Mohmed Ishak
Posted on January 4, 2022
Read full article for free on Aviyel here.
Termux, as a mobile app has gained recent traction in the last few months. Today, we’re going to test it using another app called MobSF (Mobile Security Framework) by dragging and dropping that app into MobSF and viewing key insights on Termux’s security, because the truth is, modern developers don’t really know how to efficiently view security vulnerabilities in their apps, and the only way we secure our apps usually (including me) is by writing some test cases, not committing environment variables to the repository.
What is Termux?
Termux is just an example of an Android app that we’re going to test, and this means you can replace it with any app you want like WhatsApp APK or anything. Termux is an Android terminal emulator and Linux environment app that works on your Android. If this sounds confusing, basically using a computer, you always have access to powerful terminals, but not from a mobile phone. Because of this, you cannot perform useful tasks that you would do from a computer using a phone such as using SSH to connect to a remote server. Here are some of the cool features of Termux which are advertised:
- Secure: you can securely access remote servers using SSH client from OpenSSH from your smartphones. Basically, your phone now has access to a powerful terminal through emulation.
- Feature packed: you have full control over which terminal you want to use such as Bash, Zsh, and so on.
- Customizable: Termux is already powerful by default but they don’t stop you from installing additional packages/libraries from the APT package management system from some popular distros of Linux such as Ubuntu and Debian.
- Very flexible: you can connect a Bluetooth keyboard to your phone and use keyboard shortcuts that you would use on your computer and all the commands will work.
If you’d like to know more about Termux, you can view the homepage here. The homepage looks simple, but when you click the link that will redirect to its wiki, you’ll access more pages and you’ll realize how powerful Termux is in though. But remember, the goal of this article is to teach you how to test any app using Mobile Security Framework (MobSF), so let’s take a look at that.
What is Mobile Security Framework (MobSF)?
Mobile Security Framework or MobSF is an automated and comprehensive open source mobile security tool (Android/iOS/Windows) that can check vulnerabilities for your application and do everything of that nature easily. This includes things like penetration testing, malware analysis, and so on. It’s a very complex app but so easy to use. It supports mobile app binaries such as APK, IPA, and so on so all you have to do is just drag and drop your mobile app file to this tool and it’ll do all the magic of finding security vulnerabilities behind the scenes. Why is this cool and useful? Because honestly, modern developers (including me) tend to learn the shiny new mobile development technologies such as React Native, Flutter, and so on, but they don’t know how to test the security of their app. Sure, they do know how to make secure decisions every now and then such as not committing secrets to repositories, securing databases, and so on, but still, that’s just the basics. MobSF helps you by identifying all kinds of security vulnerabilities which I’ll explain later in this article. For now, let’s just get started with installing it.
How to Install MobSF?
There are two ways to install it, one is using the manual method (advantage: you can perform dynamic analysis which is more relevant, disadvantage: setting it up on your machine may be slightly complicated). The next is by using Docker (advantage: you just need to install Docker and type in a command and everything that MobSF needs to run on your machine will be automatically downloaded without you having to do anything and MobSF will be available to access on your browser in localhost:8000, disadvantage: you cannot perform dynamic analysis using real-time data).
I will show you both ways. First, the manual way. If you want to run MobSF this way on your machine, you need to install other technologies in your machine depending on your OS.
- Therefore, download the required technologies from here.
- Next, clone the repository which is available on GitHub (just open a terminal in your computer and type: git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git.What the above command means is that you are cloning (means downloading)
- MobSF which is hosted on GitHub to your machine.
- Next, get into that folder using this command: cd
- Next, run setup.bat file by typing: setup.bat
If you face any errors, don’t worry. You can Google them or just read the official instructions/docs here. MobSF will be available in localhost:8000 on your browser (I mean just type localhost:8000 in the URL bar and you’ll be able to access it).
Remember I told you there are two ways to install MobSF? Above is the first way and the second way is to use Docker. Although both of these ways have their own disadvantages, I prefer to use Docker because I’m just used to pulling Docker images and honestly, there’s a million percent better chance that you will be able to run software using Docker rather than trying to run it manually.
