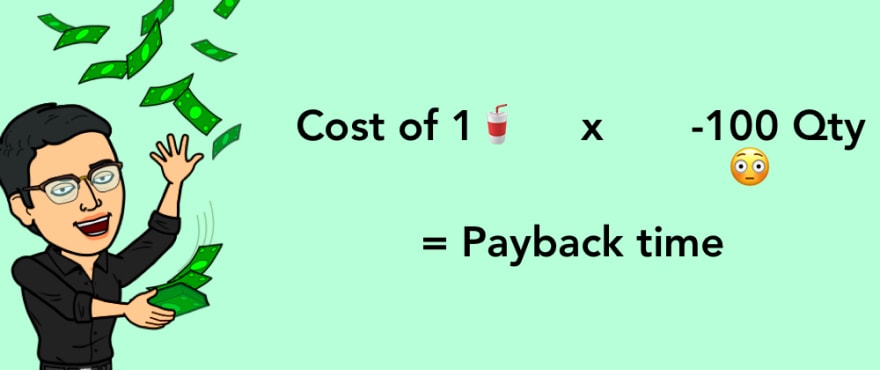Make yourself rich by hacking this juice shop 💵

Dennis Mathew Philip
Posted on June 29, 2020

As a business owner or as a professional, getting your website hacked is no fun. How do hackers do this?
Through this article, I would like to bring your attention to an exciting topic - Web Application Security.
Knowing some of the techniques will help you design a reasonably "secure" web application. Before a release, attacking your own application will help mitigate some of the vulnerabilities.
📖 Learn the techniques
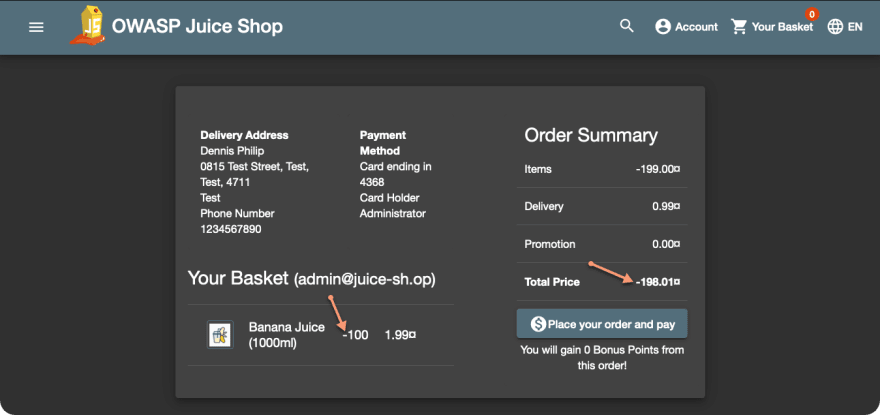
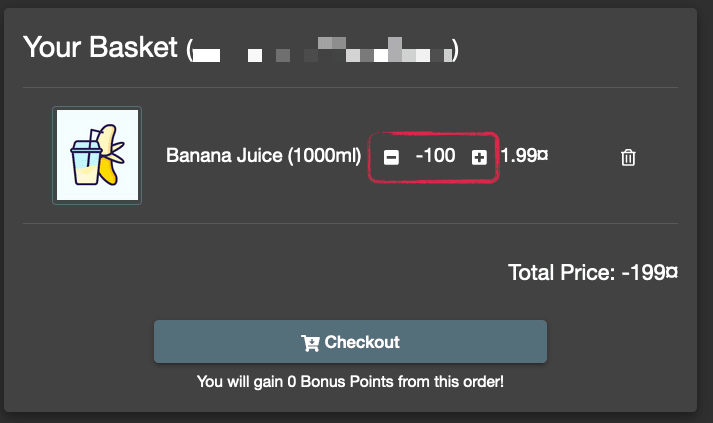
Pay attention to the screenshot below. You may have placed eCommerce orders for 1 or more items. Have you thought what would happen when an order is placed with a quantity of -100 items? This order will return money to the shopper's credit card!
Do you want to be that devastated owner of a business that "pays" money for no juice sold?
You may have read or heard about SQL injection, Cross-site scripting, Cross-site Request Forgery, and other popular attacks.
Let's learn swimming, by actually being in the water.
🥤 Set up your juice shop
Before we start, we need an online juice shop - an insecure vulnerable web application to learn some basic and advanced attacks. Luckily there is one that exists.
Assuming you have NodeJS installed:
- Clone the repository
- Install the project dependencies
- Start the server.
git clone https://github.com/bkimminich/juice-shop.git
npm install
npm start
Your juice shop is up and running.
