Walkthrough - OWASP Top 10 - TryHackMe

qwezii
Posted on July 17, 2020
Hi Guys!
This is my very first Walkthrough/Write-Up.
This is a Walkthrough on the OWASP Top 10 room in TryHackMe.
This is a beginner room - as in
The challenges are designed for beginners and assume no previous knowledge of security.
I am going to walk you through the steps I followed to find the answers.
Day 1 Injection
Strange Text:
A strange text file in the website root directory:
I used ls. We see the output something like this:
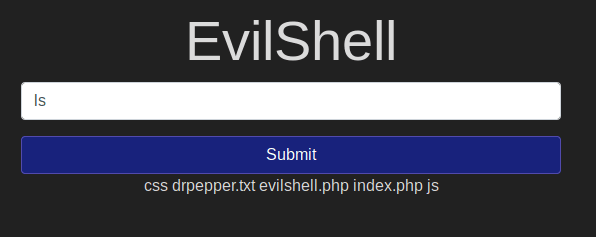
ls command lists all the available files and folders in the current directory. And with that output, we understand that drpepper.txt is a strange text file.
Take me to Top
Number Of Users
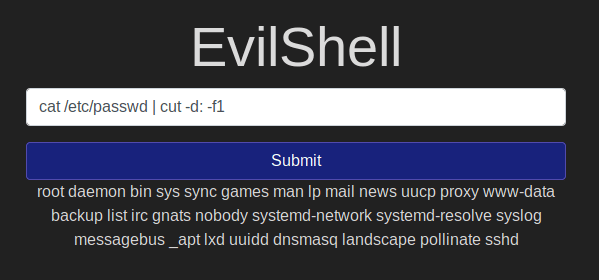
The number of non-root/non-service/non-daemon users:
We can use the command: cat /etc/passwd | cut -d: -f1
I found this command here: LinuxHandBook
And the output from the command shows there are no users that are non-root/non-service/non-daemon. And therefore the number is 0. The cat command prints all the contents of a file mentioned and we are using pipe - | to send the output of the cat to the following command i.e, cut -d: -f1 which cuts(or only prints) a repeating part of an output. In our case - we mention the delimiter as : and the -f1 would print the first part of the delimited string.
Take me to Top
User:
The user of the app:
whoami is a command that shows the current user of the application through which the shell/bash is running. So the user is www-data
Take me to Top
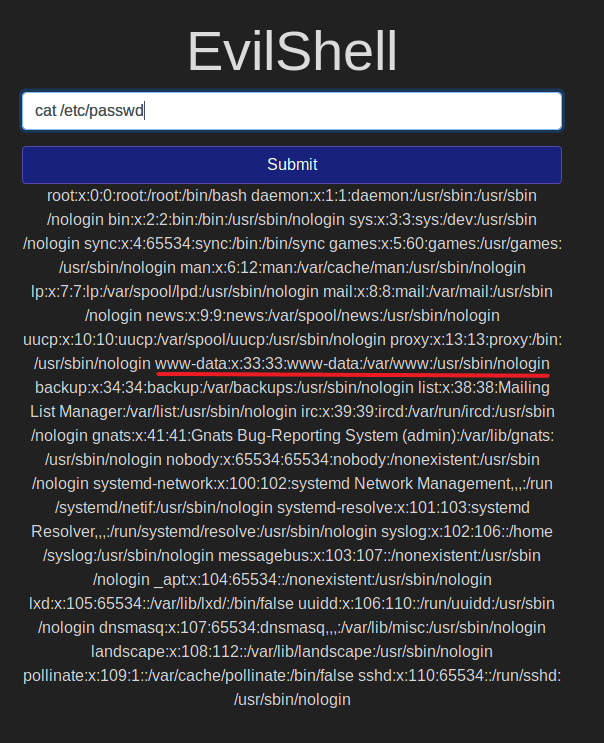
User Shell As:
I used id to find the user id. Which is 33. id prints the current user-id and group-id.
And then I used cat /etc/passwd/ to print all the list of user information.
With the command, we see a lot of information here, and we need to find the one with the id 33, or the one with the user as www-data as we found in question 3. And we see that the user is set as /usr/sbin/nologin.
Take me to Top
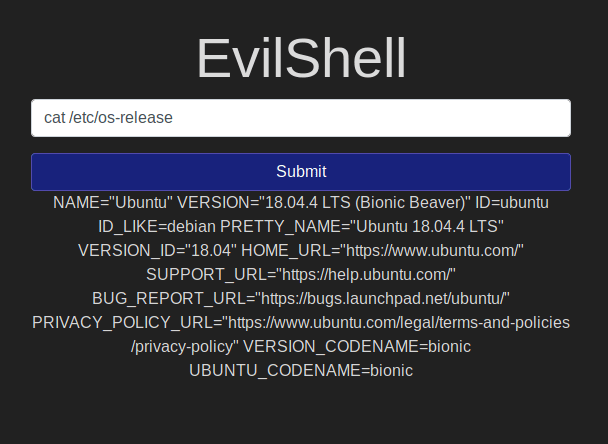
Ubuntu Version
The version of Ubuntu:
I found this command cat /etc/os-release, can print comprehensive information on the Operating System.
Here we see the version as 18.04.4.