- To run using Docker, just make sure you have Docker installed first. If not, install it here.
- Now, make sure the Docker engine is turned on. If you don’t know how, you can search it on Stack Overflow, but I’m sure you know about it.
- Now, type:
docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
With this command, Docker will pull the MobSF image from Docker Hub and run it in your machine. If you don’t know Docker, let me explain it in a way that you’d understand. Basically, you just have to install Docker and type the above command. Then, Docker will automatically install MobSF, Git, Python, and every tech it is dependent on without you having to download them. Now, you just need to head over to localhost:8000 to access MobSF.
How to Analyze Security Vulnerability with MobSF Now That You Are Running It on Termux?
First, we want to test Termux, right? So, download Termux here. You don’t have to install it on your mobile phone. Before I explain further, I want to say that the version of Termux I downloaded for the sake of writing this article is version 0.117 and the version of MobSF is version 3.4.5 (beta).
Just to make sure we’re on the same page, once you launched MobSF earlier, you should have seen something like the screenshot below on your browser (URL: localhost:8000).
Actually, there’s only one step here. Just drag and drop that APK file to MobSF and wait for the report.
How to Read Security Report from MobSF?
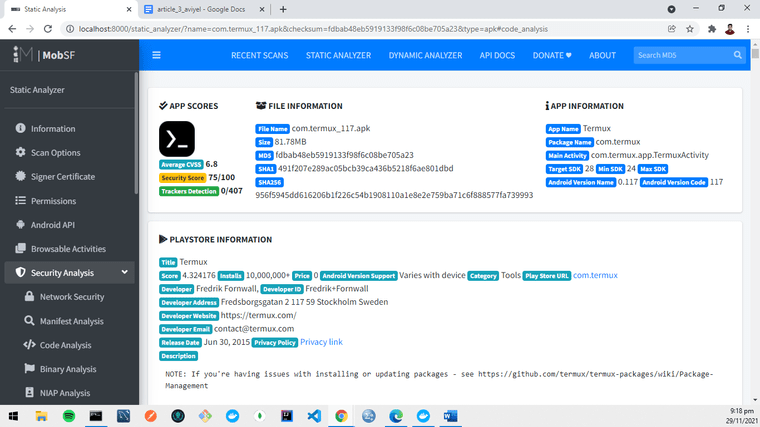
If you followed all the instructions, you just made a static analysis which is so powerful. But, if you’d like to see more real-time analysis you can try dynamic analysis after reading this article by following instructions here. Anyway, here’s how your screen will look like after the static analysis.
You may click these individual tabs to your left and I’m sure you’ll be able to understand it because of how descriptive MobSF is, but now I’ll just highlight some of the important stats.
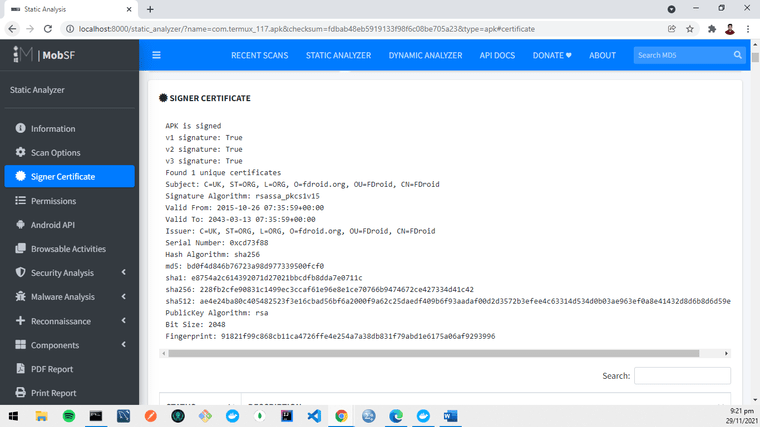
- First, signer certificate. It shows whether the APK is signed or not, who signed it, serial number, and so on so you’ll know who developed it and related data.
