
Alejandro Velez
Posted on September 26, 2022

Level 200
Welcome to this series of tutorials and how-to guides about DevSecOps with AWS! This series will coverage some steps, architecture patterns, setups, bests practices and demonstrations to create a multi-environment setup using AWS for deploying applications at enterprise scale.
Suppose that you are a DevSecOps consultant and works for a fiction company “LabXl”, it has multiples applications in mind and based in your searches found that the best way to grow and be global is using the cloud and the final decision was use AWS. You must create the bases, define the best practices and minimum viable products (MVPs) to achieve those objectives.
Let’s begin, the first step is setup the bases for manage multiples application environments, a common practice is to use a sandbox, development, preproduction and production environments. But in AWS, which is the bests practice for this setup? According to AWS Security Reference Architecture (AWS SRA) and AWS Well Architect Framework the bests practice is to split in multiple AWS accounts these environments implementing services such as AWS Control Tower, IAM identity Center (before SSO), AWS Organizations of course there are other services that will be addressedin future publications. For example, the Figure 1 shows a fragment of this setup.

Figure 1. AWS Multi Environment Accounts
Now, you must select the tools and methods for integrate these accounts and govern the deployments, according to the best practices is common to use a central account for deployments, the DevSecOps Account that is showed in the Figure 1, there you’ll create DevSecOps pipelines and user services such as AWS CodeCommit, Amazon CodeGuru, AWS Cloud9, AWS CodeArtifact, AWS CodeDeploy, AWS CodeBuild and AWS CodePipeline.
Whit this in mind the final question is, how can you bootstrap this environment for central deployments? The answer: delegate access across AWS accounts using IAM roles, you can do the process manually but this will be a repetitive task, so the best way is using Infrastructure as Code (IaC), there are many tools for example, AWS Cloudformation, Terraform, Pulumi, SDKs, AWS CLI and AWS Cloud Development Kit (CDK), each one has advantages and disadvantages but for this case and future deployments a secure and faster way is using CDK and AWS Cloud Shell.
Hands On
Requirements
- cdk >= 2.43.0
- AWS CLI >= 2.7.0
AWS Services
- AWS Cloud Development Kit (CDK): is an open-source software development framework to define your cloud application resources using familiar programming languages.
- AWS CloudShell: is a browser-based shell that makes it easy to securely manage, explore, and interact with your AWS resources.
- AWS Identity and Access Management (IAM): Securely manage identities and access to AWS services and resources.
Solution Overview

Figure 2. Solution Overview- Steps for bootstrapping Multi Environments
The Figure 2 shows the steps to accomplish this task.
1- You must login whit SSO credentials via web browser.
2- Select the profile and account to create trust relationships.
3- Open AWS CloudShell and run CDK commands.
4- Setup AWS CLI profile using aws configure command for DevSecOps Account.
5- Create CDK projects and deploy it.
Step by step
The Figure 3 shows the steps 1, 2 , 3.

