Going Dark

bkocik
Posted on January 2, 2020
This post was brought over from my Medium account, because they've started asking me to pay to read content there. It was originally published on May 29, 2017.
Important disclaimer: I'm writing this to give you advice, not to sign up to provide technical support in perpetuity for your use of any of the products or information you find here. That's just not our arrangement. Read docs, use Google, and get help from the providers you choose. They're better at it than I am, anyways.
Recently some of my less nerdy friends and family have asked me for help with being more secure in their day-to-day online lives. Rather than answer them individually, I decided to write this quick guide to patching up some of the larger holes most of us tend to have in our digital privacy fences.
I'm not here to convince you of why you should do this. Unless you live in a very deep hole you've no doubt heard about the impending death of net neutrality, the FCC rolling out the red carpet to allow your ISP to sell information about your online activities to the highest bidder, and repeated massive data breaches. There are many reasons to want to insulate yourself and your data- insofar as we can. If you're not already convinced that you should be worried about privacy and security, nothing I say about that is likely to help. If you're already on board, here are some basic steps you should take. Like, right now.
Your Browser Probably Sucks
First things first: If you're going to keep using Internet Explorer, or even the new Edge browser, no one can help you. I am not going to go into a long discussion of what is or isn't wrong with the Microsoft browsers; that topic is covered in length all over the web and if you're interested you can use Google to find your way to those debates. I'll just say this: If you're going to continue to use IE or Edge, then none of the rest of this matters and you should probably go do something else with your afternoon and forget the rest of what I was going to say. If you use one of those browsers, no one can save you. Whatever you do to try to improve your security, Internet Explorer/Edge will find a way to screw it up for you. That's what it does.
What I Do
I switch back and forth between Vivaldi and Opera, and I use Chrome for work and a lot of my development. All of these browsers are based on the open source Chromium browser. I would use Vivaldi full time if I could, but it's pretty new and it isn't ready to handle all of the web (which is why I sometimes fall back to Opera).
What You Should Do
Just get Chrome and be done with it. It's one of the world's most popular browsers, and when web developers are creating their sites and apps Chrome is usually the first browser they make sure their stuff works in. Install it, use it, and forget everything else. You can even install it on your iPhone or Android device.
And Then
Install TunnelBear's blocker. TunnelBear is a VPN provider (you'll hear more about them below), but they also provide a really good ad, malware, and privacy tracking blocker extension for Chrome. It's free. Follow the link in the first sentence of this paragraph to learn more about what it is, why you want it, and how to get it.
Your Passwords Probably Suck, Too
Don't feel bad. Mine did, too, and I know better. Or, I should.
For years I had a small handful of 3 or 4 reasonably cryptic passwords that I re-used all over the web. I'm embarrassed by this. The reason the Yahoo! data breach was such a big deal was because of people like me. Account details and passwords from that breach were available for sale online for a long time before anyone at Yahoo! knew about it and sounded the alarm. So if you were lazy like me and you'd used the same password there as you did at 100 other sites, anyone who came into possession of that information could almost certainly impersonate you and get into your private data all over the Internet.
What I Do
I used to think that password managers were for average users, not seasoned technologists like me. How irresponsible and lazy to store all of your passwords in some 3rd party app just so that you don't have to type them! It turns out I was way wrong (I'm wrong a lot, just so we're clear). Using a good password manager, as it happens, is actually a pretty good idea, and in the end will help you stay far safer than without. This is because they make it easy to have really good, strong, unique passwords all across the web, and the better ones do a stellar job of keeping your passwords safe. They're not as prone to hacking as you might expect; not nearly. If you're using one of the better password managers that uses strong cryptography in a sensible way, then someone who wants your password (and isn't dumb) is not going to try to get it from your password manager. That would be a waste of time. They're going to find some other way to get it. In other words, your password manager is going to be a strong link in the chain, not a weakness. Most people who are knowledgeable about security tend not to argue about whether or not you should use a password manager, but instead will just have heated debates about which one you should use.
