Cyber security essentials

Bilal Ahmad
Posted on December 4, 2021
Cyber security is the practice of defending computers networks, electronic devices and data from malicious attacks.
A cybersecurity framework is a collection of best practices that an organization should follow to manage its cybersecurity risk.
The goal of the framework is to reduce the company’s exposure to cyberattacks, and to identify the areas most at risk for data breaches and other compromising activity perpetrated by cyber criminals.
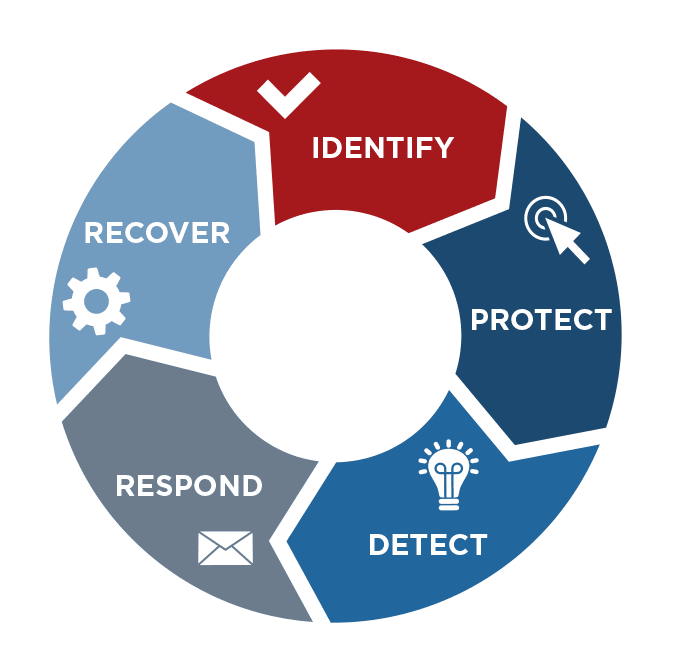
Cyber security framework works under 5 main functions:
- Identify : An understanding and identification of the cyber security risks.
- Protect : Measures to protect and maintain systems, assets and data.
- Detect : Processes to identify the occurrence of a cyber security event.
- Respond : Arrangements of detection of a possible cyber security event.
- Recover : Plans and restoration procedures to reinstate services.
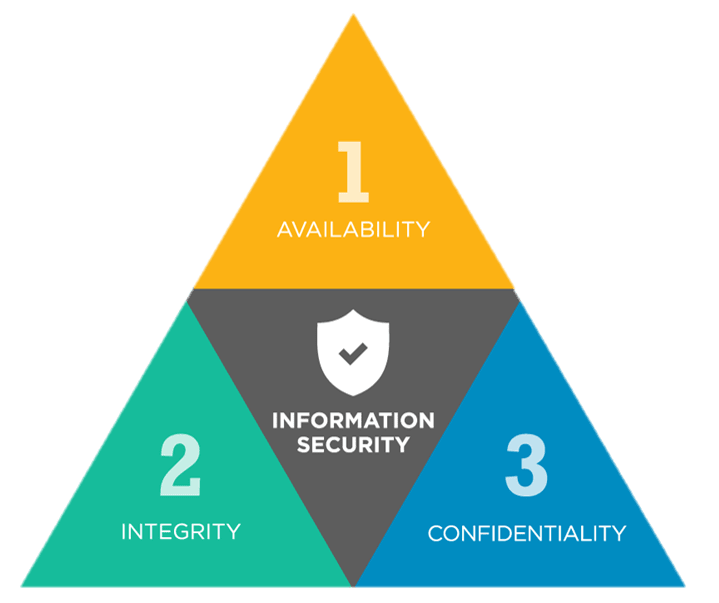
How to ensure that your information is secure? Well, Information security is based on CIA triad model. The CIA triad refers to an information security model made up of the three main components:
- Confidentiality : It’s ability of system to keep your data secret and private only to you.
- Integrity : A system’s ability to ensure that the information is accurate and correct.
- Availability : This means that the information is available to authorized users when it is needed.
A cybersecurity threat refers to any possible malicious act that seeks to damage data, steal data, or disrupt digital life in general.
Here are some cyber security threads that will cause cyber attack :
- Phishing : An email-borne attack that involves tricking the email recipient into disclosing confidential information or downloading malware by clicking on a hyperlink in the message.
- Social engineering : This technique is used to deceive and manipulate victims to obtain information or gain access to their computer. This is achieved by tricking users into clicking malicious links or by physically gaining access to a computer through deception.
- DDoS attacks : DDoS (distributed denial-of-service) attacks attempt to disrupt normal web traffic and take targeted websites offline by flooding systems, servers or networks with more requests than they can handle, causing them to crash.
- Malware : The term is used to describe malicious software designed to perform an attack on the device or server that downloads or runs it. Malware attacks can cause a corruption of data or even take down an entire system.
- Malware is a broad term used to describe any file or program intended to harm or disrupt a computer. This includes:
- Viruses : these infect applications attaching themselves to the initialization sequence.
- Worms : they don’t attack the host, being self-contained programs that propagate across networks and computers in order to overload an server.
- Trojans : it hiding inside a useful program with malicious purposes
- Spyware : a type of program installed to collect information about users
- Ransomware : An attack that involves encrypting data on the target system and demanding a ransom in exchange for letting the user have access to the data again. These attacks range from low-level nuisances to serious incidents like the locking down of the entire city of Atlanta’s municipal government data in 2018.
Experts estimate that a ransomware attack will occur every 11 seconds in 2021. (Cybercrime Magazine, 2019)
The average cost of a data breach is $3.86 million as of 2020. (IBM)
Data breaches exposed 36 billion records in the first half of 2020. (RiskBased)
Here are some historical data breaches:
- In 2020, a Twitter breach targeted 130 accounts, including those of past presidents and Elon Musk, resulted in attackers swindling $121,000 in Bitcoin through nearly 300 transactions. (CNBC)
- In 2020, Marriott disclosed a security breach impacted data of more than 5.2 million hotel guests. (Marriott)
- The 2019 MGM data breach resulted in hackers leaking records of 142 million hotel guests. (CPO Magazine)
- In 2018, Under Armor reported that its “My Fitness Pal” was hacked, affecting 150 million users. (Under Armour)
- In 2017, 147.9 million consumers were affected by the Equifax Breach. (Equifax)
- The Equifax breach cost the company over $4 billion in total. (Time Magazine)
- In 2017, 412 million user accounts were stolen from Friendfinder’s sites. (Wall Street Journal) 8. 100,000 groups in at least 150 countries and more than 400,000 machines were infected by the Wannacry virus in 2017, at a total cost of around $4 billion. (Technology Inquirer)
- In 2016, Uber reported that hackers stole the information of over 57 million riders and drivers. (Uber) 10. Uber tried to pay off hackers to delete the stolen data of 57 million users and keep the breach quiet. (Bloomberg) 11. In one of the biggest breaches of all time, 3 billion Yahoo accounts were hacked in 2013. (New York Times)
Is there a way to protect yourself from a cyber attack?
- Update your software and operating system
- Use anti-virus software
- Use strong passwords
- don’t open email from unknown email addresses
- avoid risky clicks
- Avoid using unsecure WiFi networks
Today due to high rate of cyber attack, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.

Posted on December 4, 2021
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.