BigCoder
Posted on September 19, 2021

Pass is an open source Unix password manager, safe for personal and professional use.
It has a different user experience than existing password managers because it's a command line program.
It's basically a wrapper on GPG files which are stored in:
~/.password-store
If you have multiple computers, you can sync with git.
But first, let's learn how to use pass. Setup gpg and pass.
How does it work?
First create a GPG key
gpg --full-generate-key
Now you have a GPG key, make sure to back it up!
To show your keys:
gpg --list-secret-keys --keyid-format LONG
Example output, pick the right key
sec 4096R/3AC5C34371567BD2 2019-10-10
uid toto <toto@example.com>
ssb 4096R/42B317FD4BA89E7A 2019-10-10
It's 3AC5C34371567BD2 here.
Install pass
# installation on Arch Linux
sudo pacman -S pass
# installation on Ubuntu
sudo apt install pass
Then create a new password wallet (change to your gpg keys)
pass init 3AC5C34371567BD2
To add a password
pass insert twitter/user
To generate a password of 16 characters
pass generate twitter/bob 16
To show a password
pass get twitter/user
To copy a password to clipboard
pass get -c twitter/user
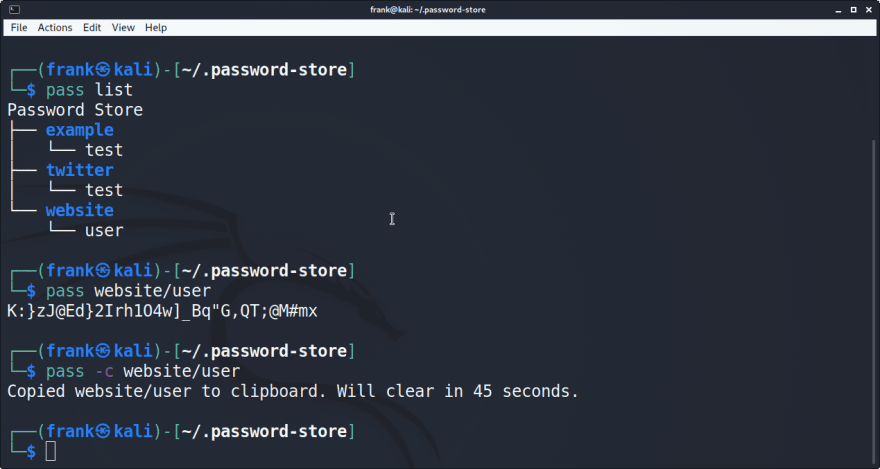
To list all passwords
pass list
Example:
$ pass list
Password Store
├── example
│ └── test
└── twitter
└── test
Weak passwords
It's important to choose strong passwords. That's because there are lists of millions passwords like rockyou.txt which can be used to brute force your Linux system using hydra.
Even a hashed password in /etc/shadow isn't necessary secure. Hashes can be cracked tools using tools like John the Ripper.
If you want to do hash cracking, there's a course here: John the Ripper.
How does it compare to Keepass and friends?
In terms of security the default config is not much stronger than Keepass.
Password managers typically store all passwords on the computer (internet connected device).
The bitcoin madness of last decade has shown that this was not the best idea (several people had private keys stolen).
In my opinion, it's not the most secure idea to store all your passwords on a general purpose computer (reduce attack surface). Especially when exploits for said software show up all the time.
So what's the solution?
You can setup Yubikey with pass and store the private keys on the key itself. This requires quite some setup time.
Alternatively, remember 500+ passwords in your head like me or cope.

Posted on September 19, 2021
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.