Apple constantly claims “macOS is the most secure operating system” and if you are an average user(just like my past self), then chances are you are in delusion just like younger me(well, I’m older and wiser now🧑🎓).
Originally posted on Medium:
Apple repeats this phrase way too often that subconsciously we believe that macOS is indeed most secure operating system in the world. But the truth is: it is not so secure after all. macOS is just difficult to break for an average programmer but not impossible for any programmer who has enough time and intuition of where to look and what to do.
First, let me clear something. The reason why people think that windows is not secure is because it makes into the news most of the time whenever there was a virus attack around the world. But have you once stopped and considered why?
- Because many people use cracked versions of Microsoft Windows
- Because many people install cracked versions of software
- Because there are no restrictions/warnings when untrusted software is being installed
So, how is Apple doing it differently?
- To begin with, macOS is free for macs. The major thing is, updates are also free since long time.
- Using cracked version of macOS on non-macs(Hackintosh) is very tricky and buggy. So, most of them avoid it.
- Unless you are an average user, you can’t even install softwares from unidentified sites and developers. Apple straight out blocks installation.
So, now you can see why Windows is more susceptible to virus attacks.
Another new feature coming in iOS 14 is, Apple notifies users what the app is doing behind the scenes
I wonder how many developers in the world actually use a specific library intended to use the clipboard and a specific function to copy the contents *accidentally*🤔.
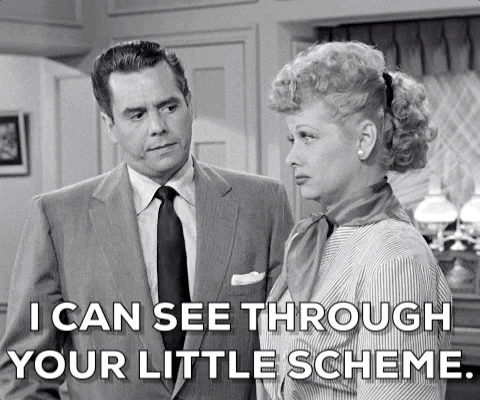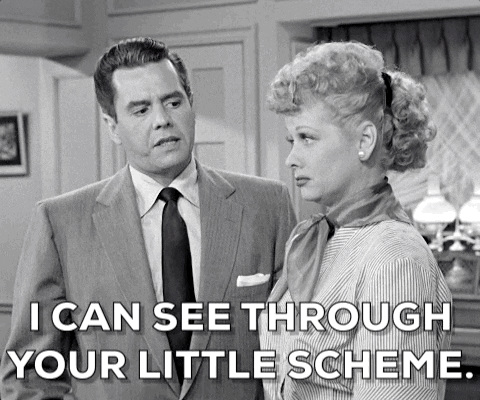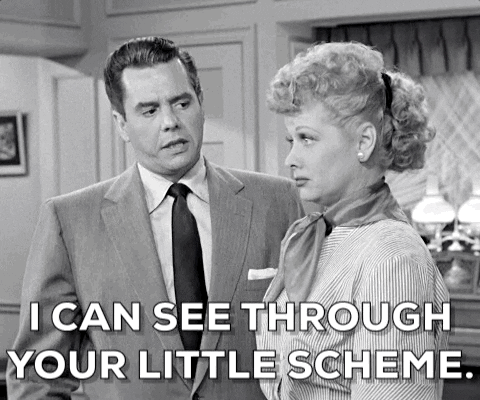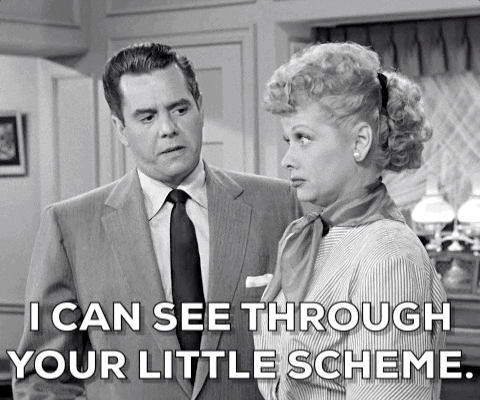
And as usually, the Linkedin’s response was “It’s a bug”

So, now you know how Apple is trying to secure its operating system. It is not secure by default. It just lets users decide and take control instead of letting users use it blindly. If you don’t know, in macOS, whenever an app tries to read a file from a directory, it asks for the user permission to allow it or not.
