Cryptographic Foundations: A Comprehensive Introduction

Binoy Vijayan
Posted on January 12, 2024
Cryptography is the science and practice of securing communication and data from adversaries. It involves techniques and methods for protecting information by transforming it into an unreadable format, and it plays a crucial role in ensuring the confidentiality, integrity, and authenticity of data.
Core Objectives of Cryptography:
Encryption for confidentiality
Encryption transforms plaintext into cipher text, which can only be deciphered by those with the appropriate key.This ensures that unauthorised parties can not understand the content of the encrypted information.
Examples
Full Disk Encryption (FDE) - BitLocker (Windows), FileVault (macOS), LUKS (Linux).
File and Folder Encryption - VeraCrypt, AxCrypt, Windows EFS (Encrypting File System).
Email Encryption - Pretty Good Privacy (PGP), S/MIME (Secure/Multipurpose Internet Mail Extensions).
Database Encryption - Transparent Data Encryption (TDE), Always Encrypted (Microsoft SQL Server).
Communication Encryption - Transport Layer Security (TLS) for web traffic, Secure Shell (SSH) for remote access, Virtual Private Networks (VPNs).
Cloud Storage Encryption - Client-side encryption in cloud storage services, such as Tresorit or Cryptomator.
Instant Messaging Encryption - Signal Protocol (used by Signal, WhatsApp, and others), Off-the-Record Messaging (OTR).
Voice and Video Call Encryption:- Secure Real-time Transport Protocol (SRTP) for VoIP calls, end-to-end encryption in video conferencing tools.
Secure File Transfer - Secure FTP (SFTP), HTTPS for secure file downloads.
Container Encryption - Docker Content Trust, encryption in virtualisation technologies.
Hash function for Integrity
In the context of computer science and cryptography, a hash is the result of applying a hash function to a piece of data, typically a message or a file. A hash function takes an input (or "message") and produces a fixed-size string of characters, which is commonly a hexadecimal number. The output, often referred to as the hash value or hash code, is unique to the specific input data.
Cryptographic hash functions are often used to generate a fixed-size digest (hash) of data. This hash can be compared to verify data integrity and detect or prevent unauthorised modifications to the data.
Examples
SHA-256 (Secure Hash Algorithm 256-bit):
Produces a 256-bit (32-byte) hash value.
- Example Usage: Cryptographic applications, blockchain technology, digital signatures.
SHA-3 (Secure Hash Algorithm 3):
A family of hash functions with variable output sizes (224, 256, 384, 512 bits).
- Example Usage: Cryptography, digital signatures, data integrity verification.
MD5 (Message Digest Algorithm 5):
Produces a 128-bit (16-byte) hash value.
Example Usage: Historically used for checksums and data integrity, but now considered insecure for cryptographic purposes.
SHA-1 (Secure Hash Algorithm 1):
Produces a 160-bit (20-byte) hash value.
Deprecated for cryptographic purposes due to vulnerabilities.
Whirlpool:
Produces a variable-length hash value, up to 512 bits.
Example Usage: Cryptography, checksums.
When using hash functions for data integrity, it's important to choose an algorithm that meets the security requirements of the specific application. For cryptographic purposes, prefer SHA-256 or SHA-3 over MD5 or SHA-1, which are considered insecure due to vulnerabilities. Always use reputable libraries and implementations for hash functions to ensure their correctness and security.
Digital Signatures for authentication
Digital signatures are cryptographic techniques used for authentication and ensuring the integrity of digital messages or documents. They involve the use of public-key cryptography, where a pair of keys (public and private) is used to sign and verify the authenticity of a message.
Examples
RSA (Rivest-Shamir-Adleman):
One of the earliest and widely used public-key crypto-systems.
Application: Digital signatures, secure communication, key exchange.
DSA (Digital Signature Algorithm):
A standard for digital signatures, specified by the U.S. National Institute of Standards and Technology (NIST).
Application: Digital signatures in various protocols.
