Stay compliant with AWS Step Functions — IAM Users’ Access Key Age Notification

Pubudu Jayawardana
Posted on June 14, 2023

It is a best practice and also, one of the AWS Security Hub controls for IAM to have all the IAM user access keys to be rotated every 90 days.
It might not be an easy task to check each and every user access key to check if they pass this validation.
Lambda is a great tool not only to be part of a Serverless system but also small house keeping tasks like this. In this blog post, I am going to discuss how we can use a simple AWS Step Function to go through all the user access keys in the AWS account and send a notification if there are keys that were created more than 90 days ago.
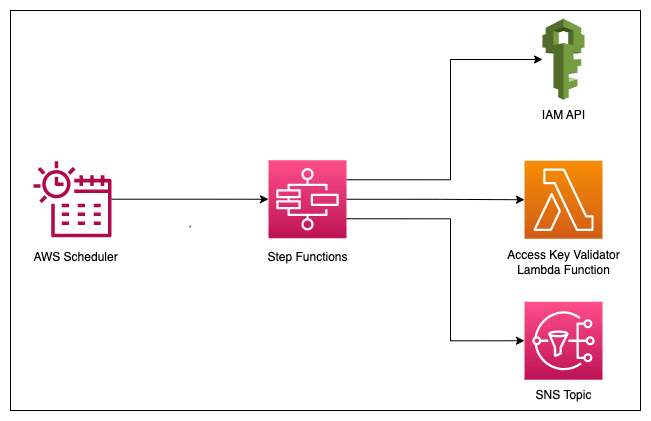
Architecture
State machine
As you see, this is a very simple system with very few components.
- There is an AWS Schedule that runs periodically that initializes a Step Functions execution.
- Within Step Functions execution, first there is a SDK integration to IAM to get all the users available in the AWS account.
- Then, the result is sent to a Distributed Map state to iterate through each and every user.
- Within the Distributed Map state, there is another SDK integration to IAM to get all the access keys for a particular user.
-
ListAccessKeys of IAM will provide the access key details in the below structure:
{ “AccessKeyId”: “AKIXXXXXXXXX”, “CreateDate”: “2021–11–27T20:15:43Z”, “Status”: “Active”, “UserName”: “pubudu” } Once all the Distributed Map iterations are completed, all the results will be sent to the KeyValidationLambda function as input.
Within the KeyValidationLambda function, all the key data are iterated and using the CreatedData, it checks if the particular access key was created 90 days ago.
If there are older access keys, it will be sent back to the SF execution.
In the next step, there is a Choice state where it checks if there are results returned from the Lambda. If so, it sends this data into a SNS Topic via SDK integration. Then it ends the execution.
If there is no result returned from Lambda, SF execution will end successfully.
You can subscribe to the SNS topic in many ways (ex: email, Slack, etc) so you will get notified when a message is published to the topic.
Test this yourself
You can test this solution in your AWS account using AWS SAM with Python. Source code for this project is available at https://github.com/pubudusj/aws-iam-key-checker
Summary
AWS Step Functions SDK integration is very powerful to build not only full scale Serverless functionality but also this kind of automation around security best practices.
At the moment, AWS Step Functions doesn’t support date time related intrinsic functions. When those are available, access key validation checks can be done within the execution which will further reduce the custom code (within the Lambda function).
Useful Links
Step Functions SDK integrations — https://docs.aws.amazon.com/step-functions/latest/dg/supported-services-awssdk.html
AWS Security Hub IAM controls — https://docs.aws.amazon.com/securityhub/latest/userguide/iam-controls.html

Posted on June 14, 2023
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.