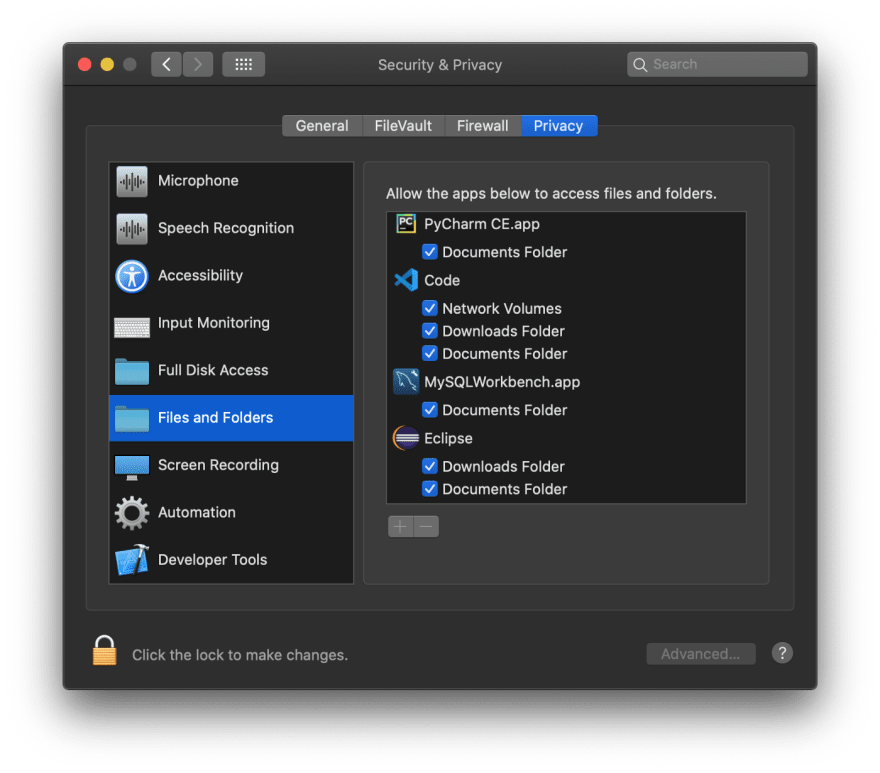
If android and windows used the same features, then both can also become a secure one. But they won't.
So, what exactly breaking a system mean?
Well, to keep it simple, bypassing the system also comes under Breaking the system.
I wrote a Keylogger for macOS, which bypasses notifying users that it is being used in the settings and actually no password is required to run the keylogger.
For some of you who don’t know, macOS doesn’t prevent anyone from creating a keylogger. But to log the key strokes, the new APIs provided by the Apple comes under Accessibility functionality, which requires user password to run and the name of the app we are running in the Settings -> Security & Privacy section.
The below link takes you to some of known open source keyloggers for macOS on GitHub and you can try that and see. Everything requires the user password to actually run the app and it will be shown in the settings app.
Well, that’s a pretty good security from Apple.
So, how did I break it?
The trick is simple to break/hack anything. Look at the past versions of the system and try to modify it to break the new updated system
If the engineers are really good and actually had time, they would completely remove it from the systems. But most of the engineers don’t have enough time to remove it. So, as they are good, they just fix it on the surface level and forget about it later or if the functionality is tightly coupled with the systems then they remove every known documentation about it to restrict its further usage. And that’s what apple did. That API is one of the essential APIs and Apple cannot remove it completely. Instead they removed most of the documentation and archived it.
Usually, the API docs for old versions are not properly available on the internet. Most of the companies remove it. But once I coincidentally came across a website which conveniently archives every apple developer docs released, which is maintained by Apple itself.
