SBOM with FOSSology

Paweł Piwosz
Posted on November 16, 2022

This episode is about FOSSology, the open source tool which is categorized as Audit, Consume and Transform tool. The project is part of Linux Foundation Project.
We will see how it works in the simplest installation, a docker container. We have multiple options, starting with installation directly on our system, use single container, or prepared docker-compose setup to add external database. As we have docker-compose ready, it is very easy to move the installation to other environments, like, for example, Kubernetes.
Let's run the container, then!
docker run -p 8081:80 fossology/fossology
Now we can enter the website, using http://localhost:8081/repo/ url. The login is simple, user and password are fossy.
VCS
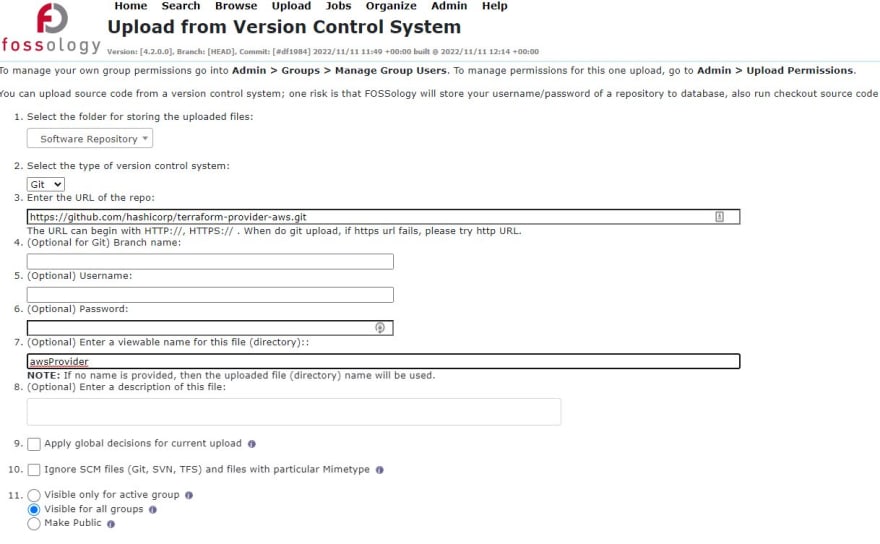
At the beginning we will try to scan some GitHub repo. I selected one, where I expect a lot of actions done through time. Select Upload and the From Version Control System.
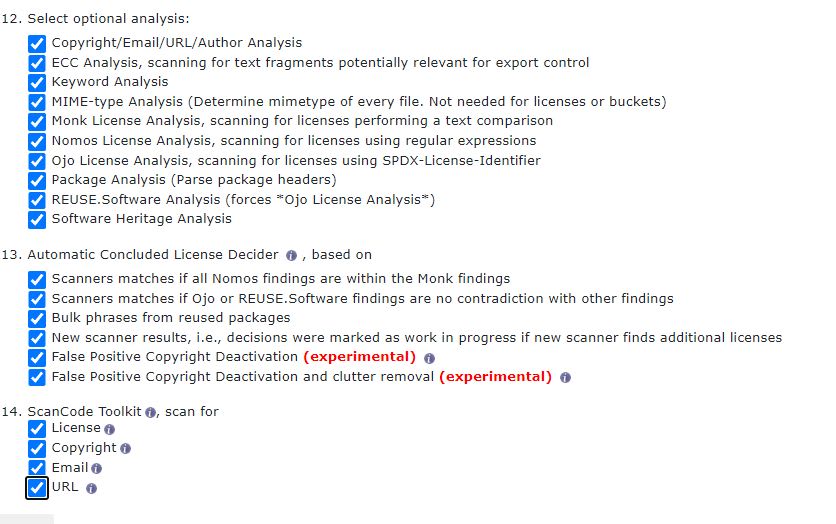
With the analytics options I go crazy, I select all :)
And then we need to click Upload button, which is quite hidden in bottom left side.