I'm not going to write a comprehensive review of every password manager out there. I'm going to tell you a little bit about three of them.
I started off trying out Lastpass and Dashlane, and eventually settled on Dashlane. Both of them are very good solutions, I just liked Dashlane a little bit better. Since then I've changed my mind and moved over to 1Password.
What You Should Do
If you just want a simple recommendation, I say get Dashlane. It's free if you want to use it on only one device, which is a fancy way of saying it isn't free. To get cross-device synchronization, right now it's $39.99 a year.
LastPass is free to use across devices, and is only $12 per year for their paid service which gets you better support and a few more features that you probably don't need. It's a good bargain option, and there's nothing wrong with it, but I found Dashlane easier to use and a little more reliable in its behavior. For the extra money, I think it's well worth it. Being reliable and easy to use likely means you'll keep using it instead of getting frustrated with it and going back to bad old habits. But if you really need to save that money, get LastPass. All of these products also have browser extensions to automatically fill out login (and other) forms on the web, and they all offer iOS and Android apps.
So why am I using 1Password but not recommending it for you? Those are two questions. The answer to the first is that I love how transparent and accessible the staff at AgileBits (the company that makes it) are, and I appreciate the amount of thought they've put into the security of their product. As an example, customers have been asking them to implement multi-factor authentication for years and they haven't done it (this was why I didn't consider them when I was choosing a password manager), but it turns out they haven't done it for very good reasons: Given how their product works, MFA would really add almost exactly nothing to the security of the product, but would vastly increase the likelihood of customers becoming locked out of their data forever (and, as they point out, data security and data availability are inextricably linked; there's a good case to be made that, in light of that, MFA would make the product less secure by increasing the risk of your data becoming unavailable to you). AgileBits refuses to engage in "security theater" in order to decorate sales brochures, and I love that about them. As to the 2nd question, I'm not recommending it simply because it's a little bit harder to use. It gets in your way more. With Dashlane and LastPass you rarely have to type your master password (the one that locks away all of your other passwords), and most of the time they'll automatically fill in login forms for you without your intervention. With 1Password I have to type my master password several times a day because it likes to lock itself when I'm not active for a few minutes, and to get it to fill in a form I have to ask it to. To me, these are non-issues, but if you want good security that's mostly in the background and out of your way, LastPass and Dashlane will each give you that. They're both excellent products. Don't let the fact that I'm switching to 1Password make you feel as though there's something wrong with LastPass or Dashlane and you should follow my lead. You can if you want, but if you want easier, you shouldn't.
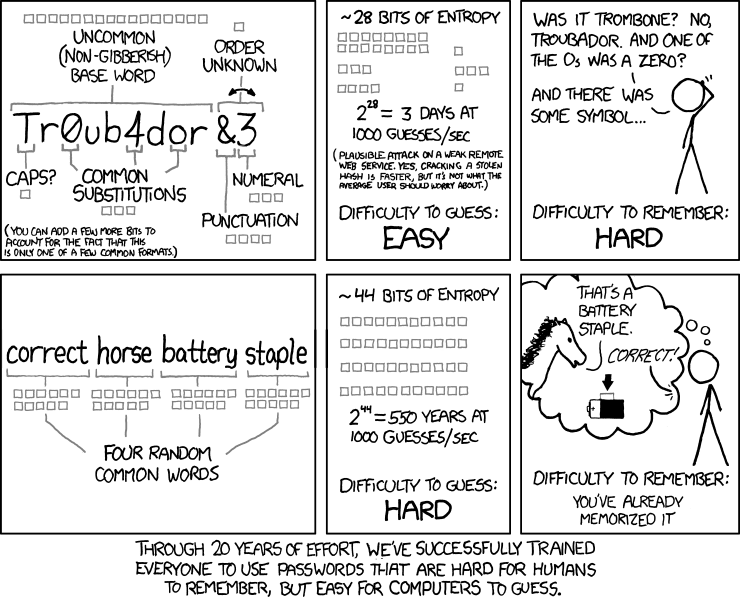
Now Make a Good Master Password
Regardless of which password manager you settled on, the next step is to create a really good, really strong password that you can remember. Start by forgetting everything people like me have been telling you about good passwords:
Your master password should look a lot more like "correcthorsebatterystaple" than "Tr0ub4dor&3." One of my passwords is 57 characters in length (which, for security reasons, I really shouldn't be telling you) and I have no trouble remembering it, and only occasional trouble typing it. For a great guide to creating a strong master password that you won't forget, take this advice from AgileBits. Seriously, go read that and then come back. (Did I mention I really like and respect those folks?)