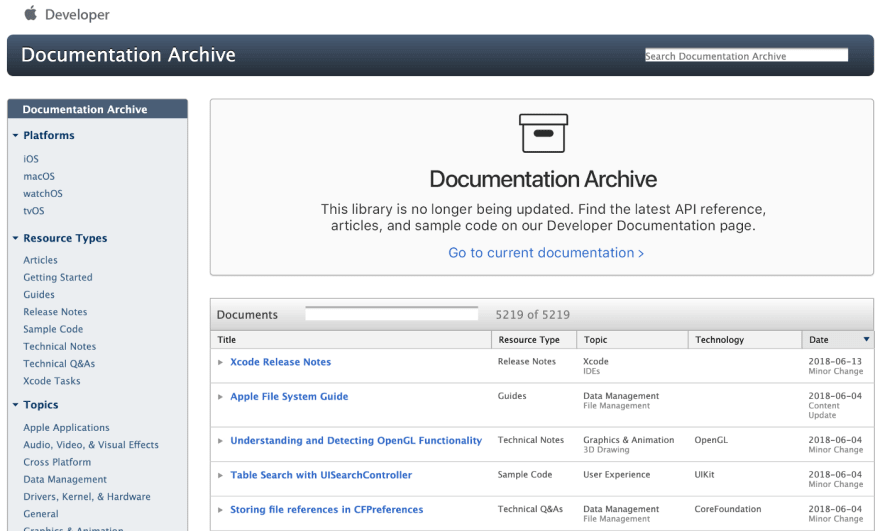
It has a total of 5219 documents, with the oldest one dated 1985–03–01 (That is some serious dedication of Apple towards its developers).
And going through one by one is not gonna happen. So, as a wannabe coder, I did what every wannabe coder does. Yes, I wrote a script to parse the contents of every document and flagged some documents with particular keywords which would likely appear in the developer docs which might help me to write a keylogger. Now, I reduced the number of documents from around 5,000 to about 500. I can reduce further(by removing documents with low frequency of occurrences), but I don’t wanna take any chances. So, instead of reducing the number, I sorted the documents with the frequency of keywords and started going through one by one.
It probably took over a month to shortlist some documents which can help me to write a keylogger. It might sound stupid but once again I went through the new set of shortlisted documents to further shortlist.
Finally, after 3 months of going through those, I was left with 1 document. Uff… that was a hell of a journey to reach 1 document from 5,000 documents.
The document is: Technical Note TN2187

It was published on 2007–12–18 for developers to develop apps for Mac OS X 10.5 (Leopard)
The keywords that picked up this document is “USB” and “KEYBOARD”. Surprisingly, their occurrences in the document is:
- USB: 6 times
- KEYBOARD: 8 times
If I had further reduced the number of documents by removing low frequency occurrences then I wouldn’t have came across this document for sure. I guess it’s time for another tip:
If you want to break a system, there are no shortcuts. You have to go through every single thing you got. You never know what you missed. Or the best thing to remember while coding anything is: Murphy’s Law
Now, back to why you are here. That document is so old that, most of the links mentioned in that no longer exists. Everything is 404.
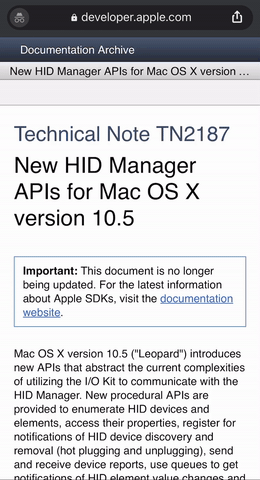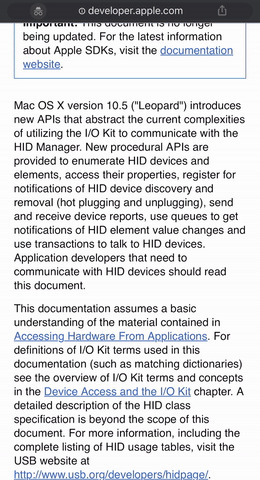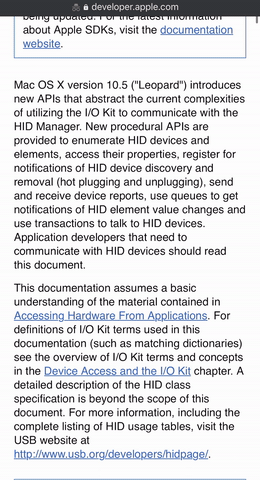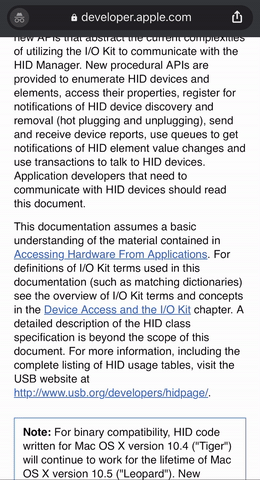
Those links are very important because it clearly states that:

So, now I don’t have any references to actually have the basic understanding about how to use this doc. To further complicate things, the docs are in Objective — C, which I have never touched.
But the odds are on my side. I got plenty of time to waste and if you ask any programmer/engineer, they will say that anything could be built, given enough time.