Please notice, the UX now is not perfect. In the first moment I didn't know if action was successful or not.
But, yes, it was :)
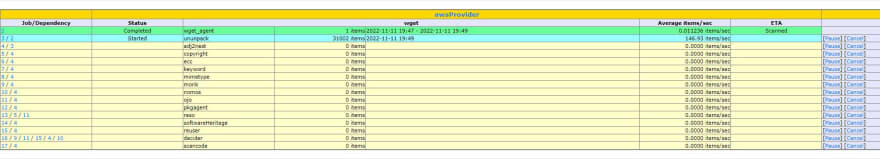
Let's go to Jobs and then My recent jobs. This shows the status of jobs. AS we can see on the screen below, my jobs are still running. Very clean and clear information panel!
We can pause or stop jobs if we want
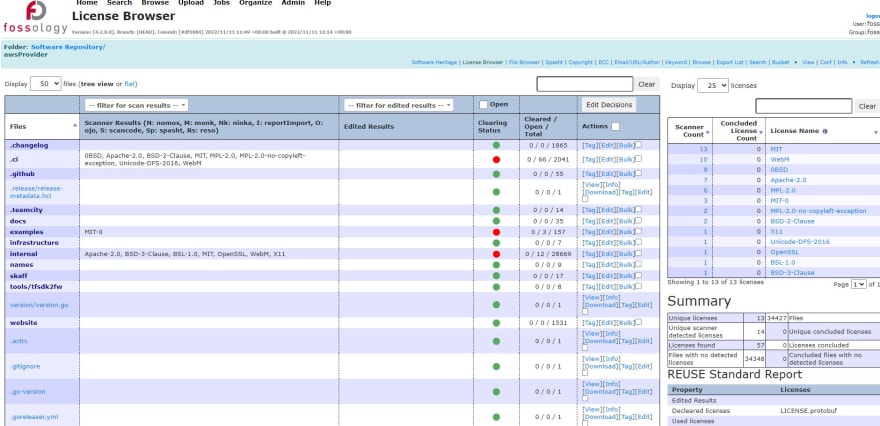
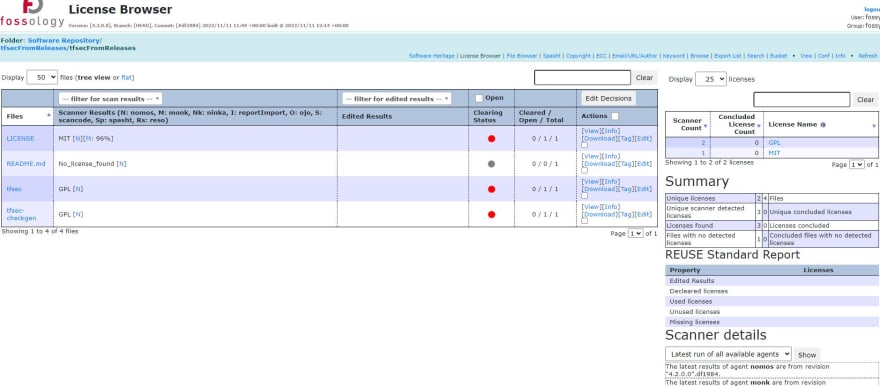
Scan is in progress, but we can look on part already collected. For example, License Browser
We see here very complex report. We can get even more info, by clicking on each element.
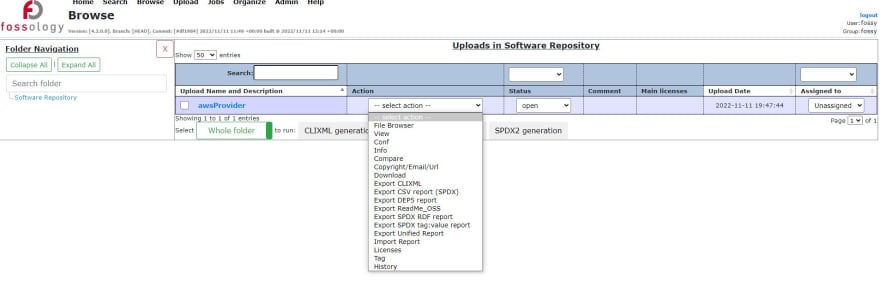
In the Browse menu we can decide what action should be taken.