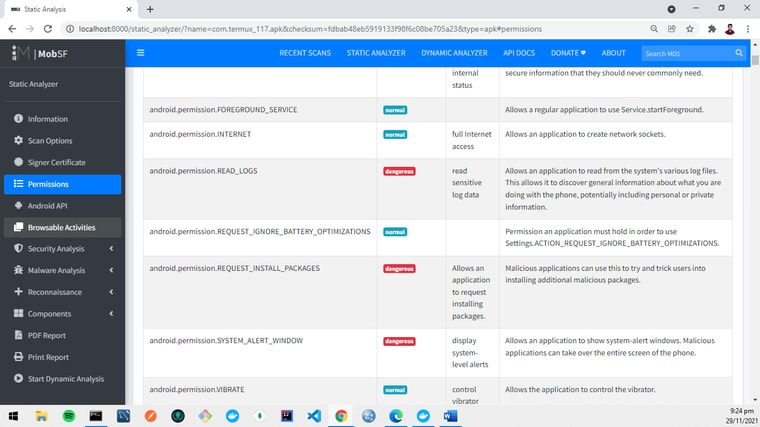
- Next, this is a serious one. It tells you all the permissions this app would ask alongside the severity. Not sure if you can read the small texts below, but based on the report generated for Termux version 0.117 by MobSF version 3.4.5 (beta) as in the screenshot below, one of the permissions is
android.permission.REQUEST_INSTALL_PACKAGESwhich allows an application to request installing packages. If users allow it, Termux can try and trick users into installing additional malicious packages. If you think I explained all this info at this point from my knowledge, that’s not right. Actually, all these are explained in the report.
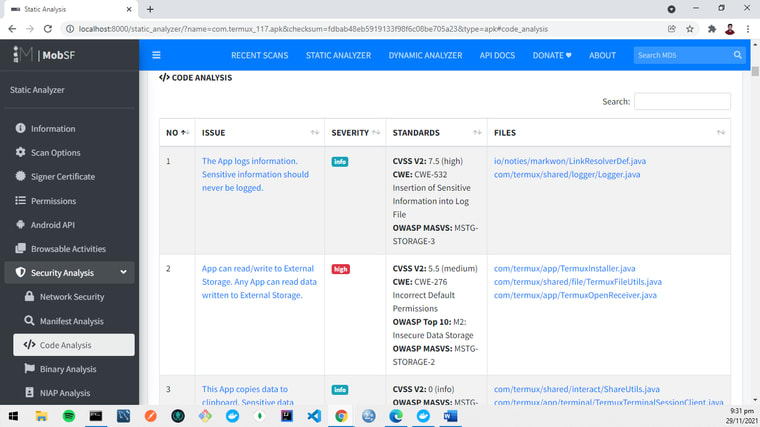
It will also check your code line by line and analyze it, and tell you what’s wrong in terms of security. As in the screenshot below, it says that “App can read/write to External Storage. Any App can read data written to External Storage”, and the severity is high. It even tells you which file(s) contain this vulnerability.
- There are so much more insights MobSF gives you such as binary analysis, APIs that are used, hardcoded secrets, and so much more. I leave it up to you to explore by yourself because it’s pretty easy since all you need to do is to click those tabs on your left and check the stats one by one and mark the ones you need the most for your future use.
So that’s all about MobSF. All while, honestly (like super honestly), I didn’t know how to test the security of the apps I’ve built, but now things seem to be so much easier with MobSF. I’ll just let MobSF do all the hard work of finding vulnerabilities while I’ll focus on building features for my apps. As for Termux, it can do so much more and if you’d like to know more, you can read a discussion on Termux I stumbled upon earlier here.
The conclusion is, just because you might not know how to test securities in your mobile apps, don’t skip this part because this is too crucial. Even if you know how to test the security of your mobile apps, you can still use MobSF to test your apps as the developers have done the hard work (you don’t need to) to implement a whole lot of features that will be helpful in testing mobile app security. If you like this article, do share it with your friends cause MobSF and Termux are so cool and it only takes you a couple of seconds to share it with your friends in exchange for the amazing exposure I’ve given you to test the security of your mobile apps.

Posted on January 4, 2022
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.