Without a further a due, I started coding it in Swift and logging every line of code to understand what’s it doing exactly. It took well over 2 weeks to decode everything and map every key code generated by that interface to the actual keyboard values.
Finally, after 4 months of persistent work, I completed writing the code for my keylogger. It just took 420 lines of unoptimised code(I swear I did not plan to reach that exact number) to break the most secure OS, the macOS.
Link to the keylogger
I open-sourced the keylogger on 2017–02–01 on GitHub. It became so popular that it was on the trending page of GitHub for multiple days world freaking wide.
Keylogger for mac written in Swift using HID
macOS Swift-Keylogger



It is a simple and easy to use keylogger for macOS. It is not meant to be malicious. There are only few keyloggers available for Mac and none of them are in Swift.
Another problem is with Apple high-level APIs. I don't know the reason but Apple suddenly deprecates and removes the documentation of APIs from its website.
So, I don't want to keep checking about the availability of their APIs and changing my code frequently. That is the reason I went for low-level API which is using HID API.
Most of the keyloggers available only log keystrokes into a file without much information about on which app the keystrokes are generated.
Usage
Clone the repository and open the project in Xcode and build the project and run the executable.
To run it in the background
To be able to close the Terminal when Keylogger is running, use…
And don’t think it won’t steal passwords by seeing the below disclaimer in the Readme in my github link:
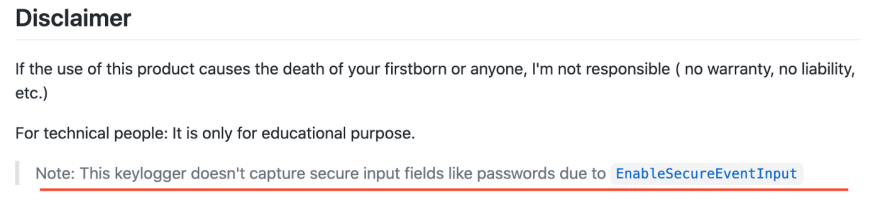
It can also be bypassed very easily and putting it on the internet won’t be “for educational purpose” anymore, even if I state it explicitly in the documentation. So, I excluded it from the open-source.
What is the current status of the project?
Unfortunately, it doesn’t work anymore as initially intended on macOS Catalina (10.15 ), which was released on 2019–10–07
From 10.15 onwards, it asks for the user’s permission to run and it shows up in the Settings -> Security & Privacy -> Privacy -> Input Monitoring

But it still works perfectly fine till macOS Catalina, without requiring any permissions to run and also without showing up in the Settings app.
But, am I sad that Apple fixed it?
No, in fact I’m happy. It’s probably a good thing that Apple fixed this. It prevents so many clueless people from being spied on or protecting them from losing important stuff from their personal computers by sniffing.
For example, it stops Linkedin, Facebook like many corporations from spying on people and stealing data without their consent and when caught, they say “it’s a bug”
Hate Apple how much you want to hate for their expensive products or imposing “Apple Tax” on it’s customers but, when it comes to security, privacy and ease of use, particularly in this age, it’s still worth to pay that “Apple Tax” to own Apple products, at least for important stuff.
Inner me: I really hope Apple comes across this page and sponsors me for this post for talking good and promoting it🤞
Summary
If you reached till here, you might be thinking is it really breaking the macOS?
To recap what I said in the beginning —
Well, to keep it simple, bypassing the system also comes under Breaking the system.
I wrote a Keylogger for macOS, which bypasses notifying users that it is being used in the settings and actually no password is required to run the keylogger.
For some of you who don’t know, macOS doesn’t prevent anyone from creating a keylogger. But to log the key strokes, the new APIs provided by the Apple comes under Accessibility functionality, which requires user password to run and the name of the app we are running in the Settings -> Security & Privacy section.
So, yeah… I broke it 🤷
Whether it’s Linux, Windows, macOS or any other Operating system, it doesn’t matter. Every OS has their fair share of never ending bugs. That’s why companies constantly release Security Updates.
The only thing Apple is doing differently is that they are providing maximum details about what the apps are doing to its customers. So, even if the OS fails to protect, users can at least see what’s happening and mitigate the damage ASAP. For example, people wouldn’t know how some companies are stealing data from the clipboard of the users if its not for iOS 14. Or my Keylogger stealing from your mac.
Feel free to contact me -
If you are interested in learning everything from the scratch related to programming, head over to my Medium Publication - From the Scratch