Sena Yakut
Posted on April 16, 2023

Amazon CodeWhisperer is an AI code service that provides real-time code suggestions in your Integrated Development Environment (IDE) to help you quickly write your code. On April 13th, Amazon CodeWhisperer is generally available. There are two tiers, Individual and Professional. For the Individual tier, it’s free to use 🧐, and easy to integrate and I recommend enabling this cool service in your IDE if you did not yet. If you’re using the Individual tier, you can get code recommendations, reference tracking, and security scans for your project. You can use Amazon CodeWhisperer with Python, Java, JavaScript, TypeScript, C#, Go, Rust, Kotlin, Scala, Ruby, PHP, SQL, C, C++, and Shell Scripting.
Today, I will show you some code generations example to secure your AWS account easily with this cool code generator. Let’s start together!😵
Setup Your Account
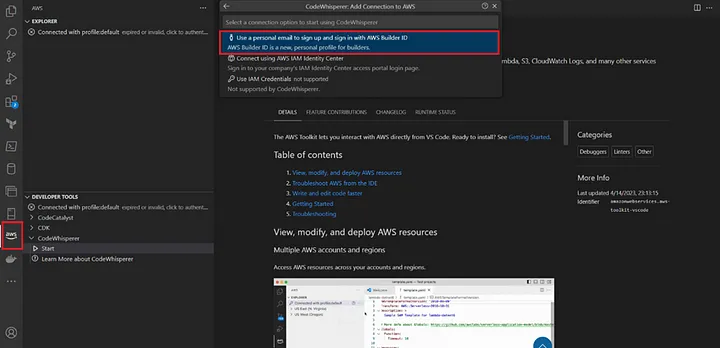
1) I’ll use Visual Studio Code in this blog however, Amazon CodeWhisperer can be integrated with JetBrains, AWS Cloud9, and AWS Lambda. If you don’t have AWS Toolkit in your VSCode, you need to install it in the extensions part. If you already have, you need to be sure it’s up to date.
2) After that, I’m choosing AWS Builder ID connection, it’s also free and you do not need to have an AWS account for this.
3) We will get authorize request panel.
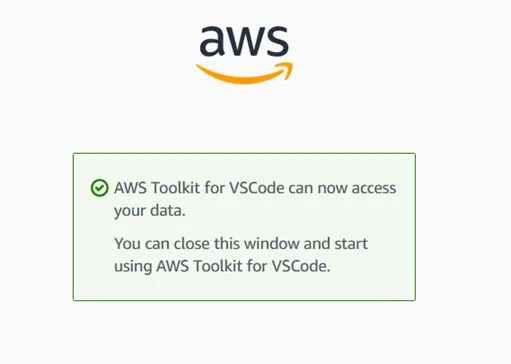
4) And we need to accept AWS Toolkit for VSCode to access our data!
After all steps, you can use Amazon CodeWhisperer suggestions in your IDE. 👻
Use CodeWhisperer as AWS CIS Recommender
The CIS AWS Foundations Benchmark provides lots of security configurations and best practices for our AWS environment. It’s important to know the issue and remediate and automate remediation related to CIS Benchmarks. There are lots of tools, integrations, and scripts for CIS Benchmark and you can use that. But if you do not want to use this, you already do not know the processes on this and you want to get all the control, you can write your own CIS Benchmark controller. For this process, we’re using Amazon CodeWhisperer.
I’ll choose some random controls from CIS Benchmark v1.5.0. You can see all controls from here.
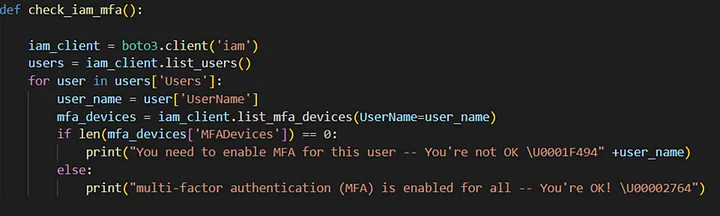
1) Ensure multi-factor authentication (MFA) is enabled for all IAM users
MFA is important for your all accounts. We also check this in our AWS Account. When I say something about this process to Amazon CodeWhisperer, it generates for me.
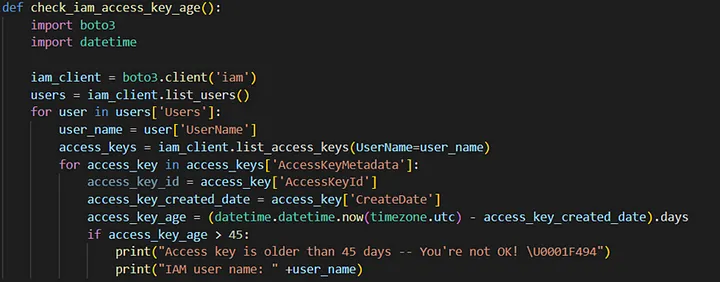
2) You need to check that the AWS IAM user key age is greater than 45 days or not
It is recommended that all credentials that have been unused for 45 or greater days be deactivated or removed. They can be used for bad activities in your account. Let’s try this control.
