Sena Yakut
Posted on December 2, 2023

AWS re:Invent 2023 is completed in Las Vegas. I’ve watched some security-focused sessions and announcements online and I want to share my notes with you. I hope you will enjoy it! Let’s start! 🥰
🧐 Sessions that I’ve recommended:
💁♀️ Move fast, stay secure: Strategies for the future of security (SEC237):
In this innovation talk, we start with “Security is a people issue. Computers do not attack each other.”
- Security operations like playing chess, we need to predict the attackers’ actions. In this game, technology and humans are together.
- Human and AI. We need both of them for better security. AI increases work efficiency, but we still need people to decide. AI cannot decide. We need talented engineers to decide.
- In the cybersecurity area, we have a talent gap. Security knowledge is not enough, we need engineers who understand the organizational logic of the company. With the AI popularity, we have lots of concerns and lots of to-dos as security professionals. You should ask yourself and your environment if you’re building your app with AI or build AI: “Where is my data?”, “What happens with my query and any associated data?”, “Is the output of these models accurate enough?” From AWS's perspective = “Your data is your data.”
💁♀️ Elevate your security investigations using generative AI (SEC244):
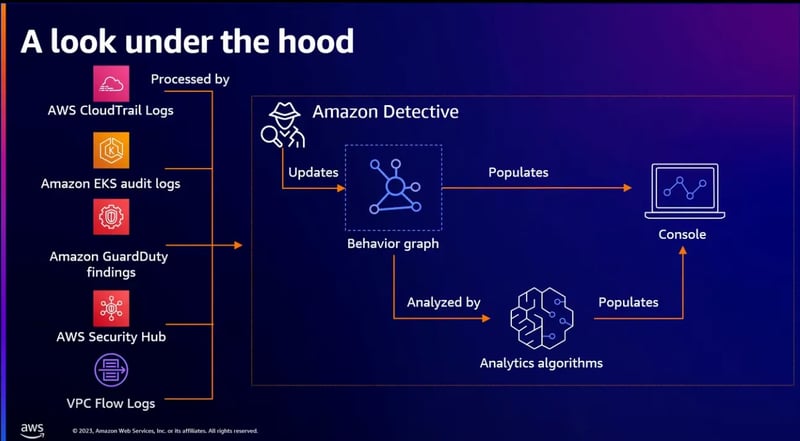
In this session, we learn about Amazon Detective and the newest announcements. There are 3 different challenges in security investigations and we can solve them with Amazon Detective:
- Analysts cannot review every high-priority security issue.
- Shortage of skilled security professionals.
- Increasing cost and complexity with investigating potential security findings.
Amazon Detective collects security logs from different services and analyzes them with different ML algorithms.
- We have a new feature called “Finding Group Summary”. With this feature, the findings are summarized with correlated behaviors and are more understandable.
- Another one is integration with Security Lake for root cause analysis. Amazon Detective uses the prepared queries or tunes them to meet the specific security needs of any investigation.
In the session, we also have an example scenario that we can analyze with Detective. It helps us to understand the use cases and new features in detail.

If you want to use Amazon Detective for your workloads, this is the pricing.
💁♀️ Amazon S3 security and access control best practices (STG315):
In this session, I felt like I was taking a security specialty exam course, and liked it. We saw lots of different usages of different approaches to secure our S3 buckets.
- Firstly, we should know AWS S3 is secure by default: Encryption (SSE-S3) by default, S3 blocks public access enabled by default, and S3 ACLs are disabled by default. In the S3 access management process, it’s important to understand IAM (obviously), bucket policies, and conditions.
- For access management, AWS recommends not using ACLs anymore. If you want to track your ACL usage, you can use S3 Inventory reports, CloudTrail, and S3 access logs.

- For encryption, AWS has different options for our objects. This cool table summarizes it. You can choose the best option for your regulatory and security needs.

- If you have strict regulatory needs about your data, consider dual-layer server-side encryption. All details are here.
- If you want to decrease your costs of encryption/decryption processes, you can use S3 bucket keys. The logic is simple here: In the first request, we’re going to request to KMS, in Nth requests, we’re going to S3 bucket keys that are time-limited within Amazon S3. It also works with multi-tenant environments.