ECDSA (Elliptic Curve Digital Signature Algorithm):
A variant of DSA using elliptic curve cryptography.
Application: Digital signatures, secure communication.
Digital Signatures for non-repudiation
Digital signatures play a crucial role in achieving non-repudiation, a security property that ensures that a party cannot deny the authenticity or origin of a digital message or document that they signed.
Examples
RSA (Rivest-Shamir-Adleman):
A widely used asymmetric encryption algorithm that can be used for digital signatures.
Application: Digital signatures, secure communication, key exchange.
ECDSA (Elliptic Curve Digital Signature Algorithm):
A variant of DSA using elliptic curve cryptography.
Application: Digital signatures, secure communication.
Types of Cryptography:
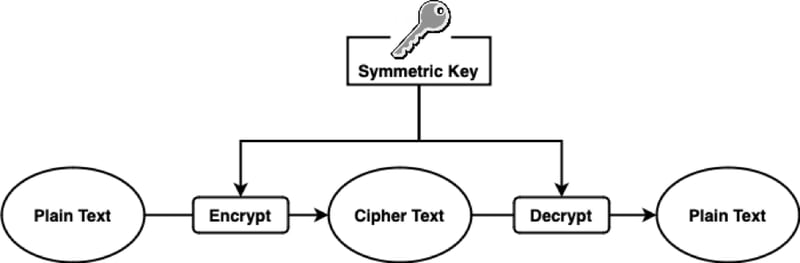
Symmetric Cryptography:
A single secret key is used for both encryption and decryption.
Efficient for large data, used in scenarios where parties can securely share a key.
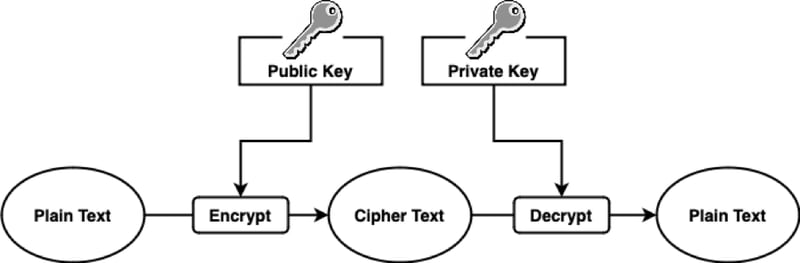
Asymmetric Cryptography:
A pair of public and private keys is used. The public key is for encryption, and the private key is for decryption.
Key exchange, digital signatures, and secure communication over insecure channels.
Hash Functions:
Converts variable-length input into a fixed-length hash value.
Data integrity verification, password storage, digital signatures.
Common Cryptographic Algorithms:
Symmetric Encryption:
- Advanced Encryption Standard (AES),
- Data Encryption Standard (DES),
- Triple DES (3DES).
Asymmetric Encryption:
- RSA (Rivest-Shamir-Adleman),
- Elliptic Curve Cryptography (ECC),
- Digital Signature Algorithm (DSA).
Hash Functions:
- SHA-256 (Secure Hash Algorithm 256-bit),
- MD5 (Message Digest Algorithm 5).
Applications of Cryptography:
Secure Communication:
HTTPS for secure web browsing, VPNs for secure network communication.
Data Protection:
Encryption of files, databases, and storage devices.
Authentication and Digital Signatures:
Verifying the identity of users, ensuring the authenticity of messages.
Secure Transactions:
Online banking, e-commerce transactions.
Challenges and Considerations:
Key Management:
Secure generation, distribution, and storage of cryptographic keys.
Algorithm Strength:
Regular evaluation of cryptographic algorithms for potential vulnerabilities.
Quantum Computing:
Theoretical threat to existing cryptographic systems due to their potential to break certain encryption algorithms.
Cryptography is a continually evolving field, with ongoing research to address emerging challenges and adapt to technological advancements. Its applications extend across various industries, providing a foundation for secure and private communication in the digital age.

Posted on January 12, 2024
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.