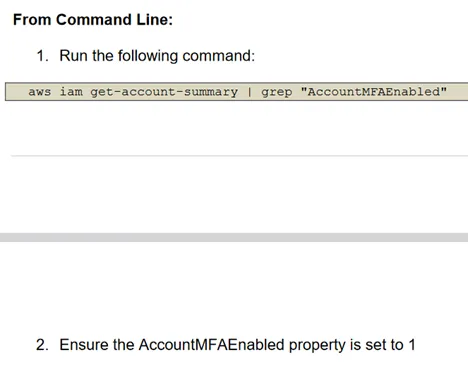
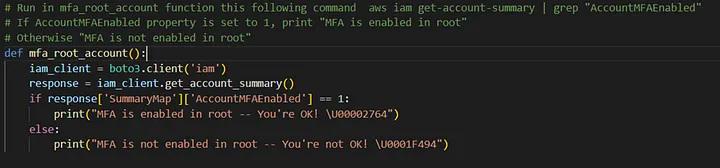
3) MFA should be enabled for the ‘root’ user account
The ‘root’ user account is the most privileged user in an AWS account. It’s so important to enable MFA in this account. I’m writing to VSCode from the AWS CIS Benchmark document.
This is from the CIS Benchmark:
And this is from us:
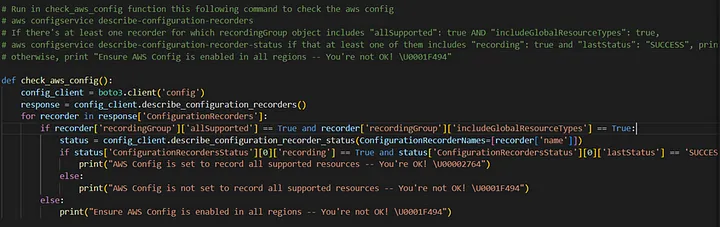
4) Ensure AWS Config is enabled in all regions
AWS Config is a web service that performs configuration management and logging changes. It’s recommended to enable it.
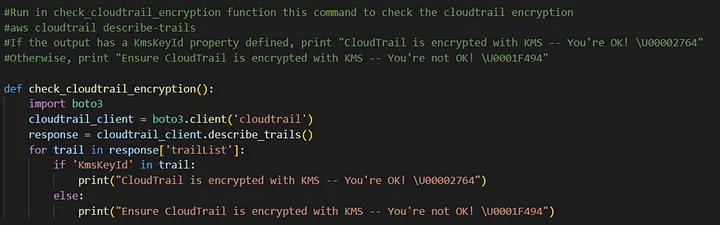
5) Ensure CloudTrail logs are encrypted at rest using KMS CMKs.
We love encryption in AWS. It is recommended that CloudTrail be configured to use SSE-KMS. I’m converting AWS CIS Benchmark controls to a sentence and explain to AWS CodeWhisperer as much as I can.
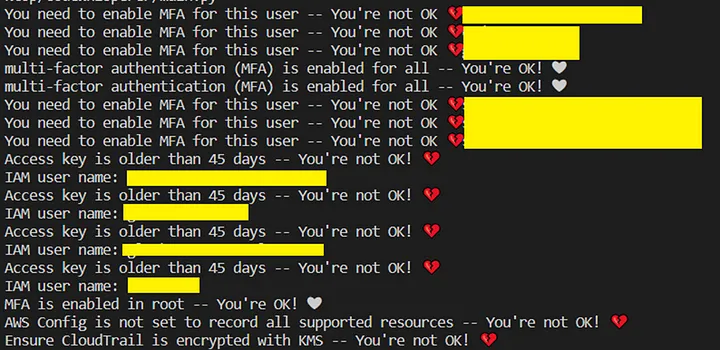
After all of that, let’s run our functions!🙀
Use CodeWhisperer as Code Scanner
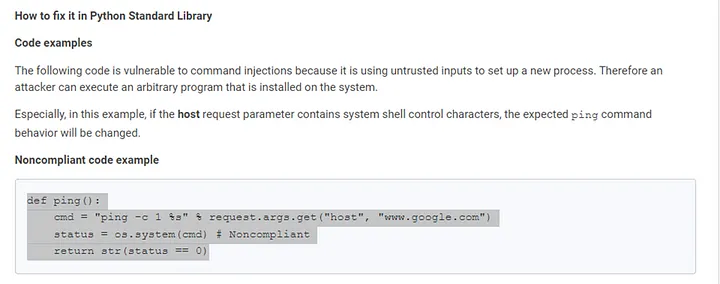
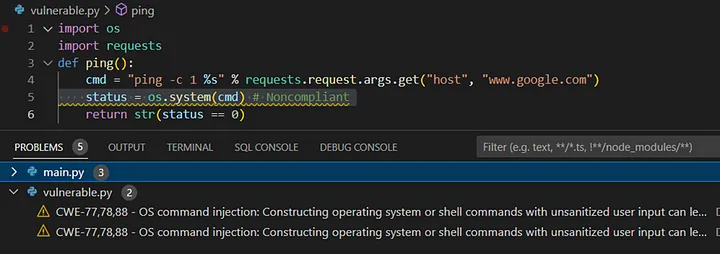
Static code scanning is important in your CI/CD pipeline and DevSecOps processes. After the security scanning is finished with CodeWhisperer, security issues in the scanned files are highlighted in the problems panel. Let’s try this with a vulnerable command injection attack code scenario from SonarQube Library.
We can easily see this issue has been found by AWS CodeWhisperer.
I strongly recommended using the security scan module for your IDE. It finds your security vulnerabilities before you go to 🧠production🧠.
Thanks for reading! Stay safe in the cloud! 🤞 ⛅️

Posted on April 16, 2023
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.