Container Image Scanning with Trivy

Josh Kasuboski
Posted on September 25, 2020
I wanted to have some peace of mind when running random container images. Trivy let's me scan them for common vulnerabilities.
Installing Trivy
You can find the Trivy repo on GitHub at aquasecurity/trivy. Installing with Homebrew is just brew install aquasecurity/trivy/trivy. Trivy is written in Golang so you just need to get the binary. They also have a magic script you can use
curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/master/contrib/install.sh | sh -s -- -b /usr/local/bin
Once you have trivy in your $PATH, you can run trivy and see the options. Trivy can do a number of scans: a remote image, local filesystem, or a remote repository.
The various options make it easy to scan code repos, images before they are pushed, and third-party images you want to use.
Scanning an image
I use ArgoCD and had to use an image other than the official one since I wanted multi-arch support. This saved me from having to build it myself which I've done in the past.
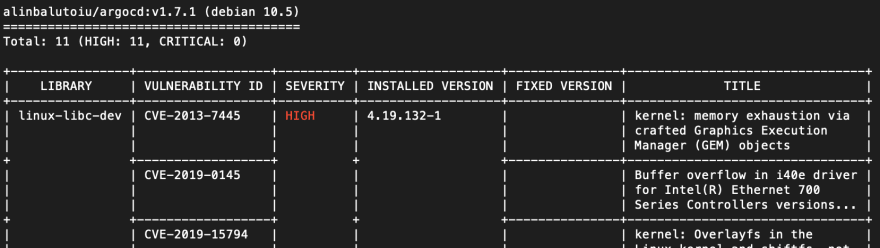
I wanted to scan this image for vulnerabilities (the build is open source, but you never really know). With Trivy this is as easy as trivy image alinbalutoiu/argocd:v1.7.1. It will download (and cache) the vulnerability database and then pull and scan the image. It then outputs a nice table of vulnerabilities as seen below. You can also filter by severity and ignore unfixed.
Next Stop CI
This is great for testing an image ad-hoc, but I want to add this to my gitops repo so that all images are scanned periodically. There is already a Trivy GitHub Action, but I think it's intended more for images you are building.
I also want to run something in my cluster that will periodically check all images that are running. Something like starboard could be the beginning of that.

Posted on September 25, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.