Navigate to http://localhost:3000
💵 Make yourself rich
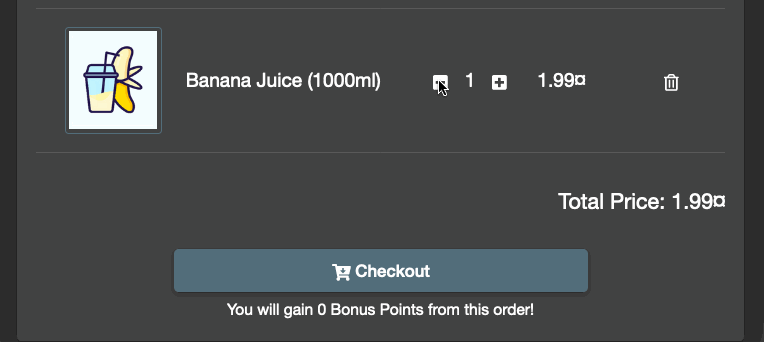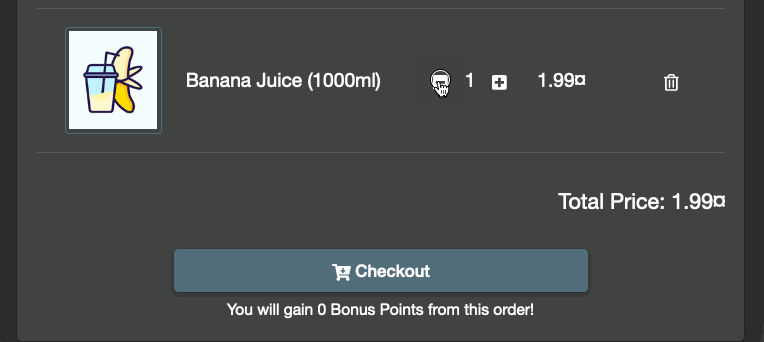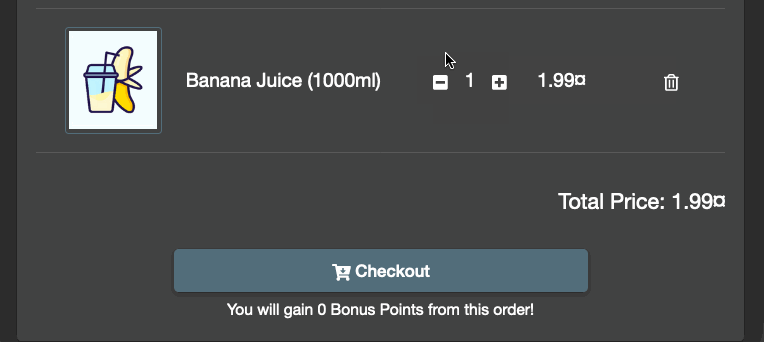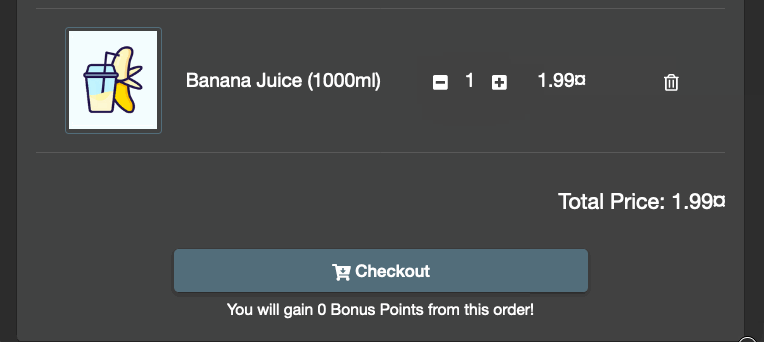
The user interface will let you pick only 1 juice.
mmmmm... What about the API?
