Kubescape: a Kind Insurance Inspector for Your Kubernetes Investments

Roman Belshevitz
Posted on June 13, 2022

0. Introduction
Container security is a critical aspect of running and administering a cloud environment. This article will focus on open source security tools for Kubernetes and containers, as we feel that some free tools are just as good as their commercial counterparts.
One of a major challenges among DevOps tasks is usually in charge of container creation and maintenance. They employ continuous integration and continuous delivery pipelines, often known as CI/CD pipelines, to stay up with the fast speed of business you're used to, as well as the competition and client demand. However, if security isn't part of the equation, you might soon expose yourself to danger. Because regular DevOps people aren't always best trained in security, the correct container tools and security solutions are critical.
The Red Hat State of Kubernetes Security Report exposes many of the issues that exist in the present Kubernetes ecosystem. The following are some of the report's most notable data points:
- Security worries around Kubernetes have hampered or delayed production implementation for 55 percent of business IT companies.
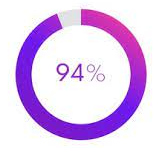
- In the last 12 months, 94 percent of survey respondents indicated that they had at least one security incident in their Kubernetes system.
- The biggest issue of 59 percent of businesses about adopting container techniques is how to secure them and maintain a good security posture.
More than only vulnerability detection is done by container security tools. They make sure that everything in your container is running according to your instructions. The process of securing containers must run in the background, not just guarding the container host, its network traffic, and its management stack, but also maintaining the build pipeline, your application security, and the container's fundamental layers.
Here is a review of one powerful open-source container tool that can help you do just that.
I. What makes kubescape special
First to say, kubescape is the first open source by ARMO (5.8k⭐) tool for running NSA and CISA Kubernetes hardening tests.
To assist companies in making their Kubernetes environments more difficult to compromise, the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have published comprehensive recommendations in 60 pages for strengthening the security of an organization's Kubernetes system.
This 66-page cybersecurity technical paper focuses on the common origins of a compromised Kubernetes environment and provides practical advice for administrators on how to operate Kubernetes securely.
To learn more, visit kubescape GitHub page.
Kubescape is based on Open Policy Agent engine and ARMO’s posture controls.
Kubescape retrieves the Kubernetes objects from the API server and scan them by running a set of snippets developed by ARMO.
🎓 If you're interesting what OPA is, please read this article by Magalix.
Kubescape establishes how well your Kubernetes configurations meet the best practice recommendations from the NSA and CISA guidance.
The output results are printed in a console friendly manner by default, but they can be also retrieved in JUnit XML, JSON, PDF or even in Prometheus' metrics format for further processing.
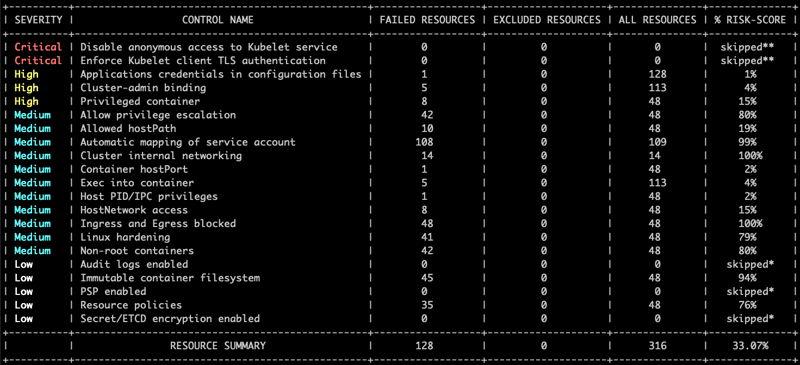
Also, when working with ARMO portal, you may export the resulting report to a CSV file.
II. What can you test your orchestrator for