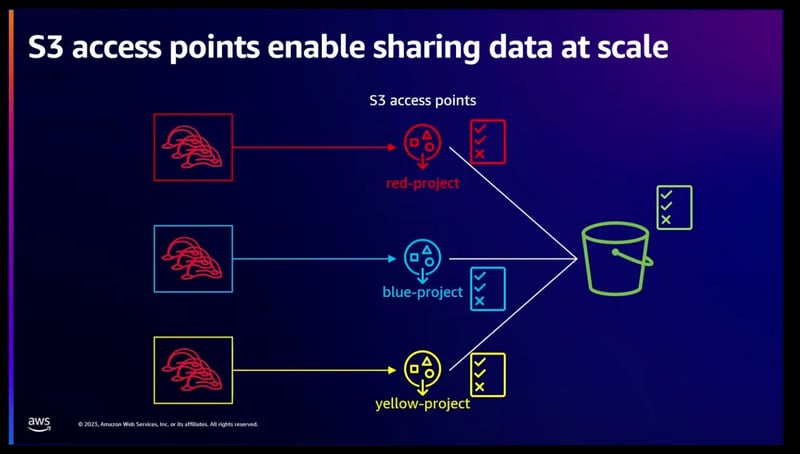
- If you want to simplify the security management for S3, you can use S3 access points. Each S3 access point has its own DNS name and point policy.
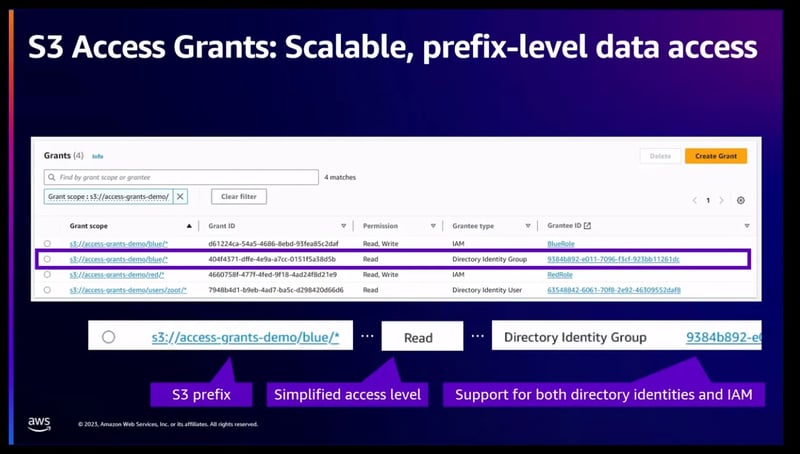
 NEW: S3 Access Grants: And wow, we have a new access control mechanism. You can define granular access to your Amazon S3 data based on applications, personas, groups, or organizational units.
NEW: S3 Access Grants: And wow, we have a new access control mechanism. You can define granular access to your Amazon S3 data based on applications, personas, groups, or organizational units.
💁♀ ️Governance and security with infrastructure as code (DOP209):
This is a developer-focused talk. We can learn how to catch issues early with cdk-nag, validate your pipelines with cfn-guard, and protect your accounts from unintended changes with CloudFormation hooks.

💁♀️ Safeguarding infrastructure from DDoS attacks with AWS edge services (NET201):
Interesting session about DDoS attacks and mitigation tactics.
💁♀ ️Streamlining security investigations with Amazon Security Lake (SEC234):
We heard about Amazon Security Lake in re: Invent 2022. In this session, we will gain visibility for comprehensive security investigations and swift incident responses in hybrid environments.
💁♀ Centralize user activity from external sources in AWS CloudTrail Lake (COP341):
This is a quick demo session and I like it. We will learn how we can use AWS CloudTrail Lake to centralize user activity from external sources in one place.
🧐 Announcements that I’ve noted:
- Integrating Amazon Inspector scans into your CI/CD pipeline: You can use Amazon Inspector as your scanner for your images. It’s an important update for DevSecOps.
- IAM Access Analyzer now simplifies inspecting unused access to guide you toward the least privilege: We love the “at least privilege principle”. As you know, it’s hard to provide an audit of this in all AWS accounts. AWS IAM Access Analyzer now simplifies inspecting unused access. Note: Please read the pricing guide before you start to use this.
- Amazon Inspector agentless vulnerability assessments for EC2 (preview): Amazon Inspector now offers continuous monitoring of your Amazon EC2 instances for software vulnerabilities without installing an agent or additional software. You can use this feature within the hybrid mode.
- Introducing Amazon GuardDuty ECS Runtime Monitoring, including AWS Fargate: Your first to-do in an AWS account, enable GuardDuty. In containerized environments, it’s important to add threat intelligence for it. AWS announces Amazon GuardDuty ECS Runtime Monitoring, an expansion of Amazon GuardDuty that introduces runtime threat detection for Amazon ECS workloads — including serverless container workloads running on AWS Fargate.
- Amazon Inspector expands AWS Lambda code scanning with generative AI-powered remediation: For the reducing time to fix it’s an important update. AWS includes assisted code remediation using generative AI and automated reasoning to Amazon Inspector. Note: I’ve tested this feature and got some errors about it. I’ll reach out to the support team.
- AWS Config launches generative AI-powered natural language querying (preview): We can ask questions like: “Show me all non-compliant S3 buckets in my organization.” It simplifies the investigation and search of AWS resource configurations and changes for our resources.
- AWS announces CloudWatch Logs Anomaly Detection and Pattern Analysis: Anomaly detection is important for our production workloads. Using these new features, we can identify unusual events, and use these accelerate our investigation.
- Amazon Detective announces investigations for IAM: Amazon Detective provides an investigation of AWS IAM entities for anomalies. This new capability helps us determine whether IAM entities have potentially been compromised or involved in any known scenarios.
- You can now customize security controls in AWS Security Hub: We always need customization based on our environments for security posture management. With custom control parameters, Security Hub evaluates the control against the value that we specify. There are some customization examples from AWS:
*[CloudWatch.16] — CloudWatch log groups should be retained for a specified period: You can specify the retention period.
*[IAM.7] — Password policies for IAM users should have strong configurations: You can specify parameters related to password strength
*[EC2.18] — Security groups should only allow unrestricted incoming traffic for authorized ports: You can specify which ports are authorized to permit unrestricted incoming traffic.
*[Lambda.5] — VPC Lambda functions should operate in multiple Availability Zones: You can specify the minimum number of Availability Zones that produce a passed finding.
- Amazon CodeWhisperer offers new AI-powered code remediation, IaC support, and integration with Visual Studio: We love the shift left principle as DevSecOps engineers and security professionals. With an AI-powered code remediation feature, it provides generative AI-powered code suggestions to help remediate identified security and code quality issues. Fix before exist.
Thanks for reading! Stay secure in the cloud! 🌤

Posted on December 2, 2023
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.