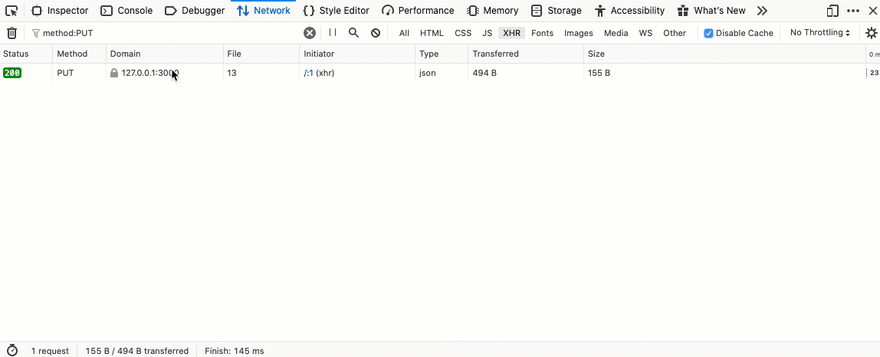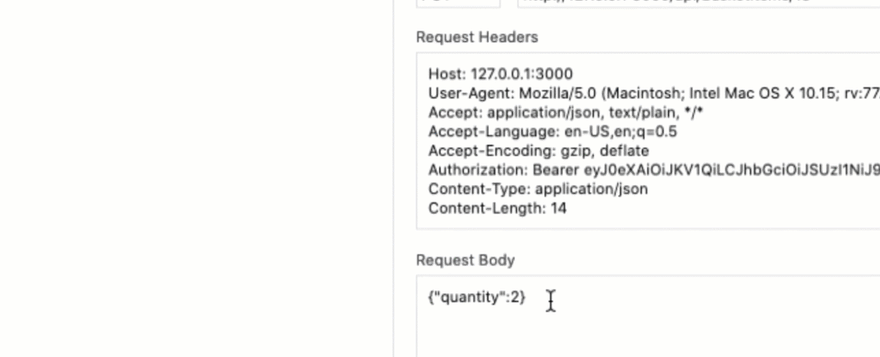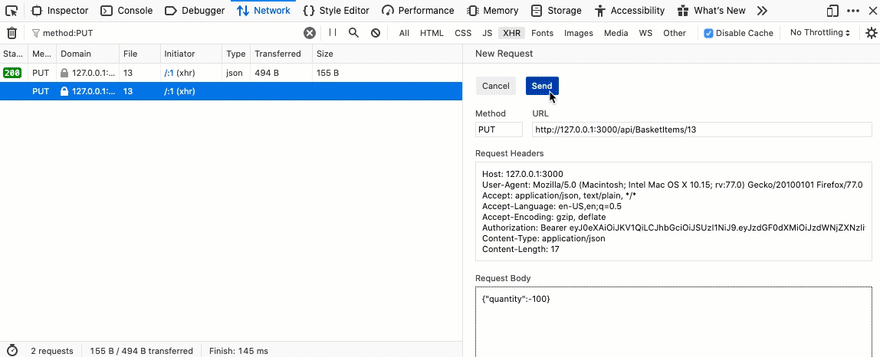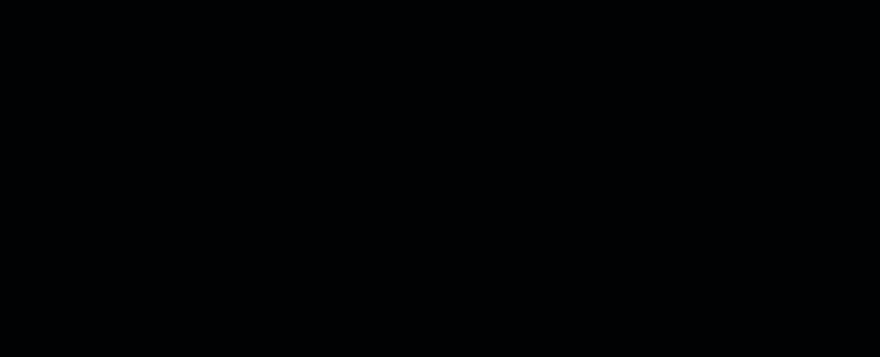
Open the browser developer tools, firefox will let you resend a request quite easily.
That works 🎉.
Wait, what just happened? We used the API to post the quantity of juice as -100.
Placing this order will pay you $198.01 from the juice vendor!
Obviously, this is a hypothetical situation. The web application is mindfully crafted to be insecure to show the point.
🧊 The tip of the iceberg
"OWASP Juice Shop" is an application that provides awareness for security risks that potentially exist in modern web applications.
This is only one of the many challenges in the set of OWASP Juice Shop exercises. See all the challenges and work through each of them. You will be delighted to learn some of the popular techniques to
- Access confidential files on the server
- Decrypt coupon codes and get an 80% off an order
- Login as a different user without knowing their password
Start here: https://bkimminich.gitbooks.io/pwning-owasp-juice-shop/content
This is definitely one of the best free security training for you out there. Let's create secure web applications together.
🙏 Credits
Björn Kimminich for creating and maintaining this project for the world to learn.
Please find my other writings here:
- One side rounded rectangle using SVG
- What makes these borders beautiful?
- Automated End to End tests made easy
- Automate your node dependency update
- Visual Studio Code — Debug Mode
- I want TypeScript to succeed.
- What’s in my laptop?
- CoffeeScript’s most loved feature soon in JavaScript
- Extend your wireless signal with an old router

Posted on June 29, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.