Take me to Top
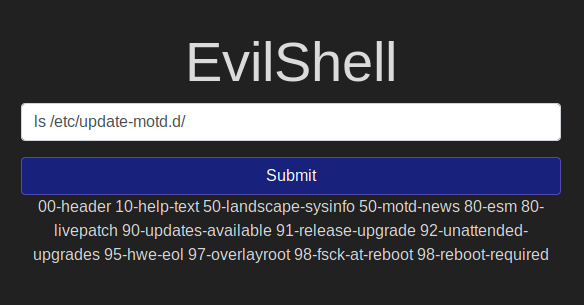
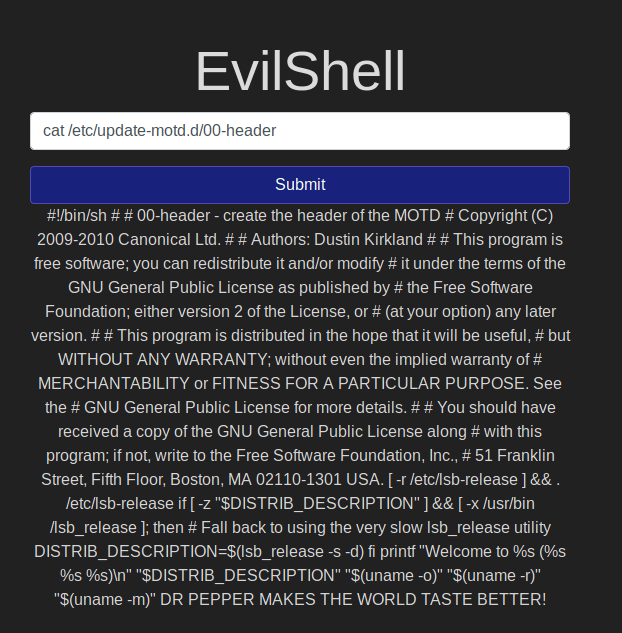
MOTD:
I first could not find the motd as I first thought its at /etc/motd. Then I found that it's a different directory.
With the command ls /etc/update-motd.d/ I could see the files and one of them is 00-header and this is mentioned in the hint. So I used the command cat /etc/update-motd.d/00-header
Now we can see in the last line of the output talks about "Dr Pepper" and that is the favorite beverage.
Day 2 Broken Authentication
I found this type of attack cool. Now, if we just follow the instructions we can find the answers to the given questions.
Darren's Account:
We try to register a new account using the name "darren" but we see a message saying user already exists. But the problem with this is in the backend of the application, with this step we now have overridden the password for darren with what we have used for the registration. Now we just have to login using the same password but add a space to the username: " darren".
Now we are logged in as darren and we see the flag.
Arthur's Account:
We follow the same steps that we followed for darren's account.
We try to register using username "arthur" and some password.
Then we see the message that user already exists.
Then we login as " arthur" and the same password we used to register. We are taken to arthur's account.
Day 3 Sensitive Data Exposure
Sensitive Directory:
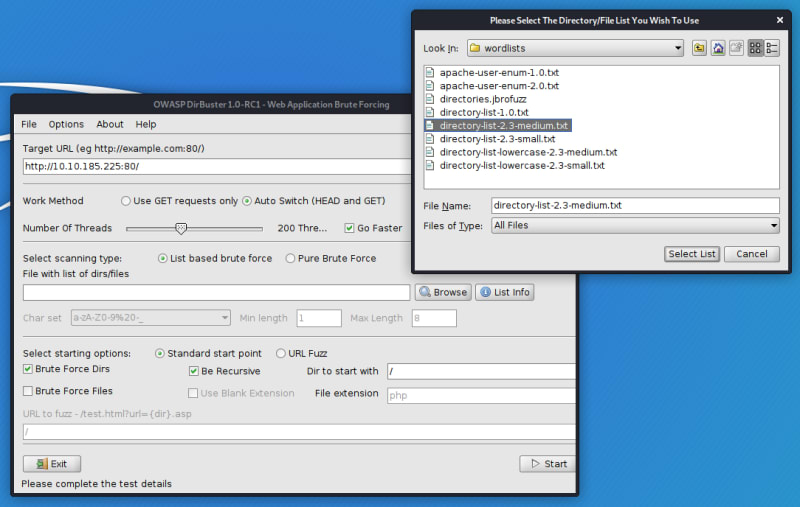
For this task, I used a subdirectory enumerator software called DirBuster that is available in Kali Linux by default.
I used the following settings:
I used the wordlist file that is available by default here:
/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Then I let it run for a while and found.
But it will be a lot simpler if we use the hint. We see that there is something in the login page source code.
We see that the developer has stored something in the /assets directory.
DB File:
When you open the directory you will see the .db file. Click on it to download.
Or you could directly go to http://MACHINE_IP/assets/webapp.db to download.
Sensitive Data:
Then I used the mentioned commands in the given Material. And found the following:
We see the Admin, Bob, Alice users and their password hash.
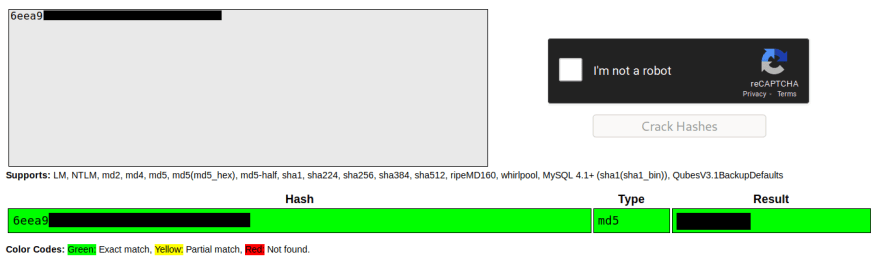
Admin Password:
I used the website Crackstation mentioned in the given material to crack the password hash.
Admin Flag:
I used the login page to login as admin and found the flag.
The current room is a progressive room and releases one task per day. I will try to update this page as and when I find the answers.

Posted on July 17, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.