Kubescape is running the following tests according to what is defined Kubernetes Hardening Guidance by NSA and CISA. Among of them are:
- Non-root containers
- Immutable container file system
- Building secure container images
- Privileged containers
-
hostPID,hostIPCprivileges -
hostNetworkaccess -
allowedHostPathsfield - Protecting pod service account tokens
- Pods in
kube-systemandkube-public - Resource policies
- Control plane hardening
- Encrypted secrets
- Anonymous Requests
The number of tests is constantly increasing, the company maintains updated CVE database.
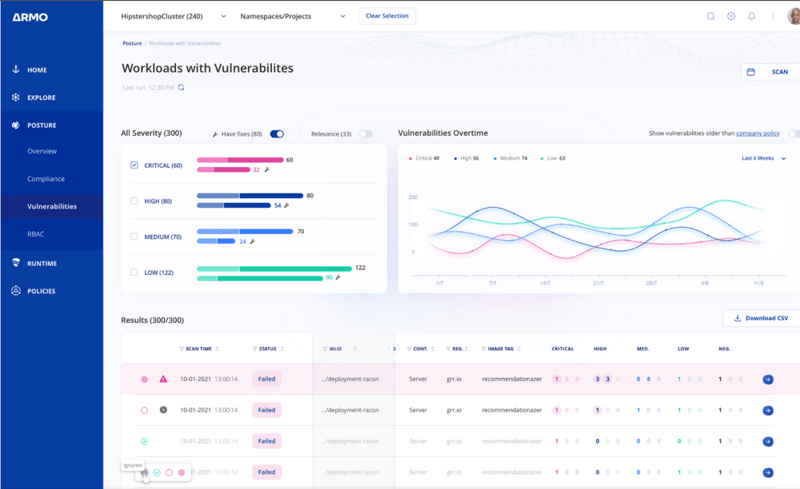
The connectivity of roles and privileges between different portions of a Kubernetes cluster is visualized using a strong Role-Based Access Control (RBAC) module. All of these features are already available in Kubescape. Kubescape explains why controls fail and suggests configuration changes to improve security posture for developers and DevOps teams.
The company offers pricing plans which vary depending on a number of your worker nodes. You pay for access to ARMO's CVE database and to their web portal.
III. Appearances, passwords, misty signs
You may install kubescape with or without pre-registering your cluster on the portal (in the first case, a secret key is provided). A helm chart is available for convenient installation.
Kubescape can function without being connected to a cluster. You may validate the security of resource manifests saved as local YAML files (it looks like kubescape scan *.yaml) before applying them to your cluster.
Add an extra parameter to define the YAML manifests you wish to scan.
There's an option of integration with popular cloud providers (some limitations should be kept in mind), and also of CI integration.
For example, in your GHA CI you may create a trigger job which is capable to stop the whole flow if your YAMLs are failing the security checks. To achieve that, you can invoke the tool with -t flag and an appropriate value. Valid values are integers between 0 - 100. A value of 100 will never fail.
jobs:
nsa-security-check:
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v2
- name: Scan YAML files
run: kubescape scan framework nsa -t 20 deployments/*.yaml
🎓 See one of the best flows here. Thanks to Kumar Anurag.
Your kubescape enabled job will return failure if more than 20 percent of objects are failing security tests.
IV. Limitations
All this, of course, is wonderful, but it should be noted separately that Kubescape does check involved docker images, but it doesn’t check for vulnerabilities inside the docker containers you run in your cluster.
You’ll need another tool such as docker scan, grype or trivy to do that. Running a container scanning engine alongside Kubescape gives you the most complete picture of your environment’s security posture.
V. Argumentum ad populum
Viktor Farcic, widely known in narrow DevOps circles, did not remain indifferent to the solution from ARMO.
Well, so are we! It should be noted that the author of the article, at least, did not find competitors for the described tool. Maybe, except Bridgecrew's checkov, but they use completely different approaches. So, definitely, this is a topic for another article, not this one.
By the end of April 2022, ARMO has raised $30 million in Series A funding. At Otomato, we wish them continued success in maintaining community interest and selling plans! 💰
Picture: ITPro UK / Shutterstock / Dilbert

Posted on June 13, 2022
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.