AS we can see, FOSSology is also an "operational" tool. We can assign people to be the owners of the report, we can change status of the project.
Reports
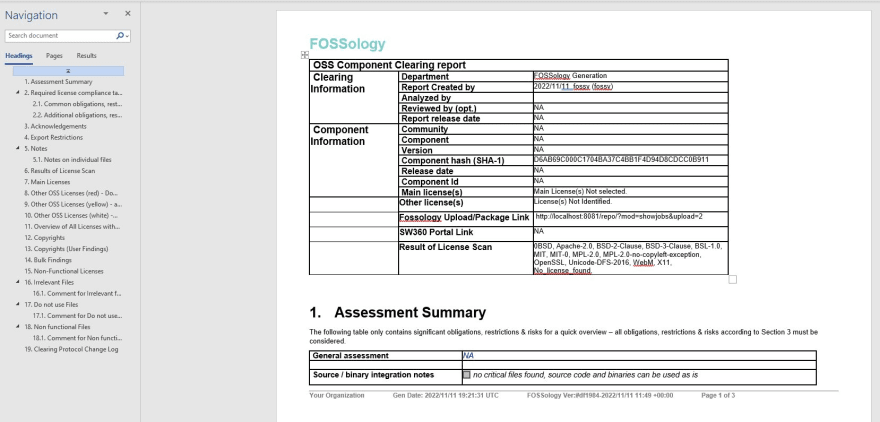
I've created unified report, which I downloaded from Jobs section. This report is generated as MS Word file and is very detailed.
File from URL
As a next excercise, I use tfsec project downloaded directly from GitHub releases. I love tfsec as a tool, so I use this opportunity to learn more about it :) We will see how many information the tool is able to extract from executable.
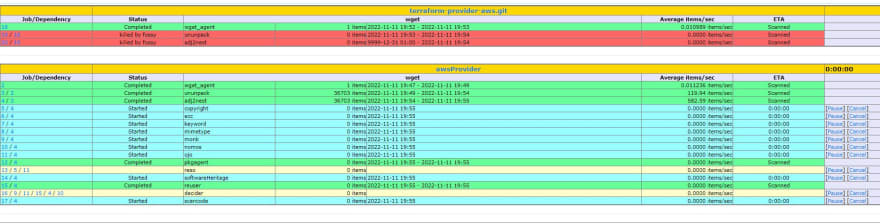
This time, reports shows more data about licenses, etc. Don't get it wrong, it is not the FOSSology things, simply speaking, more work in this area is done for thsec than for TF AWS provider :)
Duration of scan
Well, it depends on the type of scan. softwareHeritage can be very long. I mean, very, very long. Generally, we have to prepare ourselves to give around 15 minutes to complete scan (except SoftwareHeritage). Of course it depends on the package type, size, etc, but it is definitely not something what can be seamlessly added to the pipelines (however, this should be obvious).
Summary
Very useful tool. Helps to analyze data from multiple sources. Only one missing point for me is to scan Docker containers.
The GUI is quite clean and useful. Everything is easy to be found, navigation is really easy. The one exception is mentioned confirmation (or failure) of adding project to the application.
FOSSology is using external services for some checks, what might be problematic in many situations.
User management is quite advanced for such tool. API is available and each user can generate the personal token to use.
I like FOSSology and I think I will remember about it when it comes to SBOMs in pipelines.
The downside of this tool might be the file size limitation. We can upload files to 700M, so majority of iso images is too big for this scanner (for example current Ubuntu iso images are way bigger).

Posted on November 16, 2022
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.