Kaloyan Yosifov
Posted on January 27, 2023

Your extraordinary one time secret
In this post we will go through our new project we created and open sourced at Tapro Labs. Let this post be a brief introduction of our project and elaboration on our agenda.
What is it about? (Brief introduction)
In our company we used a really interesting way of sharing secret. For starters when we wanted to share usernames or passwords, we would upload them in k8s secrets resource, then the other party would just fetch the secret through the Command Line.
For a small company of engineers that is fine, but when we have to send passwords or files to non engineers it gets tricky.
So instead, we decided to create our own custom solution for sharing secrets in our company.
Why not use an already built in open source solution?
We looked at other solutions at the time like Luzifer’s OTS and Sniptt’s OTS.
Which fit nicely into our use case, but since we considered adding more unique features and wanted to wet our feet with Rust, we decided to start from scratch.
What is OTS
Let’s start by first explaining what is one time secret sharing:
Ideally a one time secret app allows people to share private info without the server ever having knowledge of what that info is.
Encrypted secret is stored for a short period of time on the server
Server cannot know about the encryption key
Basic implementation:
User sends an encrypted secret to the server
Server returns a unique id to reference that secret
User then sends the id along with the decryption key to the recipient
Recipient queries the server with the secretId
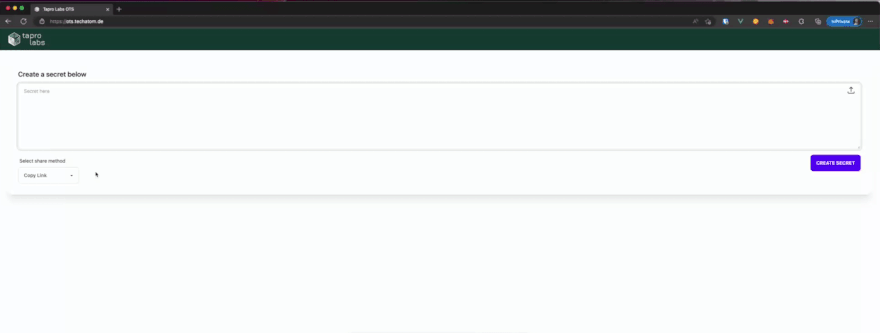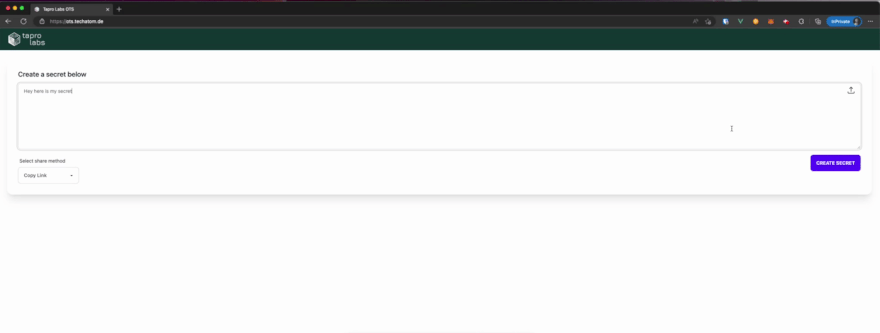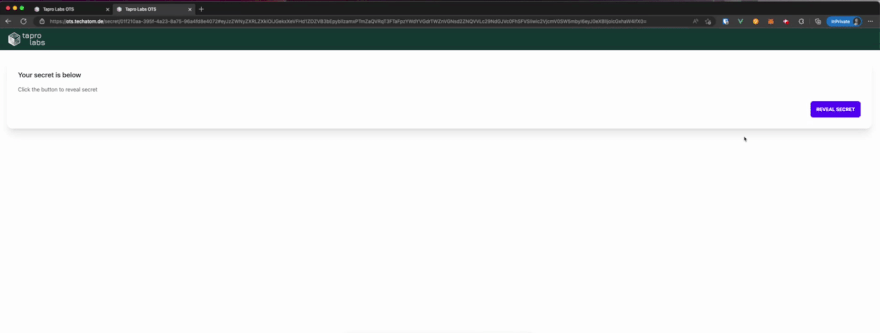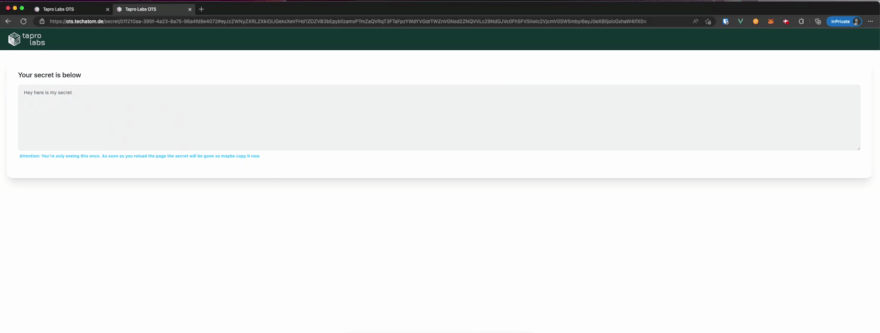
Server responds with the encrypted secret and removes it from it’s storage system.
Recipient decrypts the secret with the decryption key
The secret is stored by default for **24 hours **or until someone views the secret.
Why are we doing it (Agenda)
To make password, confidential documents and secrets easy to share for both developers and non developers alike
To improve our skills
To open source our first project and help people who would need the additional custom solutions we built.
What makes it so special?
Let’s check the features of both mentioned packages above and compare them to our OTS.
Luzifer’s OTS:
Secrets are encrypted by the client
Server has no knowledge of the encryption/decryption key
Secret is destroyed after being viewed or after a period of time.
Multilingual
Sniptt’s OTS:
Secrets are encrypted by the client
Server has no knowledge of the encryption/decryption key
Secret is destroyed after being viewed or after a period of time.
Documentation for self hosting
Sharing secrets through the CLI
Specify time to live period
And here is what our OTS support:
Secrets are encrypted by the client
Server has no knowledge of the encryption/decryption key
Secret is destroyed after being viewed or after a period of time.
Slack app integration
File uploads (up to 40MB)
With more features on the way:
Command line integration
Specify time to live period
Self-hosting helm chart
Chrome extension
Use Cases
Most of the time we are sharing passwords or environment variables, but it didn’t took long enough for us to want to send files as well.
Usually when we interview people we get their CV. After the interview, this file must not be located anywhere in our company systems or personal computers. Most of the time we would send these files through slack, but we had to remember to delete them afterwards along with us trusting that Slack is not breaching their policy or no hacker is in their servers.
This is where the file integration comes into place. It still has the same security features as sending plain text, but it allows us to not forget to delete the file from the messaging system (Slack).
Short Demo
Here is a short demo displaying how it works in the browser:
Conclusion
We host our application at https://ots.techatom.de . While it is secure enough to use, we would recommend that you go with self-host approach. At the moment it is not documented, but we will create a helm chart ready for use in the future. You can watch for update in the repository here
Remember to keep secrets a secret 😉 and thanks for reading! 🙌

Posted on January 27, 2023
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.