Figure 3. Login into cloud shell using AWS SSO
The next step is created an initial CDK project, in future post you can find more information about this tool.
Update cdk version.
[cloudshell-user@ip-10-1-48-231 ~]$ sudo npm install -g aws-cdk
[cloudshell-user@ip-10-1-48-231 ~]$ cdk --version
2.43.1 (build c1ebb85)
Create project
[cloudshell-user@ip-10-1-48-231 ~]$ mkdir cdk_init_project
[cloudshell-user@ip-10-1-48-231 ~]$ cd cdk_init_project/
[cloudshell-user@ip-10-1-48-231 cdk_init_project]$ cdk init --language python
Active environment and install dependencies
[cloudshell-user@ip-10-1-48-231 cdk_init_project]$ source .venv/bin/activate
(.venv) [cloudshell-user@ip-10-1-48-231 cdk_init_project]$ pip install -r requirements.txt
Collecting aws-cdk-lib==2.43.1
Downloading aws_cdk_lib-2.43.1-py3-none-any.whl (62.0 MB)
|████████████████████████████████| 62.0 MB 2.1 MB/s
Collecting constructs<11.0.0,>=10.0.0
Downloading constructs-10.1.111-py3-none-any.whl (56 kB)
|████████████████████████████████| 56 kB 6.0 MB/s
Collecting typeguard~=2.13.3
Downloading typeguard-2.13.3-py3-none-any.whl (17 kB)
Collecting publication>=0.0.3
Downloading publication-0.0.3-py2.py3-none-any.whl (7.7 kB)
Collecting jsii<2.0.0,>=1.68.0
Downloading jsii-1.68.0-py3-none-any.whl (554 kB)
|████████████████████████████████| 554 kB 53.7 MB/s
Collecting python-dateutil
Downloading python_dateutil-2.8.2-py2.py3-none-any.whl (247 kB)
|████████████████████████████████| 247 kB 51.3 MB/s
Collecting typing-extensions<5.0,>=3.7
Downloading typing_extensions-4.3.0-py3-none-any.whl (25 kB)
Collecting attrs<23.0,>=21.2
Downloading attrs-22.1.0-py2.py3-none-any.whl (58 kB)
|████████████████████████████████| 58 kB 6.8 MB/s
Collecting cattrs<22.2,>=1.8
Downloading cattrs-22.1.0-py3-none-any.whl (33 kB)
Collecting six>=1.5
Downloading six-1.16.0-py2.py3-none-any.whl (11 kB)
Collecting exceptiongroup; python_version <= "3.10"
Downloading exceptiongroup-1.0.0rc9-py3-none-any.whl (12 kB)
Installing collected packages: typeguard, publication, six, python-dateutil, typing-extensions, attrs, exceptiongroup, cattrs, jsii, constructs, aws-cdk-lib
Successfully installed attrs-22.1.0 aws-cdk-lib-2.43.1 cattrs-22.1.0 constructs-10.1.111 exceptiongroup-1.0.0rc9 jsii-1.68.0 publication-0.0.3 python-dateutil-2.8.2 six-1.16.0 typeguard-2.13.3 typing-extensions-4.3.0
WARNING: You are using pip version 20.1.1; however, version 22.2.2 is available.
You should consider upgrading via the '/home/cloudshell-user/cdk_init_project/.venv/bin/python3 -m pip install --upgrade pip' command.
(.venv) [cloudshell-user@ip-10-1-48-231 cdk_init_project]$
Finally, run cdk bootstrap command with trust option and pass administrator access policy for cloudformation execution when trusted account will run deployments.
cdk bootstrap --trust 123456789012 --cloudformation-execution-policies arn:aws:iam::aws:policy/AdministratorAccess
⏳ Bootstrapping environment aws:// 123456789014/us-west-2...
Trusted accounts for deployment: 123456789012
Trusted accounts for lookup: (none)
Execution policies: arn:aws:iam::aws:policy/AdministratorAccess
CDKToolkit: creating CloudFormation changeset...
✅ Environment aws://123456789014/us-west-2 bootstrapped.
This command creates all resources necessary for CDK deployments using a centralized account. Finally, You should watch something like this.
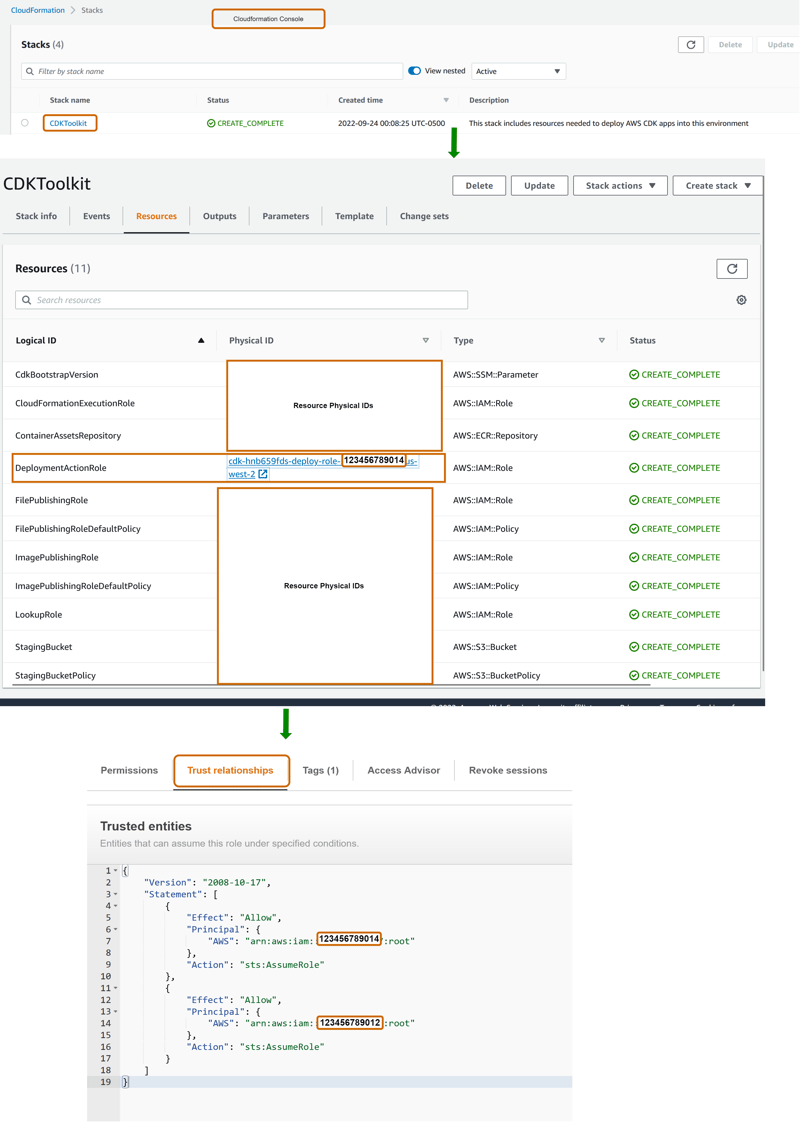
Figure 3. MultiEnvironment Accounts steps verify
Repeat the steps for other accounts.
In the next post of this series, you can verify the deployment using unique credentials and central account.
Thanks for reading!

Posted on September 26, 2022
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.