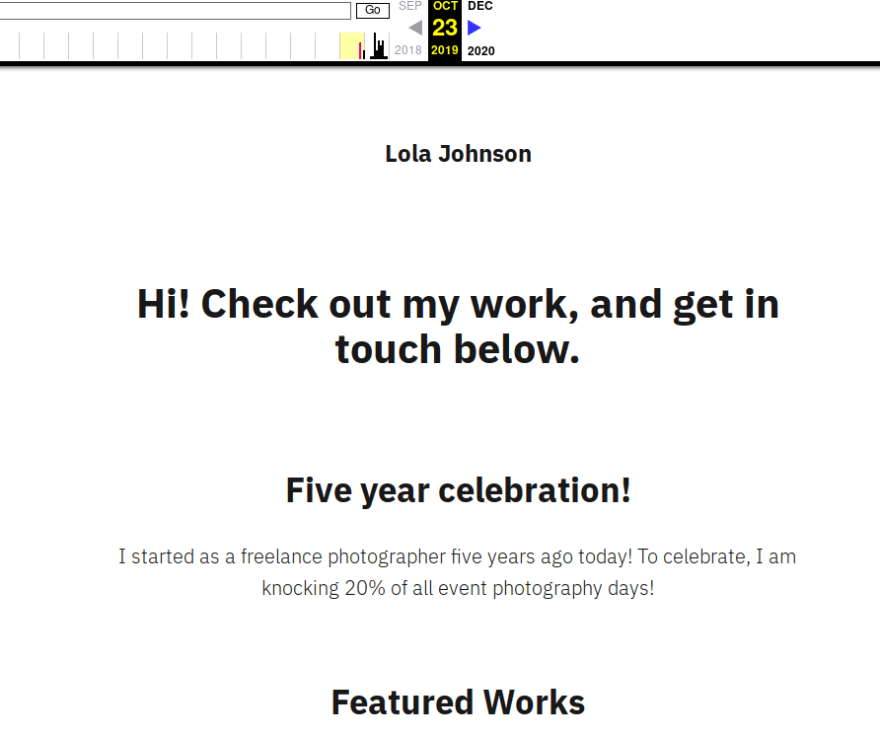
The second to last answer can be found by using the Wayback Machine on Lola's wordpress site. The earliest snapshot comes from October 23, 2019 and the site comes with a text celebrating Lola's 5 year photography anniversary, so the answer is 23/10/2014!
This task was a cakewalk compared to the others, was still pretty cool to learn about OSINT though.
Learned: OSINT

Posted on January 15, 2021
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.