Loop DOS? Letś Discuss.

EvanForensics
Posted on March 27, 2024

New Loop DoS Attack Targets Application Layer Protocols
A new type of denial-of-service (DoS) attack, named "Loop DoS," has emerged, targeting application layer protocols that rely on the User Datagram Protocol (UDP). Developed by researchers at the CISPA Helmholtz-Center for Information Security, this attack can affect an estimated 300,000 hosts and their networks.
How Does Loop DoS Work?
Loop DoS takes advantage of a vulnerability in the implementation of the UDP protocol, specifically its susceptibility to IP spoofing and lack of sufficient packet verification. When an attacker exploits this vulnerability, they create a self-perpetuating mechanism that generates excessive traffic without limits or a means to stop it.
Potential Outcomes of Loop DoS Attacks
There are three possible outcomes when an attacker leverages the vulnerability:
Overloading of a vulnerable service: The attack can cause a service to become unstable or unusable due to the excessive traffic generated.
Network outage: The attack can lead to a denial-of-service condition on the network backbone, causing network outages for other services.
Amplification attacks: Network loops can cause amplified distributed denial-of-service (DDOS) attacks, where the attacker's traffic is multiplied before reaching the target.
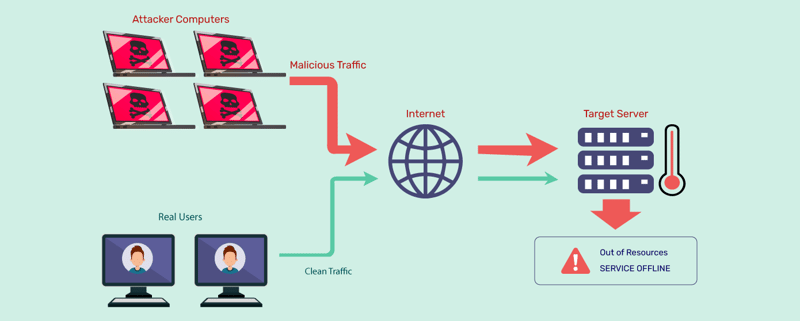
Impact and Mitigation Strategies
The potential impact of Loop DoS extends to both legacy and modern protocols, affecting crucial internet-based functions like time synchronization, domain name resolution, and file transfer without authentication. To mitigate the risks associated with Loop DoS, CERT/CC recommends several strategies:
Install the latest patches from vendors addressing the vulnerability.
Replace products that no longer receive security updates.
Use firewall rules and access-control lists for UDP applications.
Turn off unnecessary UDP services.
Implement TCP or request validation.
Deploy anti-spoofing solutions like BCP38 and Unicast Reverse Path Forwarding (uRPF).
Utilize Quality-of-Service (QoS) measures to limit network traffic and protect against abuse from network loops and DoS amplifications.
As of now, there is no evidence of active exploitation of the Loop DoS vulnerability, but the researchers warn that it is easy to exploit. Vendors confirmed to be affected by CVE-2024-2169 include Broadcom, Cisco, Honeywell, Microsoft, and MikroTik.

Posted on March 27, 2024
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.