Now Fix All of Your Other Passwords
Actually there's a step right before this one if you've been storing your passwords in your browser: Import them. Both LastPass and Dashlane have the ability to import passwords from at least some browsers. Consult their documentation for help; I can't really walk you through it here, and they've already done a good job of creating step-by-step guides so there's really no reason for me to. You're going to have to do a little bit of legwork here. Google can help you find the way. Once you've safely imported them into your shiny new password manager, delete them from your browser. If you've been using Chrome to store them and are logged into your Google account for synchronization, be sure to go to https://www.google.com/settings/chrome/sync and use the reset button to delete them there, too. Also don't forget to turn off synching in your browser or it will put them right back.
Yep, it's a pain in the ass. It still needs to be done.
LastPass and Dashlane both also have neat tools for telling you how secure (or not) your passwords are. They'll look at password length, complexity, and most importantly, re-use. At first they're going to make you feel bad about yourself because your passwords are not long or complex, and you've probably got a lot of repeats. Don't worry about it, that's why you're here, and that's why you installed them.
Use their built-in tool to take an honest look at just how bad your password habits were (because now you're developing new, good habits) and also to fix the problems. Both of them have the ability to automatically change your password to something more secure on many popular sites. In my experience, Dashlane is better at this than LastPass. For every imported password that your password manager doesn't like, go change it. Let your password manager generate a new password for you - you don't have to remember it (I don't know most of mine). Consult their documentation for how to use their auto-change features, as well as for how to get them to generate new passwords and save them for you. You really should spend some time getting to know how to use your password manager. It's an important tool and it won't have much of a learning curve.
This part is also a pain in the ass. Do it anyways.
Well That All Sucked, What Else Can I Do That's Awful?
Honestly, switching to a good browser, installing and using a password manager, and updating all of your passwords on the web to good, strong passwords with no re-used passwords is at least 90% of the battle. If you did those things, congratulations, you've made huge strides in protecting your online presence and identity.
But there's more you can do if you want to. One of the more important ones is:
Turn On MFA Everywhere You Can
MFA stands for multi-factor authentication. In short, when you log into anything, the fact that you knew your username is a factor - although it's usually not counted as one because it's usually not a secret. That you knew your password is usually the only factor in proving that you are who you say you are, so just having a username and password to a site is often considered to be single-factor authentication. On many sites, you can have more factors because they support 2FA (which you may have guessed stands for 2-factor authentication), or, more generically, MFA.
The easiest way this usually works is with sites like Facebook and Twitter, who will, if you want, send you a text message containing an additional code that you must type if you log into their sites from a browser or device they haven't seen before. This means that if someone actually gets hold of your Twitter password, for example, they'll head on over to Twitter, type in your username and password, and on the next screen they'll see a little box where Twitter is demanding that they also provide the code. The code that Twitter just sent to you. The code that Twitter did not send to them. Now they're stuck (and as a bonus, you now know that someone knows your Twitter password and you should go change it using LastPass or Dashlane). That code is the 2nd factor.
What I Do
I have multi-factor authentication turned on for every site and product I use that supports it. I own a Yubikey, which is a hardware-based security token. For sites that support that, when I log in I have to type my password (actually I don't, because I use a password manager) and then I have to plug the key into a USB port on my computer to complete the authentication process. This is pretty serious security. If you don't physically possess my Yubikey, you're not getting into those accounts - at least not through the front door.
