ayy lmao
Posted on January 15, 2021
Task 11: Data Elf-iltration
This task was pretty fun for me. To start off we're given a pcap file and need to find some bits of information that's been exfiltrated from the server.
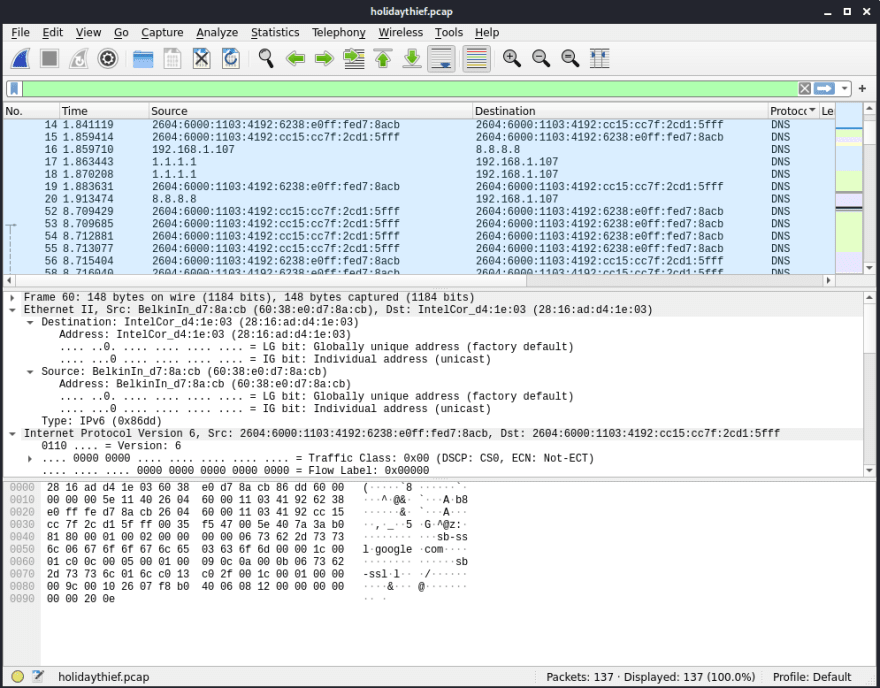
The first question asks us to find information that's been exfiltrated by DNS. At first I didn't really know what I was looking for exactly and just clicked around on any of the 20-ish DNS packets in Wireshark and tried to look for information in the the many name:value pairs listed. After a while of this not getting anywhere, I re-read the supporting doc and did a little research to find this:
There's a lot of neat information in this blog post, but for our purposes all we need is the above image. Malware is able to send information (restricted to letters and digits) as a subdomain to an attacker's registered domain. I somehow missed this in the supporting doc because I didn't know what a subdomain was (it's the portion before the first period) and thought it was some field I could find in the DNS packets.
With this, I just went through every DNS packet in the pcap file and and eventually found packets 17 and 18 with a suspicious query to 43616e64792043616e652053657269616c204e756d6265722038343931.holidaythief.com. Run the subdomain text through a hex decoder to get Candy Cane Serial Number 8491, the answer to our first question.
The next two questions are fairly straightforward. Exporting HTTP objects from Wireshark gives us two files: TryHackMe.jpg and christmaslists.zip. Using steghide, the hidden contents in the jpg file is written to christmasmonster.txt. Inside is a sort of poem:
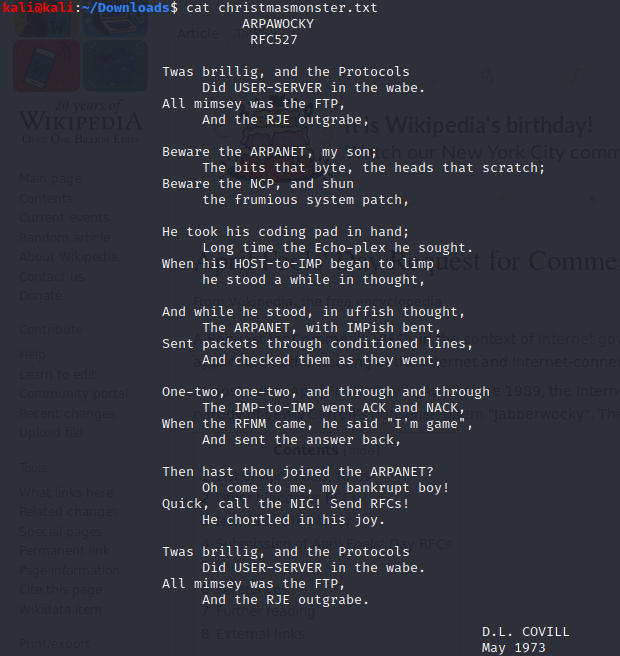
After a little bit of digging it turns out to be an Request for Comments (RTF), which are usually used to describe methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems (Wikipedia). This particular one, RTF527 is an April Fool's play on the 1871 Jabberwocky poem from Lewis Caroll. RTF527 is also the answer to the third question.
Use fcrackzip on the zip file to get the password december. Use that to find this christmas list for timmy and the second answer: PenTester
Lots of cool information found in this one, learned about topics I never knew about and finished in not too bad of a timeframe. All in all not bad!
Learned: DNS Exfiltration, subdomains, steganography

Posted on January 15, 2021
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.