
Eng Soon Cheah
Posted on April 13, 2019
Configure endpoint protection
- The information under Endpoint protection issues can help you create a plan to address any issues identified
- Security Center reports the following endpoint protection issues:
- Endpoint protection not installed on Azure VMs
- Endpoint protection not installed on non-Azure computers
- Endpoint protection health issues
- Security Center presents the endpoint protection issues as a recommendation

Configure centralized policy management by using Azure Security Center
- By default, all prevention policies are turned on
- Enabling a prevention policy, such as OS vulnerabilities, enables recommendations for that policy
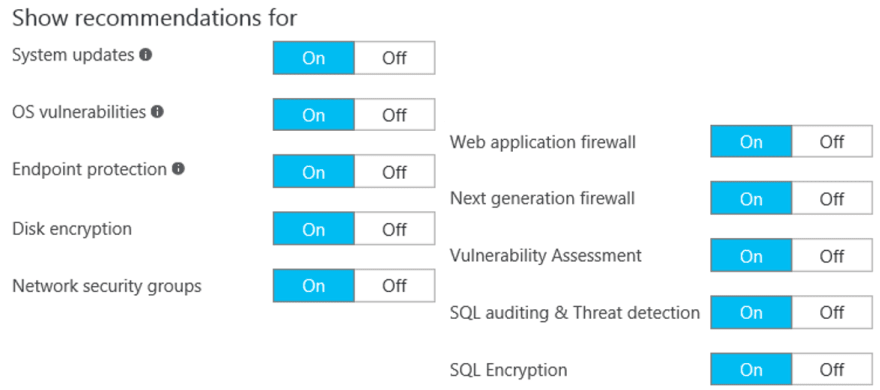
- You can enable or disable recommendations for:
- System updates
- OS vulnerabilities
- Endpoint protection
- Disk encryption
- Network security groups
- Web application firewall
- Vulnerability Assessment
- NGFW
- SQL auditing & Threat detection
- SQL Encryption
Configure vulnerability scanning and policies
- Azure Security Center provides you with a centralized view of your Azure resources and their active security state
- It provides integrated security monitoring and policy management across your Azure subscriptions, and works with a broad ecosystem of security solutions
- Security Center delivers these solutions through the following capabilities:
- Prevention
- Detection
- Response
- A security policy defines the set of controls that are recommended for resources within the specified subscription or resource group
- In Azure Security Center, you define policies for your Azure subscriptions or resource groups
- Enabling Security Center and data collection enables all the security policies by default
- Three policy components include:
- Prevention policy
- Email notifications
- Pricing tier

Configure JIT VM access by using Azure Security Center
- RDP brute-force attacks are the attack method most commonly used to access Azure VMs
- To blunt RDP brute-force attacks, you can:
- Disable the public IP address and use a connection method such as P2S VPN, S2S VPN, or Azure ExpressRoute
- Require two-factor authentication
- Use complex passwords
- Limit the time that the ports are open
- Azure Security Center implements the last method by using JIT VM access
- By enabling JIT VM access for your VMs, you can create a policy that determines the ports to help protect, the time ports should remain open, and the approved IP addresses that can access these ports
💖 💪 🙅 🚩

Eng Soon Cheah
Posted on April 13, 2019
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.
Related
azure Securing Your Azure Cloud Environment with Application Security Groups (ASGs)
November 28, 2024
undefined Steps to Optimize Your Infrastructure During Azure Migration and Achieve Maximum Efficiency
November 26, 2024