I also use Google Authenticator, which is a time-based one-time password (TOTP) generator (Update: I have switched to using 1Password's built-in OTP functionality. Google's is still a perfectly good choice, though). Despite its name, it works with a lot more than just Google accounts. It actually works with any site that supports TOTP software, and I use it with a ton of them. For those accounts, if you don't have physical possession of my phone you're not getting in the front door, either.
For some other accounts that support SMS-based one-time passwords, I use that. This is the easy way that doesn't require you to buy hardware or install software. Twitter, Facebook, and others support this (and other) methods.
What You Should Do
For every site you can think of that matters to you, go search Google for "sitename multifactor authentication." The results should tell you two things: Whether the site supports MFA, and if it does, how to turn it on.
You should.
What About My Data In Motion?
To be fair, if you already know the difference between "data at rest" and "data in motion" then you probably didn't need any of this advice. If you don't know, and you care, here are two quick definitions:
Data at rest: Stored data, like files on your hard drive, or passwords. Data in motion: Data that's being transmitted, like browser traffic.
What we've done so far has been focused on your data at rest, but the net neutrality and ISP firesale of your personal information are matters of data in motion. There is something you can do about these things.
What I Do
I use a virtual private network (VPN) service. In short, this allows me to set up a single connection to a VPN server somewhere (this is called my tunnel), and send all of my traffic from my computer through that tunnel. This means my ISP has no real knowledge of what I'm doing, because instead of seeing a connection to Google, and another one to TechCrunch, and another to my email provider, and so on, all they see is that single tunnel connection. Importantly, they can't see inside of it. Really, no one can - except for my VPN provider. This means my ISP can't sell my data, and they can't selectively throttle my connection to any sites or services that haven't paid them for the privilege of not having that done to them. I have a VPN client installed on my computer, I have an encrypted proxy extension installed in my browsers (for times when I'm not on the VPN, like when I'm at work), and I have a VPN client installed on my phone. All of my traffic travels through opaque, encrypted tunnels. I'm subversive like that.
What You Should Do
I bet you think I'm going to tell you which VPN provider among the dizzying array of choices out there is the best. I have bad news: There is no best. There are so many VPN providers in the market today with so many similar and not-so-similar features, specious claims, and varying levels of integrity and trustworthiness that it's really, really difficult to pick one.
I won't tell you which one is the best, I'll just tell you that if you want a VPN I think you should probably use TunnelBear. There, that was easy.
They'll give you 500Mb per month of free data, which isn't very much, so you're probably going to have to buy a subscription. (Sorry, not everything is free, and sometimes software and services are worth paying for.) If you want something a little more advanced, consider NordVPN or maybe VyprVPN.
Trying to evaluate VPN providers - and then defend your evaluation - is an exhausting task. It's so overwhelming that just thinking about trying to explain why I like those three makes my head hurt, so I'm not going to. I'll just say this: As far as I can tell, those three are pretty damn good and the companies behind them seem decent. TunnelBear is the simplest one to use and they're known for having outstanding support, so that's my recommendation.
Is That Everything?
Of course it isn't, but it's a hell of a start. When it comes to protecting our data and accounts, we're usually our own worst enemies. I'll say it again because it can't be overemphasized: Using a password manager to easily keep your passwords strong and unique is an enormous step toward keeping people out of your business. If you do nothing else I've talked about here, do that. Seriously.
One other thing I have done is encrypted my entire hard drive using macOS's built-in FileVault utility (know that if you have an iPhone, its data is already encrypted; you can send Apple a thank-you note for that). If you use a Mac, you should do that, too. If you use Windows, you should…I don't know, stop? Windows is kind of a neurotic minefield of insecurity and vulnerability. It has issues, but I hear it's been working through them in therapy. I don't use it, so I don't really know anything about how people who do stay safe with it.
Maybe you can Google for that.

Posted on January 2, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.
Related

November 30, 2024